By Ivan Vinogradov, Solution Architect, LogPoint
During times of crisis, hackers take every opportunity to attack and exploit overwhelmed organizations. Users should take the obvious immediate steps to keep safe, like avoiding links in unknown emails, using strong passwords and only connecting to secure WiFi. But there are important steps to take at the infrastructure and policy level to reduce risk and enhance cybersecurity. Here are the key actions for the administrator in a time of crisis.
Always use encryption
Some form of encryption is a staple of almost any modern technical security control, and rightfully so. However, its application is often inconsistent – a problem that may increase risk during a time when non-technical controls are less viable.
Reinforce VPN policies
The use of a virtual private network (VPN) is commonly seen as an item of utility rather than an overarching policy. Enterprises with immature security policies tend to use it to access certain internal services, but not all of them. When used inconsistently, data exchange often takes place outside the encrypted confines of a VPN. With more employees working from home, it’s a good opportunity to create or reinforce a VPN policy that routes most, if not all corporate traffic, through an encrypted tunnel.
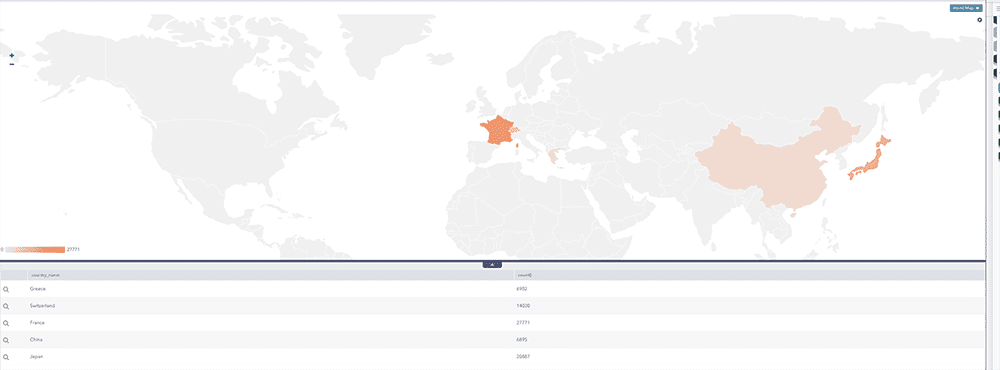
In LogPoint, you can see a visual overview of VPN traffic by geographic location to ensure there is no abnormal traffic.
Data encryption at rest especially important now
It’s a good idea for all organizations, especially those with a highly mobile or remote workforce, to encrypt data at rest. Encrypting data at rest basically converts sensitive data into another form of data only accessible by authorized personnel in order to keep data secure.
Encrypting data at rest has become a necessity during the COVID-19 crisis where physical control over a device is not possible and an overview of the device data might not be readily available. We recommend that companies enforce laptop and mobile device encryption through all levels of organization. It need not be complex. A basic offering like Microsoft’s BitLocker will suffice to deter most malicious actors that end up in possession of a corporate device.
Apply endpoint controls to devices within and outside the network
It is standard practice in most enterprises to install some form of centralized management agent on devices to maintain an overview of the environment, as well as to implement technical controls. It becomes even more important to maintain an overview of devices when employees are working remotely. Mobile device management (MDM) is software that IT departments use to monitor, manage and secure employees’ mobile devices. MDM can be a helpful tool to ensure security of devices while employees are working remotely outside the office network.
Get an overview of device activity
As a device leaves the network, it is immediately much more difficult for companies to get transparency about the device’s activity. With MDM, devices often generate their own data as part of the default functionality. Combining MDM solutions with monitoring data, such as logs, helps companies maintain an overview of device activity even when devices are off premises.
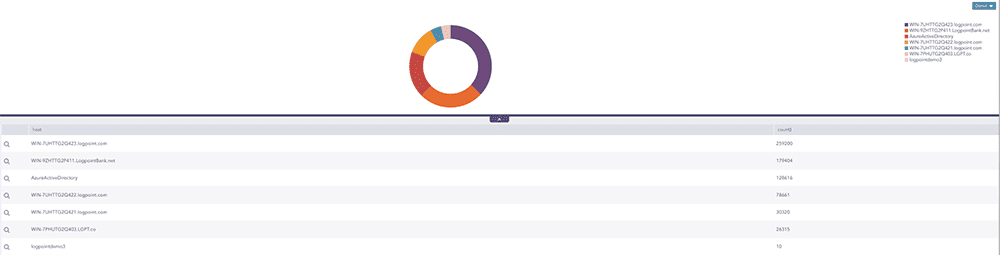
In LogPoint, you can get an overview of device activity, such as seeing how many remote logins were successful and how many failed.
Monitor hardware to detect breaches
Hardware monitoring and use restriction are practical ways to keep devices secure when employees are working from home. Hardware monitoring can help pinpoint the start and cause of a breach when attackers use the device to as an entry point to the network. Furthermore, hardware monitoring can help detect when employees are using hardware to engage in unsanctioned activities, such as moving files between their personal and work devices.
Apply application restrictions
Once an employee is outside the network, typical technologies that seek to limit dangerous and potentially unproductive activity, such as application filtering and DNS blocking, are no longer helpful. Companies can help maintain security by enforcing application restrictions and only allowing employees to deploy certain applications on their workstations. Application restrictions can also help prevent inadvertent security-compromising behavior, such as accessing compromised IPs or using software that is vulnerable, not licensed or non-compliant.
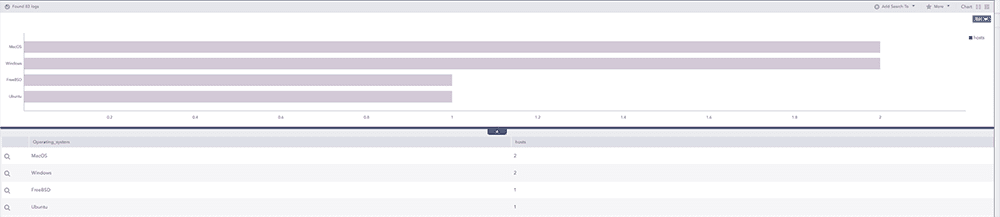
In LogPoint you can get an overview of application use, for example most used operating systems, to help detect security-compromising behavior.