Fast Facts
-
LockBit is a highly persistent and sophisticated ransomware that operates on the Ransomware-as-a-Service (RaaS) model.
-
In 2022, LockBit was the most deployed ransomware variant worldwide and remains prolific in 2023.
-
LockBit attacks are known for their varied tactics, techniques, and procedures (TTPs), posing challenges to the security networks of organizations.
-
The ransomware gang has made at least $100 million in ransom demands and extracted tens of millions of dollars in actual ransom payments.
-
LockBit has grown over time, with new versions providing more features and capabilities such as information theft and targeting systems other than Windows, such as Linux, macOS, and VMware ESXi.
-
Recent high-profile LockBit targets include Taiwan Semiconductor Manufacturing Company (TSMC, SpaceX, and the Port of Nagoya, Japan).
Go To Section
Background
LockBit is ransomware that operates on RaaS (Ransomware-as-a-Service) model and is known for its persistent and successful assaults against companies all around the world. While there are other prominent ransomware gangs, LockBit stands out for its cruel perseverance, sophistication, and multi-year rampage. Since late 2019, the gang has targeted a number of organizations, employing multiple extortion strategies and technologies to increase the success of their operations.
According to CISA Advisory released in mid-June 2023, In 2022, LockBit was the most deployed ransomware variant across the world and continues to be prolific in 2023. In November 2022, the US Department of Justice in their press release wrote that “LockBit members have made at least $100 million in ransom demands and have extracted tens of millions of dollars in actual ransom payments from their victims“. Until Q3 of 2023, it is still one of the most active and profitable ransomware groups successfully targeting machines not limited to Windows but also Linux and VMware ESXi systems, macOS, and also virtually hosted machines, making hundreds of millions of dollars just through ransom which makes it more dangerous and prolific than any other variant of ransomware.
LockBit's Ransomware-as-a-Service (RaaS) model extends its reach and impact by attracting affiliates who deploy the LockBit ransomware. These affiliates are enticed by upfront payments, subscription fees, and a share of the profits. As a result, LockBit ransomware attacks display a wide range of observed tactics, techniques, and procedures (TTPs). This significant variance in TTPs presents a notable challenge for organizations working to maintain network security and protect against ransomware threats.
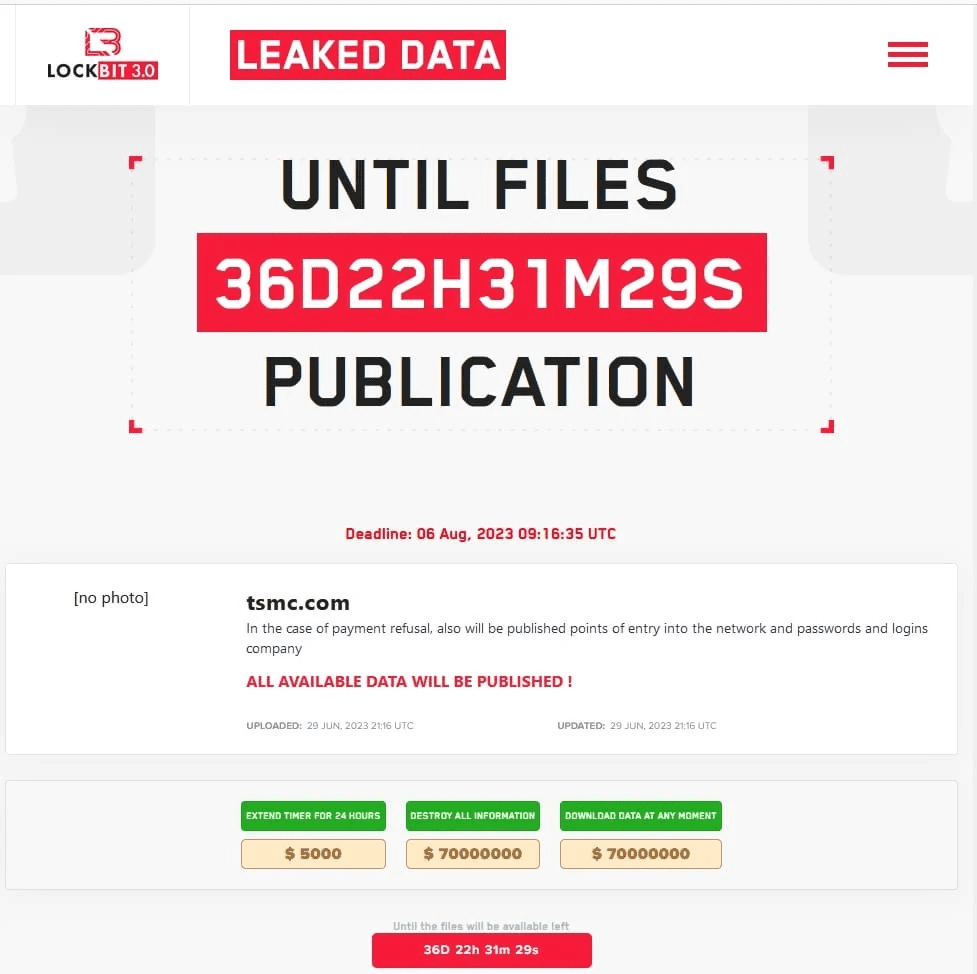
Their target industries and areas of interest are diverse, and there are no restrictions on the type of company they target. They are financially motivated and have been attacking high-profile targets. According to Cybernews, the LockBit group breached Taiwan Semiconductor Manufacturing Company (TSMC), a semiconductor giant responsible for 65% of the world’s semiconductors and 90% of the high-end chips, demanding $70 million for the stolen data as recently as late June 2023. On their blogging website (hosted on the darknet), they have threatened to publish TMSC’s data if they don’t pay the ransom by Aug 6, 2023.
