A new ransomware outbreak named “Petya”, similar to the WannaCry malware was seen on June 27, 2017. This malware spread quickly and affected various organizations in Europe and the US. The ransomware was thought to be a variant of Petya family but researchers determined that they are not related and has now been renamed to “NotPetya”.
Petya/NotPetya does not require the EternalBlue SMB vulnerability for exploitation to spread in the systems of a network. One infected host will allow ransomware to spread in any connected systems, provided that the infected system has SMB credentials. So, unlike WannaCry, patching SMB and disabling SMBv1 will not prevent the spread.
Detection of compromise
The LogPoint administrator may search for various indicators of compromise.
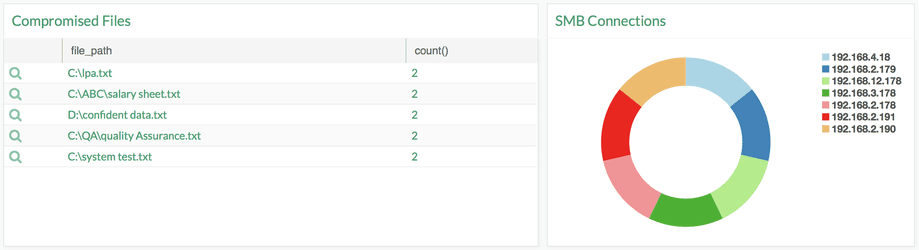
1. Check for file integrity. Possible indicators of compromise are hash values listed below:
- 34f917aaba5684fbe56d3c57d48ef2a1aa7cf06d
- 9717cfdc2d023812dbc84a941674eb23a2a8ef06
- 38e2855e11e353cedf9a8a4f2f2747f1c5c07fcf
- 56c03d8e43f50568741704aee482704a4f5005ad
2. If command-line logging is available, check for various commands listed below
- Scheduled Reboot Task: Petya schedules a reboot
-
- schtasks /Create /SC once /TN “” /TR “\shutdown.exe /r /f” /ST
- cmd.exe /c schtasks /RU “SYSTEM” /Create /SC once /TN “” /TR “C:\Windows\system32\shutdown.exe /r /f” /ST
- This can be searched by looking at event_id=106 and event source=Task Scheduler Service
- Lateral Movement (Remote WMI): Process call create
- \”C:\Windows\System32\rundll32.exe \”C:\Windows\perfc.dat\” #1
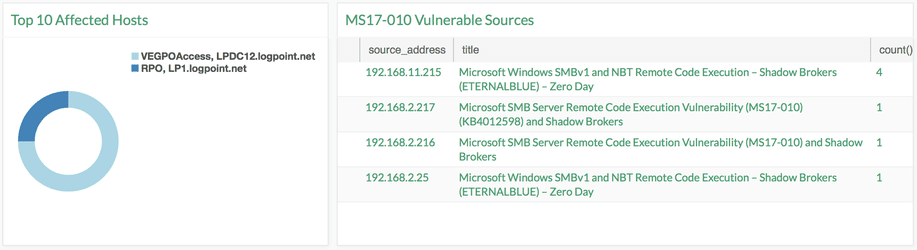
3. Possible Compromise of Network can be detected by looking at servers and workstation scanning tcp port 139 and 445
4. Vulnerability Scan: EternalBlue exploits (MS17-010 Vulnerability) are still applicable and this can be an indicator of compromise.
More information?
If you want to know more about Petya/NotPetya, read this article on our Help Center or contact us via the form on our contact page.