By Jon Gisli Egilsson, Engineering Manager, LogPoint
The amount of cyberattacks continues to rise but the cybersecurity industry has a fundamental challenge finding people with cybersecurity skills to match the demand. Globally, there are more than 3.5 million unfilled cybersecurity positions revealing just how big the challenge is.
The size of the problem suggests that it is unlikely to go away any time soon. Organizations must learn to live with the challenge and still manage their cyber security well enough to withstand the increasing threat of cyberattacks. The key to that is to accelerate cyber efficiency and minimize the need for human resources through machine learning.
The cyber defense challenge rethought
Part of the security analyst’s job is to program cybersecurity tools to detect known indicators of compromise in a system or network. The problem is that hackers continue to find new exploits and methods to compromise, and so the list of indicators of compromise continues to grow. The hackers are two steps ahead of the analysts, and the analysts are always chasing the expansion of methods.
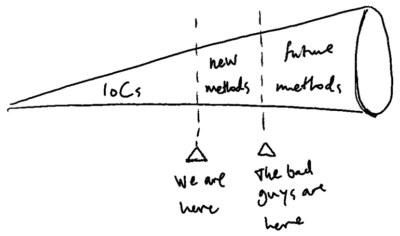
Security analysts work with indicators of compromise, but hackers continue to find new methods
Machine learning can automate and expand the threat detection. Modeling the behavior of users and technical entities in the IT landscape provides capabilities to detect anomalies leading up to or during the attack. Not all companies or departments behave the same. An anomalous behavior in one company might be a normal behavior in another. Machine learning can help detect different baselines between different groups and introduces contextual information, improving the incident response.
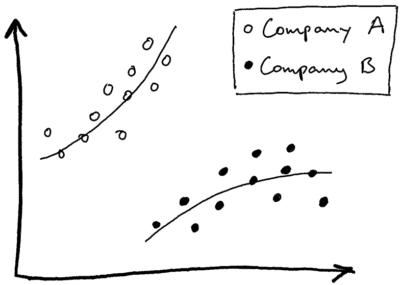
Anomalous behavior in company A, might not be anomalous behavior in company B
Augmenting the security analyst
Machine learning systems might not be as general or flexible as humans, but they can be trained to be more accurate than humans at certain tasks. They can also analyze complete data sets, instead of relying on sampling methods, which often is necessary for a human. Finally, they can analyze complex data, high-dimensional data, and complex edge cases. Humans would have to do visualizations and data pivoting and it would be necessary to map it down to low dimensions due to the huge number of combinations.
Machine learning augments security analysts and carries out some of their normal tasks. In doing so, analysts can focus their efforts on situations in which machine learning cannot be applied – not yet at least. For example, general hardening of the security posture, reviewing architecture and infrastructure, responding to attacks, and investigations.
The data-centric approach gives the strongest outcome
It is important to be mindful of the approach to machine learning. The model-centric approach has been more widely used but a data-centric approach yields better results. Whereas the model-centric approach is focused on building complex models, the data-centric approach is focusing on qualifying the data set.
Machine learning might sound complex and like something that is hard to implement, but it does not have to be, if you ensure data governance and data quality. CISOs contemplating machine learning security, should consider some internal and external aspects before making the decision:
- Internal aspects: Is there enough data? Is the data quality good enough? Is there the right data at the right velocity or intervals? Is the IT organization mature enough?
- External aspect: What is the accuracy of the machine learning solution? How is it tested? How is it ensured?
Machine learning security in practice
The LogPoint UEBA solution can detect behavioral anomalies. A simple example: it can detect if an employee signs in or works at an anomalous hour of the day compared to normal. Different individuals have different patterns, and UEBA learns this context from data. It is not something that an analyst has programmed into the detection system. It is something that the system infers from past behavior.
LogPoint UEBA detects unusual behavior, making it the ideal tool for detecting account compromise, which gives security analysts the opportunity to stop unauthorized account usage by anyone other than the account holder. This way security analysts will be warned about executives getting spearfished by outsiders attempting to infiltrate the organization. The UEBA technology can also do internal reconnaissaince by gathering evidence on network resource and letting analysts know if any of them is behaving differently than expected.
If you are interested in learning more about UEBA, you can read our blogpost about it here.