By Ivan Vinogradov, Solution Architect, LogPoint
The MITRE ATT&CK framework is a structured collection of adversarial techniques that is meant to assist in all aspects of security activity, with a focus on blue teams. By creating a unified framework, MITRE has enabled security professionals to communicate more clearly and share information more efficiently, thus contributing to a higher level of security globally.
How the ATT&CK framework helps security teams
There are several areas the framework can assist a security professional – most of these defensive. Analytics, forensics and intelligence all benefit from a unified framework that classifies existing threats. Using the framework, cybersecurity specialists with different levels of expertise can communicate information without any of it being lost between the cracks.
For a security analyst, the framework speeds up reaction time and helps with response. Analysts can map alerts directly onto the framework, which optimizes processes and makes it easier to create comprehensive playbooks for security operations centers (SOCs). Furthermore, alerts in the framework are mapped sequentially, so analysts can accurately escalate incidents and know how to respond to the threat.
When it comes to threat hunting – the chief benefit is the ability to place a starting point on the investigation. A starting point gives analysts a rough idea of the location of the point of the compromise if a substantial threat is discovered. The ATT&CK framework also benefits threat intelligence by increasing analysts’ ability to share threat information, without going into details.
Using ATT&CK in SIEM
SIEM solutions generally benefit from the use of the ATT&CK framework. It classifies attacks according to type as well as stage, which allows the analyst to quickly pinpoint the attack position in a compromise and articulate findings to team members. Furthermore, the framework classifies incidents without necessarily requiring a deeper insight into the methods, which expedites training and standardization of SOC procedures.
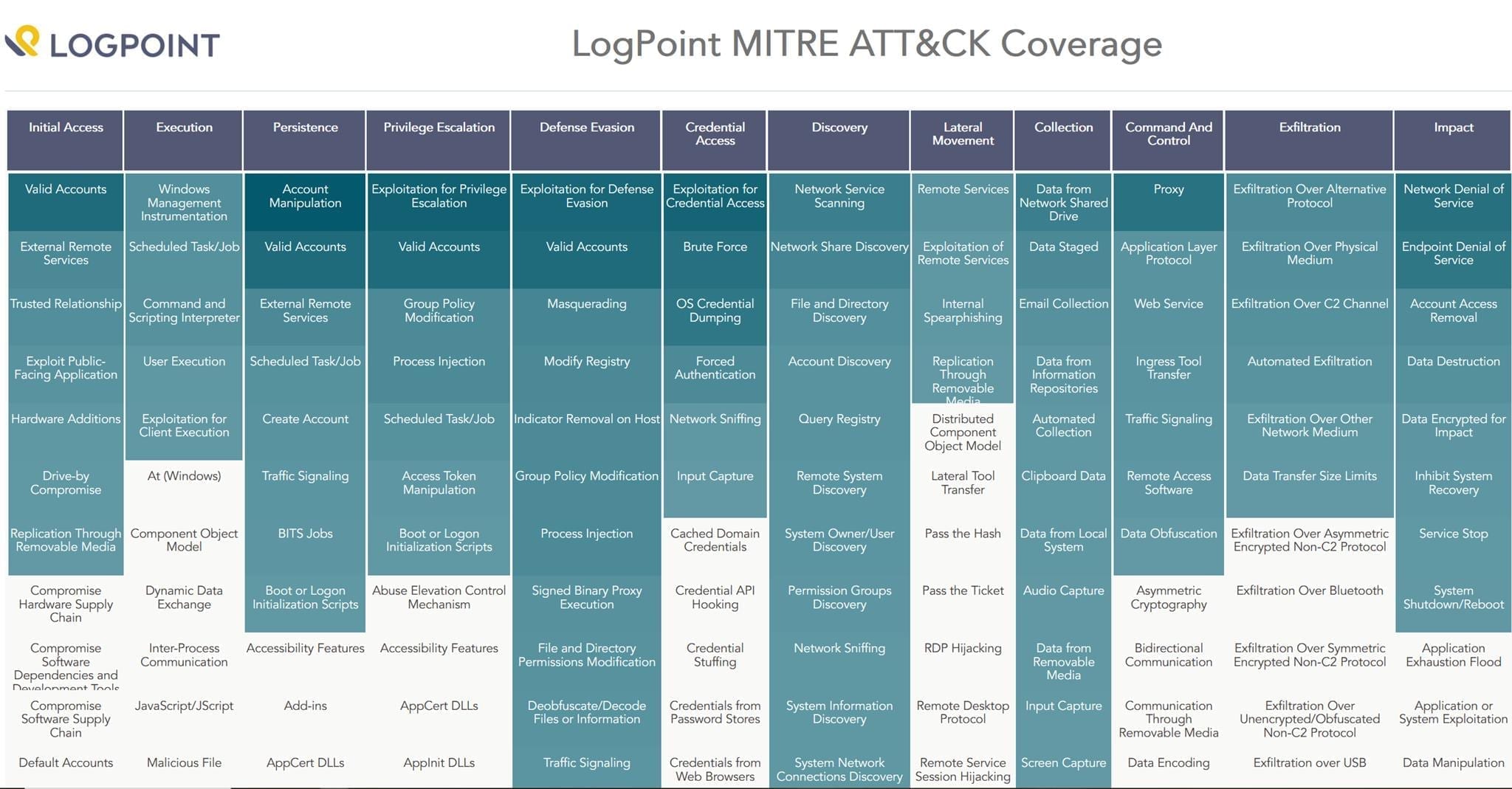
Security analysts can use ATT&CK to understand more about adversary tactics and techniques.
The ATT&CK framework also benefits employees outside the analyst team. The framework is steadily becoming an industry standard, making it a great tool to communicate to higher-level personnel, such as senior leadership and security managers. Using ATT&CK, it’s much easier to produce a high-level overview of incidents with more accuracy. The framework even helps with automation, such as dashboarding and reporting, which are in high demand among auditors and CISOs.