Source: SpiceWorks
According to news released by CNN on July 6, 2023, The most recent target of LockBit is Japan’s busiest and largest port - the Port of Nagoya, a hub for car exports. The attacks likely started on Tuesday, July 4 2023 when the computer handling the shipping containers was knocked offline and general operations of the port were obstructed. According to Nagoya Harbor Transportation Association, the hack shuts down the handling of ships that came to the terminal by trailer.
Origin and Evolution
LockBit ransomware has evolved and transformed significantly from its first detection in September 2019 as ABCD ransomware, leading to its present sophisticated condition. The appearance of LockBit in Russian-language cybercrime forums in January 2020 signaled its formal presence in the cyber threat arena. Notably, LockBit 2.0, also known as LockBit Red, debuted in June 2021, offering StealBit, an integrated information-stealing tool. LockBit Linux-ESXi Locker version 1.0 was released in October 2021, expanding its capabilities by allowing the targeting of Linux and VMware ESXi systems. LockBit evolved further with the release of LockBit 3.0, also known as LockBit Black, in March 2022, with similarities to the BlackMatter and Alphv ransomware. The leaked LockBit 3.0 constructor permitted non-LockBit affiliates in September 2022. In January 2023, the ransomware scene saw the emergence of LockBit Green, which included source code from the Conti ransomware. Furthermore, LockBit ransomware encryptors were discovered targeting macOS devices in April 2023, suggesting the malware's expanding reach. These advances highlight LockBit ransomware's ongoing growth and adaptability, providing a persistent and severe threat to enterprises globally.
| Date | Event |
|---|---|
| September 2019 | The precursor to LockBit, known as ABCD ransomware, is identified through its initial observed activity. |
| January 2020 | LockBit ransomware, bearing its name, initially emerges on Russian-language cybercrime forums. |
| June 2021 | LockBit version 2 (LockBit 2.0), or LockBit Red, surfaces with the inclusion of StealBit, an integrated information-stealing tool. |
| October 2021 | LockBit 3.0, alias LockBit Black, emerges with resemblances to BlackMatter and Alphv (BlackCat) ransomware. |
| March 2022 | Emergence of LockBit 3.0, also known as LockBit Black, which shares similarities with BlackMatter and Alphv (also known as BlackCat) ransomware. |
| September 2022 | Leaked builder enables non-LockBit affiliates to utilize LockBit 3.0 |
| January 2023 | Arrival of Conti ransomware incorporated LockBit Green |
| April 2023 |
LockBit ransomware targets macOS systems |
LockBit Timeline (Source: CISA)
We recommend first studying our prior LockBit release to better understand the contents of this Emerging Threat Report (ETP). That study, released in October 2022, includes insights into LockBit's previous attack strategies and activities. This ETP expands on that foundation by discussing the most recent advances and emerging trends in LockBit's tactics, strategies, and procedures. Reading the prior report will give vital background and improve your comprehension of the shifting threat scenario outlined in this release.
Rather than digging into an in-depth study of each particular sample, we will focus on the common tactics, methods, and procedures (TTPs) seen in LockBit ransomware assaults in this research. We made an attempt to cover all of the reported TTPs mapped using MITRE as well as the behavioral elements related to LockBit ransomware. Our goal is to give a thorough knowledge of the ransomware's behavior by emphasizing the similarities in its assault tactics and providing a holistic perspective of its functioning.
We will discuss viable detection procedures for each TTP that can assist companies in identifying symptoms of compromise or malicious behavior linked with LockBit. This might involve using network monitoring tools, anomaly detection software, or endpoint security solutions.
In addition, we will offer remedial procedures to lessen the effect of LockBit attacks. These measures may include isolating impacted systems, recovering data from secure backups, deploying security fixes, or enlisting the assistance of incident response teams.
**All new detection rules are available as part of Logpoint’s latest release, as well as through the Logpoint Help Center. (https://servicedesk.logpoint.com/hc/en-us/articles/115003928409).
Logpoint Emerging Threats Protection Service provides the service subscribers with customized investigation and response playbooks, tailored to your environment. Contact the Global Services team here.








