When Zero Day Meets Ransomware: CVE-2023-28252 and Nokoyawa Ransomware
Microsoft has addressed a critical zero-day vulnerability actively exploited in the wild and has released a patch. Microsoft tagged the exploit as CVE-2023-28252 and named it – “Windows Common Log File System Driver Elevation of Privilege Vulnerability”.
CVE-2023-28252 is a privilege escalation vulnerability, an attacker with access to the system and enough ability to run code can successfully exploit to acquire SYSTEM privileges – the highest user privilege level in Windows.
The exploit has come to the limelight through Nokoyawa’s active profiteering through it, as detected and reported by Kaspersky Technologies.

In this blog post, we dive deeper into the exploit and its usage by ransomware groups. We also try to look at how individuals and organizations can ensure that they are taking the necessary steps to protect themselves from zero-day attacks, all the while providing you with the information you need to stay ahead of the curve in an ever-evolving cybersecurity landscape.
Dive-in
Kaspersky has disclosed that the CVE-2023-28252 is an out-of-bounds write (increment) vulnerability, exploited when the system attempts to extend the metadata block. The exploit allows for the alteration of the base log file in return forcing the system to treat a bogus element of the base log file as a real one.
It does so by changing the offset value pointing to a particular Common Log File System (CLFS) structure in the memory, into an offset pointing towards a maliciously crafted structure. This offers a pointer to a controlled memory at a user level and obtains kernel read/write privileges with it. CLFS structures are part of the CLFS general-purpose logging system used by Windows operating systems that consists of physical log files, log streams, log records and more.
We shall update the blog, once further details are available on the vulnerability.
Criticality Level
| CVE | CVSSv3 Score |
|---|---|
| CVE-2023-28252 | 7.8 |
Severity: High (Important)
Current situation: Exploited in the wild
Should I be concerned?
The answer to that question would be - Yes.
CVE-2023-28252 affects all supported versions of Windows servers and clients, including Windows 11; enabling even the local attackers to potentially exploit the vulnerability without any need for user interaction and with relatively simple attack methods.
Further, CISA has even enlisted CVE-2023-28252 to its catalog of Known Exploited Vulnerabilities, clearly stating the Federal Civilian Executive Branch (FCEB) agencies to get patched or secure their systems by the first week of May.
Affected Products:
-
Windows Server 2022
-
Windows 11
-
Windows Server 2019
-
Windows 10
-
Windows Server 2016
-
Windows Server 2012
-
Windows Server 2008 R2
-
Windows Server 2008
Nokoyawa ransomware’s approach to CVE-2023-28252
According to Kaspersky Technologies, back in February, Nokoyawa ransomware attacks were found to exploit CVE-2023-28252 for the elevation of privilege on Microsoft Windows servers belonging to small & medium-sized enterprises.
Nokoyawa ransomware emerged in March 2022 as a 64-bit Windows ransomware family sharing striking similarities in their attack chain with Hive, one of the most notorious ransomware families of 2021. The initial version of the ransomware was developed in C programming language while the later ones are in Rust using Elliptic Curve Cryptography (ECC) with Curve25519 and Salsa20 for file encryption and require command-line arguments.
Attack Chain
Given its similarities with Hive, it is likely that, Nokoyawa threat actors gain initial access into the target system through phishing with malicious attachments [T1566], leaked/compromised credentials [T1078], and more.
Once in the system with the ability to run code, the zero-day CVE-2023-28252 is exploited for privilege escalation with the main purpose of dumping [T1003] the contents of the HKEY_LOCAL_MACHINE\SAM registry hive.
As for command and control and lateral movement in the target network, obfuscated codes [T1027] that are part of the Cobalt Strike beaconing technique are executed, with loaders to prevent AV detection.
As soon as the attackers assure that the entire network has been compromised and necessary organizational data has been exfiltrated, the final payload i.e. Nokoyawa ransomware is delivered and the encryption process initiates. Once complete, a message pops up notifying the users about the incident that occurred in their system, a URL link to Nokoyawa’s .onion/ portal to chat with the “Support”, and guidelines as a warning.
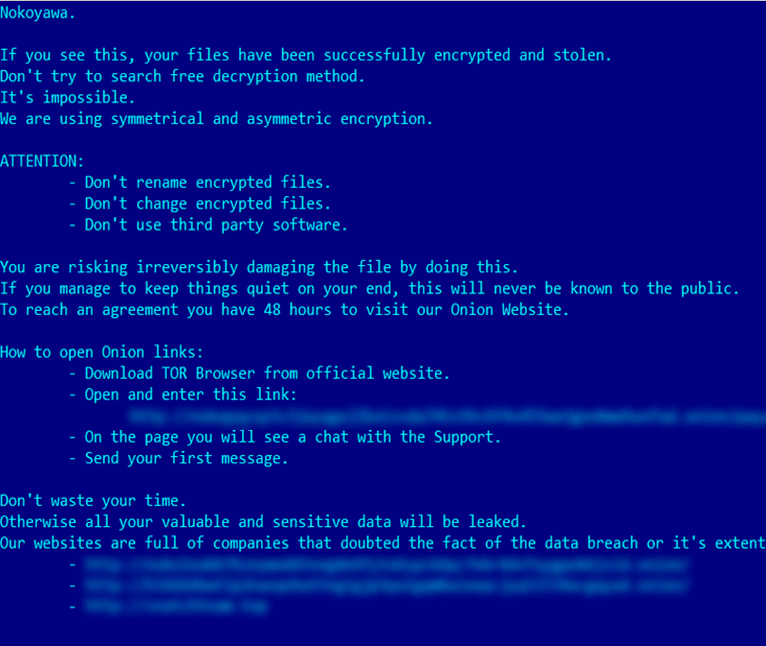
Nokoyawa ransom note (Kaspersky Technologies)
Detection of CVE-2023-28252 exploit by Nokoyawa using Logpoint
Patching an organizational infrastructure takes time, and therefore, it is important to look for indicators of attack and detect any traces of exploitation attempts or intrusion.
