When purchasing a new security solution, decision-making is rarely an individual process but rather an alignment of many moving parts in the form different stakeholders and their needs. While Finance will search something that fits the budget, IT will need a an easy-to-operate tool, Risk Management requires a clear overview of what it does, and Cybersecurity wants coverage, efficacy and integration capabilities among other aspects. The key to this situation lies in balancing all of them equally.
According to a World Economic Forum study, business executives should not expect security executives to perform without empowerment. Instead, they should align and involve security executives in business decisions and objectives. When considering security solutions, their role should go beyond checking the technical requirements and asses the future ramifications for the company, including the pricing evolution of the new tool and possible business outcomes, like building a trusted enterprise by staying compliant with regulators and protecting your employees and customers data.

However, many organizations lack long-term vision of their security infrastructure and only focus on the cost they are ready to assume, and the capabilities of the products pitched to them. And in many cases, short-term price becomes a decisive factor in the acquisition of a security tool. So, false ideas like Microsoft Sentinel can be enabled at no cost become too irresistible to say no. But is it truly inexpensive in the long run?
What is Microsoft Sentinel and why it’s so popular
Microsoft Sentinel is a popular Security Operations Platform. This cloud based SIEM platform runs in the Azure cloud and offers a range of threat intelligence, detection, and response capabilities.
Its popularity is due to Microsoft’s undoubtedly big name in the tech industry covering both household and business solutions that oftentimes are bundled into Microsoft 365 subscription plans. This leads to the unfounded idea that Sentinel, as well as other Microsoft products, come as low cost or free, reassuring business executives to opt for them instead of many other alternatives in the cybersecurity market.
In addition to its big name, there is the unfounded idea that organizations using Microsoft products are more secure because Microsoft has an interest in protecting their infrastructure. But what happens with all the other tools outside of Azure? Attackers will always look for the path of least resistance to infiltrate your data, whether it’s under the label of Microsoft or not, as we saw with the zero-day vulnerability in the Windows CLFS Driver.
Microsoft Sentinel is not for free
Let’s cut to the chase. The only free thing about Microsoft Sentinel is the 31-day trial – and in many organizations, this trial is used for testing and evaluation. But you may wonder where this idea of Sentinel being free comes from. Mostly from advertising some no-cost logging sources and the efforts put in by some of Microsoft’s evangelists.
However, Microsoft Sentinel is not bundled into a Microsoft 365 plan, but instead in an E5 license, and not all logging sources are free. Only a small group of log types and data tags are ingested at no cost, such as Office 365 audit log, Azure AD Identity Protection, Azure activity logs and Microsoft Defender alerts. However, there are plenty of other logs that any SOC deals with daily and that don’t fall into this coverage but need to be ingested to protect the organization – and those come at a price.
Instead of a predictable pricing scheme based on the number of nodes or users, Sentinel’s pricing uses a data-consumption basis organized in two models: pay-as-you-go and tiers. So, this can be a problem over time because global data volume will continue to grow, reaching 175 zettabytes by 2025, as per Deloitte’s analysis. But these are only estimations, so there’s no way for companies to predict in a precise manner the amount of data they will consume, making it difficult to budget how much security costs every month.
In addition, full log storage comes at a price too. So, even if you ingest data sources from within the Azure cloud, you still need to pay for retention periods.
Is Microsoft Sentinel worth the cost?
Roughly speaking, it all depends on the organization. However, for most organizations, it’s unrealistic to think that your architecture is going to be solely Microsoft based.
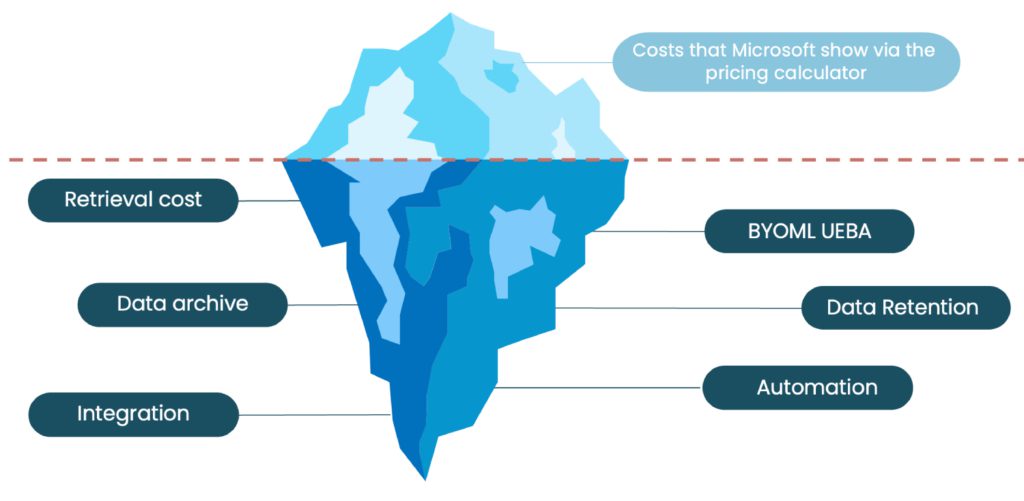
Sentinel can be expensive if you ingest data from sources that are outside of the Azure cloud. And for organizations with large amounts of data, the cost can be steep.
