Emerging Threat: Akira, Not a CyberPunk Movie – A Very Real Ransomware Threat
Fast Facts
-
Emerging in March 2023, Akira ransomware has been grabbing daily headlines with its relentless and perilous assaults, leaving a trail of mounting victims.
-
Akira is actively targeting Cisco ASA VPNs without multi-factor authentication to exploit CVE-2023-20269 as an entry point for their ransomware.
-
Akira was among the Top 10 Ransomware groups in August 2023, with no indication of slowing down.
-
Not only Windows, but the Akira variant can also infect Linux systems
-
As of September 6, 2023, they have successfully struck 110 victims, including big-name organizations such as Quality Assistance Leader, Intertek.
Background
Although Akira is a relatively new ransomware variant, it has been making headlines for its ongoing ransomware assaults since its initiation in March of 2023. According to Bleeping Computer, there were several ransomware operations with the same name (Akira) in 2017, although these two operations are unconnected.
As of September 15, 2023, they have successfully targeted 110 victims, mainly those located in the U.S. and the U.K. Without a particular target, they have honed in on a wide range of industries including education, finance, real estate, manufacturing, and consulting. We have continuously monitored data from ransomware.live, and the statistics are presented and interpreted in the chart below.
| Month | January | February | March | April | May | June | July | August |
|---|---|---|---|---|---|---|---|---|
| Victims Leaked per Month |
0 | 0 | 0 | 10 | 23 | 27 | 18 | 29 |
| Year | 2023 |
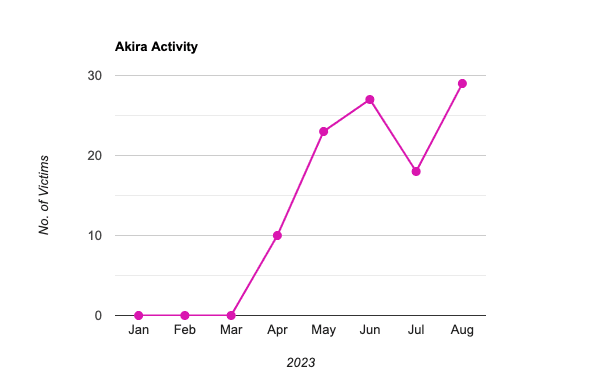
Akira Ransomware Activity Trend
This chart resembles the current engagement trend and the increasing victims list of the Akira ransomware gang. It suggests that their activities will only increase without showing any indications of slowing down in the near future. In addition, with every campaign, they are continuously evolving, exhibiting new patterns, features, and capabilities making it even more ferocious and harder for the blue team to detect new attacks.
According to SentinelOne, the Akira Ransomware gang applies multiple extortion techniques. They have their own separate leak website in the dark web where victims are listed along with any stolen data should a victim fail to comply with the ransom demands. In the ransom note, the victims are instructed on the ways to negotiate the ransom through their TOR-based portal. Using multiple extortion schemes, they are also demanding millions of dollars in ransom.