Using Logpoint Converged SIEM with a few queries can be the tool in your arsenal for the grand act.
Log Source Needed
-
Windows
-
Windows Sysmon
-
Process Creation with Command Line Auditing explicitly enabled
-
Registry Auditing explicitly enabled
As the CVE-2023-28252 is exploited to dump the contents of the HKEY_LOCAL_MACHINE\SAM registry hive, we can be on the look-out for the same,
NOTE: To generate such events Registry auditing should be enabled for the registry key.
Also, we can actively search for the relevant hash of the exploit,
Towards the end, exploitation files are left behind in the “C:\Users\Public\” folder that can be detected with,
Next, Cobalt Strike beaconing technique is used for execution and maintaining persistence in the system. Detection for Cobalt Strike leveraged by the Hive actors has been published and reviewed time and again in our “How to detect stealthy Cobalt Strike activity in your enterprise“ blog.
Sysmon, if deployed and correctly configured in the environment, allows us to detect Cobalt Strike’s default named pipes.
The creation of the Sysmon remote thread logs aids in detecting Cobalt Strike’s process injection activity.
With these, you can be able to detect and act to disrupt the chain of infection, preventing further damage to the system.
Incident response with Logpoint SOAR and AgentX
Logpoint not only offers detection but also has a strong response module i.e. SOAR. AgentX, our native endpoint agent, adds EDR capabilities to Converged SIEM and comes with built-in telemetry that enriches SOAR events, allowing for automated and timely responses to security incidents and therefore reducing the scope of impact.
Logpoint AgentX is available now: Contact your representative.
The analyst or administrator can utilize the Block Indicators playbook to check if any IP, domain, URL, or host exists in a list of IoCs, block them, and add them to the blocked list preventing damage to the system.
As mentioned above, the Nokoyawa threat actors have been found dumping the contents of the HKEY_LOCAL_MACHINE\SAM registry hive for password hashes after exploiting the vulnerability. The retrieved credentials can be used to log in as a user and access the systems. Once detected, Disable AD User playbook can be leveraged to disable the user and reduce response time.
Further, the analyst or administrator can utilize the Logpoint AgentX Isolate-Unisolate Host playbook to isolate the host and prevent lateral movement.
Remediation and mitigation
We recommend applying the patch released on ‘patch Tuesday’ (11th April 2023) by Microsoft as soon as possible, as it is the optimal way to mitigate the risks of being susceptible to the attack.
We know that applying the patch to some systems comes with its own set of caveats. Therefore, if patching is not immediately possible, ensuring you have implemented these security best practices can help mitigate this threat to a large extent:
-
Regularly scan and assess organizational assets for vulnerabilities and misconfigurations to patch them, and maintain updated Operating Systems, firmware, and applications.
-
Strongly enforce MFA and phishing protection for both user and administrative accounts. Adopt the practice of least privilege and time-based access, where possible.
-
Conduct simulated attack scenarios to make sure that the employees are well aware of phishing and other risks, and also to make sure that they report the incident to the internal cybersecurity team.
-
Extensively implement network segmentation to prevent the spread and limit the impact.
-
Deploy Logpoint AgentX or other endpoint protection platforms (EPPs) to secure endpoint devices and ensure they are up-to-date, properly configured, and trigger alerts when disabled.
-
Develop the practice of regularly creating and maintaining offline encrypted backups that encompass the entire organizational data infrastructure, and assure their availability through periodic restoration attempts.
-
Regularly review the security posture of third-party vendors interconnected with the organization.
-
Actively be on the lookout for leaked credentials on malware data leak sites, and make changes accordingly.
-
Continuously monitor critical organizational assets with a combination of tools such as Sysmon and the Logpoint Converged SIEM platform.
Final thoughts
Patches are like little superheroes for the system, swooping in to save the day and protect our system from potential harm. And when it comes to zero-day vulnerabilities - patches become even more critical. Without these timely updates, our systems could be left open to attack, leaving our personal information and sensitive data at risk. So let’s not ignore those pesky patch notifications - they may be all that’s standing between us and a potentially catastrophic cyberattack.
Further, with a significant rise in the number and level of sophistication among cybercriminal groups; a proactive detection approach is of utmost priority for security analysts of any organization wishing to stay away from harm’s way.
With the Logpoint Converged SIEM platform combining SIEM, SOAR, and EDR capabilities, analysts can investigate Nokoyawa and initiate a proper response.
** We can help you! For help with the suggested playbooks – design, development, and implementation.