ATT&CK and LogPoint
When it comes to LogPoint, the broadest application area of the framework lies in classifying alerts. Classification gives a reasonable degree of high-level security awareness very quickly, especially when used in combination with any of LogPoint’s visualization methods. Standard LogPoint alerts combined with an ATT&CK reference give immediate value in a low-intensity environment. Even in a higher throughput environment, a LogPoint security solution using ATT&CK provides value through an improved security overview.
In addition to the benefits mentioned previously about ATTC&K improving internal communication about threats, the framework is also widely understood and used by external security contractors. LogPoint alerts are already mapped to the ATT&CK framework, making it easy to quickly communicate about an alert, even with external stakeholders.
LogPoint dashboards display ATT&CK tactic distribution, which is useful particularly in larger environments. LogPoint is built to provide an overview of alerts and the ATT&CK heat map in the dashboard gives larger organizations the insight to more accurately identify the stages of an attack.
Summing up
Overall, the ATT&CK framework is a dynamic, standardized and widely popular method of classifying and communicating security information in a way that is accessible to both humans and machines. We strongly advise that you evaluate your security posture using the ATT&CK framework because it represents the peak of modern security community collaboration.
Integration and automation of security services are key drivers of LogPoint as a security solution. The ATT&CK framework is an instrumental part of improving security awareness out of the box. It also allows analysts to better assess information from other devices and solutions.
What is MITRE?
MITRE is a non-profit organization focused on cybersecurity and solving security challenges to create a safer IT environment for organizations. MITRE developed the ATT&CK framework as a universal way to classify adversarial tactics.
What is the ATT&CK framework?
Started in 2013, ATT&CK is a community-driven knowledge base of adversarial techniques that are organized into a set of tactics to help explain and provide context for the technique. Tactics are the “why” of a technique and the techniques are “how” an adversary achieves an objective by performing an action.