The only way to remediate this would be to only ingest those security-specific logs that are necessary. Yet, this creates loss of visibility, and limiting data can also be a risky approach as attackers are continuously changing their tactics. So, even if organizations eventually decide to invest time and resources in cleaning up the number of logs ingested and the storage period, customers should be able to reach their security objectives without worrying about restricting what they ingest and from where.
Log retention
And it’s in the log data retention, needed for compliance and forensics, when things get complicated. When Sentinel is enabled on Azure Monitor Log Analytics, there is a free retention period of 90 days. After that, there is a monthly charge for each GB of data retained.
However, healthcare institutions are required to keep logs for up to 6 years to comply with HIPAA. Another example is the mandatory retention period of 6 months the European Commission’s security standard. Before counting chickens before they’re hatched, organizations choosing Sentinel should remember that to adhere to the minimum log retention requirements they will need to pay.
Extra tools come at a price
It’s not enough to just use Sentinel to have an end-to-end security platform. Analysts also need other solutions for a full TDIR (Threat Detection and Incident Response), and that’s when the surprise comes.
Tools like Microsoft Defender, Azure Logic Apps and UEBA imply additional charges that increase the total cost of ownership (TCO). And for the sake of a good TDIR process, most SOC teams can’t just get by without them, especially when the data they deal with requires extra protection.
So, when you start juxtaposing the initial idea of “free” against all charges incurred in log ingestion and retention, it soon stops being a like-for-like comparison. In the long run, this translates into a higher TCO.
Failure to comply with Schrems II can be expensive
Lack of pricing predictability is not the only thing that can make choosing Microsoft Sentinel or any other security operations platform an expensive decision, especially for organizations based in the EU. Failure to comply with data residency in the EU can result in expensive fines.
Microsoft is unable to guarantee geofencing that Sentinel as well as some other services are in-scope for the EU Data Boundary and, as a result, that data won’t leave the EU. CEOs and CISOS of organizations that choose Sentinel don’t have the peace of mind that they will comply with GDPR if Microsoft is legally bound by a government order to release data to U.S. security authorities.
Limited third-party integrations
Yet another reason that any business executive must bear in mind before choosing Sentinel is the lack of out-of-the-box support outside of Microsoft Product Suite for third-party integrations. Instead, analysts need to learn ASIM to build their own parsers for unsupported integrations.
According to Gartner’s research, 80% of enterprises will have adopted a strategy to unify web, cloud services and private application access from a single vendor’s security service edge (SSE) platform by 2025. The lack of support for other integrations creates observability inefficiencies and makes companies’ tech stack more complex.
Complex taxonomy and query language
Eventually, all cybersecurity decisions should take into consideration personnel resources and response time. The absence of a source-agnostic single common taxonomy makes day-to-day TDIR workflows difficult, reducing throughput and increasing the MTTR.
And let’s not forget the learning curve that comes with using KQL to perform daily operations. The syntax and semantics of this query language are highly complex, and organizations would need to invest resources in educating their analyst and retaining talent.
Final thoughts on Microsoft Sentinel
Throughout this article, we have separated the wheat from the chaff in this false premise of Sentinel as an inexpensive option. Costs can add up quickly when you factor in log storage, additional features or indirect costs.
- Only a limited number of log sources are free, and their free data retention policy of 90 days doesn’t add up when organizations must keep them for six months due to several regulations.
- Besides, those who choose Sentinel must also bear direct costs for ingesting logs outside of the Microsoft suite, and indirect costs, such as staff training in ASIM to build parsers for integrations and in KQL to query the Azure log databases.
- Its pricing scheme based on data consumption doesn’t seem sustainable for high-growth companies or organizations with an increasing volume of data.
- Incident response automation, like LogicApps, and machine learning have additional charges. So, organizations that need adjacent tools along with Sentinel for complete SIEM, SOAR, and UEBA capabilities will see an increase in the TCO.