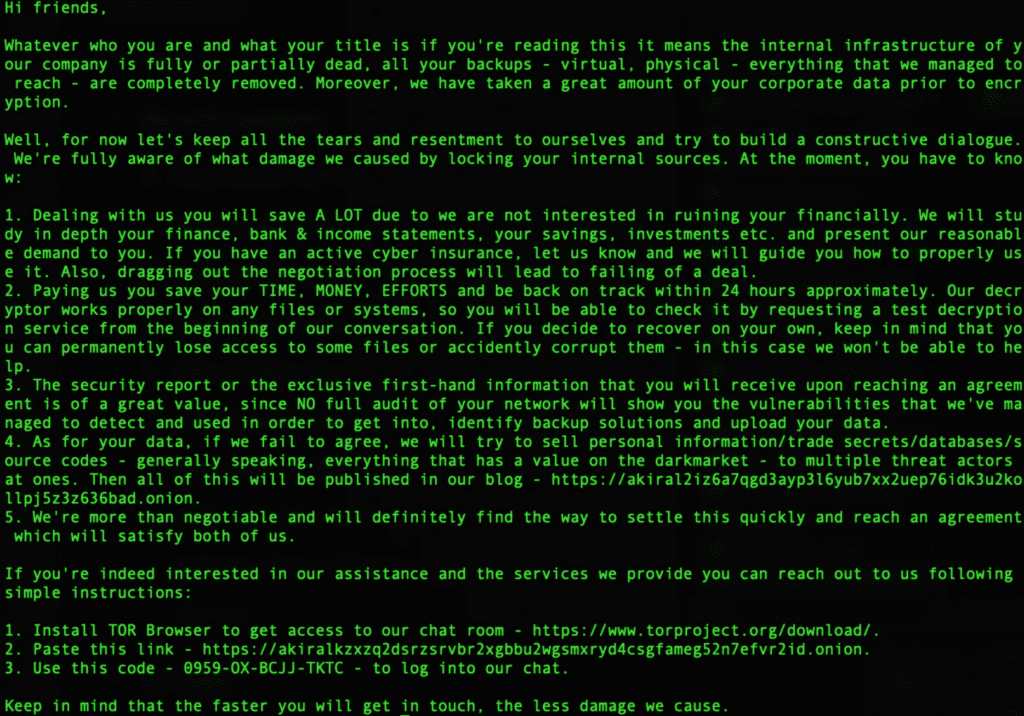
Ransome Note: Source Akira
According to NJCCIC, Avast published a free decryptor for Akira in June 2023, however, it was only effective against previous versions of the ransomware. Akira has been constantly being developed with new features and capabilities in each campaign. More recently, Akira also began expanding its reach beyond Windows to Linux-based systems, targeting VMWare ESXi virtual machines. According to an 'X' (formerly Twitter) thread on Aug 28, 2023, the Security Researcher suspects Megazord could be a new version or rebranding as it was observed using Akira infrastructure. In August 2023, activities and victims were increasing subsequently placing them among the top 10 ransomware gangs that month as shown in the chart shared by Daily Dark Web (below).

Recent victims include Penny Publications LLC, Voss Enterprises, Divvies, Cutler Smith PC, etc. The big name that was recently breached by Akira was Intertek. On August 28, Dominic Alvieri, via 'X' (formerly Twitter) wrote “Quality assistance leader Intertek has allegedly been breached by Akira”.
On the same day, Falcon Feeds also confirmed this allegation stating “Akira ransomware group has added Intertek (http://intertek.com) to their victim list”, sharing the screenshot of Akira’s blog post in which it is claimed that “They have access to more than 300GB of data which includes personal docs, business partners info, confidential agreements, and reports, etc.”

Cisco VPN solutions are widely adopted across many industries to provide secure, encrypted data transmission between users and corporate networks, typically used by remotely working employees.
However, a significant security concern emerged on August 24, 2023, when Cisco released an advisory mentioning Cisco ASA VPNs that are not configured for multi-factor authentication are being targeted by Akira to infiltrate organizations. Cisco also released another article on September 6, 2023, where it was mentioned that it was indeed a vulnerability (CVE-2023-20269) on the Cisco ASA device which allows remote attackers to conduct a brute force attack in an attempt to identify valid username and password combinations or an authenticated, remote attacker to establish a clientless SSL VPN session with an unauthorized user. Additionally, Akira was also found using remote access tools, such as RustDesk, to gain access to targeted networks.
Emerging Threats Report
In the attached report, we perform a thorough assessment of the Tactics, Techniques, and Procedures (TTP) employed by adversaries, in conjunction with an examination of the matching capabilities displayed by the malware they employ. Our research is based on malware samples obtained from reliable sites such as filescan.io, as well as insights offered by Security Researchers via Twitter threads.
Furthermore, we leverage the capability of cloud-based sandboxes like Any.Run, tri.age, and vmray to undertake an in-depth analysis of the TTPs displayed by these malware specimens. After the final assessment, we created and/or included existing detection rules to identify the suspicious TTP exhibited by the adversary. In addition, for investigation and response, we also have provided playbooks.
**All new detection rules are available as part of Logpoint’s latest release, as well as through the Logpoint Help Center. (https://servicedesk.logpoint.com/hc/en-us/articles/115003928409).
Logpoint Emerging Threats Protection Service provides the service subscribers with customized investigation and response playbooks, tailored to their environment. Contact the Global Services team.





