by Bhabesh Rai, Associate Security Analytics Engineer, LogPoint
On July 1, 2020, BIP-IP released security updates for a remote code execution vulnerability found in undisclosed pages of the Traffic Management User Interface (TMUI) of the BIG-IP application delivery controller (ADC).
Critical TMUI RCE vulnerability
An F5 vulnerability, tracked as CVE-2020-5902, could allow attackers to take full control over unpatched systems that are accessible on the internet. The core of the vulnerability lies in a path traversal flaw that leads to an authentication bypass. Unauthenticated attackers or authenticated users with network access to the TMUI, through the BIG-IP management port and/or Self IPs, can execute arbitrary system commands, create or delete files, disable services, and/or execute arbitrary Java code. Affected versions of BIG-IP are 15.0.0-15.1.0.3, 14.1.0-14.1.2.5, 13.1.0-13.1.3.3, 12.1.0-12.1.5.1, and 11.6.1-11.6.5.1.
The vulnerability has a CVSSv3 score of 10 (Critical) and exploits a lack of proper access control for the TMUI configuration utility for the devices. If deployed correctly, the management interface shouldn’t be exposed to the internet, but Bad Packets found a total of 1,832 unique IPv4 hosts worldwide vulnerable to CVE-2020-5902.
Bad Packets has detected opportunistic mass scanning and exploit activity targeting F5 BIG-IP servers vulnerable to CVE-2020-5902. Researcher Rich Warren from NCC Group first reported the exploitation attempts coming from Italy. The attackers were attempting to read files and extract encrypted passwords. Twitter user @x4ce was the first to submit the PoC for RCE in his tweet on July 5, 2020. There is also a pull request submitted for a Metasploit exploit. It is strongly recommended to upgrade BIG-IP to version 15.1.0.4, 14.1.2.6, 13.1.3.4, 12.1.5.2, or 11.6.5.2 to fix the vulnerability.
Detection using LogPoint
The following query will detect all the exploitation attempts for CVE-2020-5902.
norm_id=* request_method=GET (resource="*/..;/tmui/*" OR url="*/..;/tmui/*")
An alert is also available in LogPoint for the exploitation attempt of the CVE.
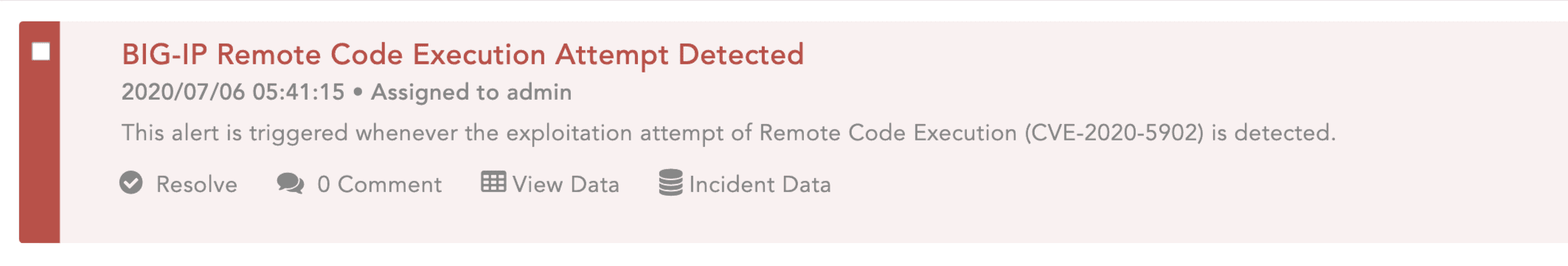
Although temporary mitigations are available, the F5 advisory recommends upgrading to a fixed software version to fully mitigate the vulnerability. If you have updated your device or applied the workaround then the following query will detect any unsuccessful exploitation attempts.
norm_id=* request_method=GET (resource="*/..;/tmui/*" OR url="*/..;/tmui/*") status_code=404
Attackers are still actively probing for endpoints vulnerable to recent Pulse Secure and Citrix CVEs. BIG-IP is also at risk for increased attack activity due to its criticality and use in critical infrastructures worldwide, which makes it a prime target for adversaries ranging from ransomware groups to APTs.