- Its lack of guarantee of compliance with Schrems II can, and should, deter European enterprises that fear reputational and legal risks from choosing Sentinel, instead of an EU-based solution.
How Logpoint stacks up
At the end of the day, the best SIEM is the one that works best with the organization’s needs, both present and future ones. It’s fair to say that Logpoint, as a European vendor, has compliance with GDPR and Schrems II as a priority, but also with other major regulatory domains such as HIPAA, NIS2, PCI-DSS and SOX.
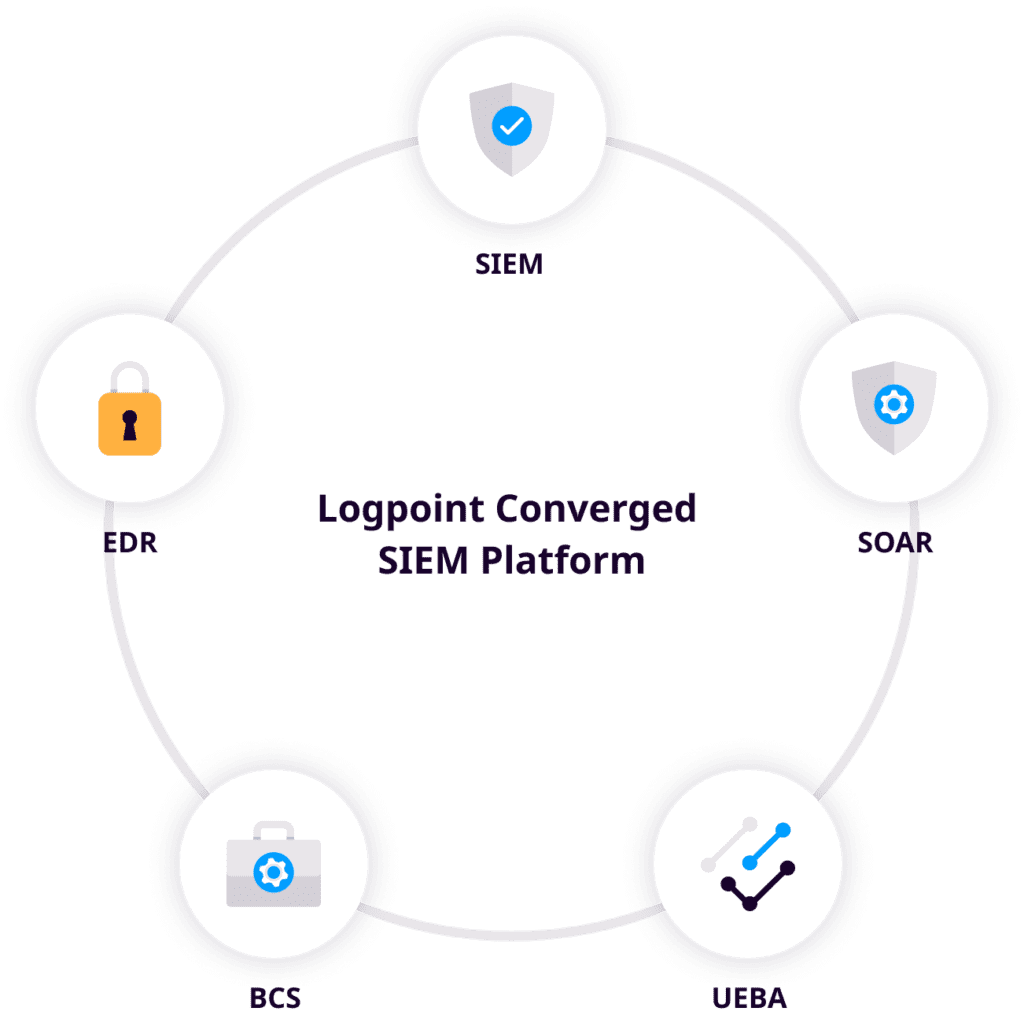
Logpoint’s pricing scheme is independent of data volume, but instead, it’s based on the number of nodes or users – if you want to know the EPS and the volume of data processes in your network, you can always check our SIEM sizing calculator. On top of that, the Logpoint Converged SIEM always comes with a free SOAR seat. So, the TCO is always predictable and lower in the long run.
On the other hand, Microsoft’s model becomes problematic as the consumption is not only on data, but on alerts, correlations and SOAR actions. For organizations, such complexity makes it almost impossible to foresee what the costs will be in the future based on what the cost now. And it’s because of this that many businesses don’t have a single-SIEM strategy based on Sentinel.
Reducing complexity of the tech stack
Yet, Logpoint can provide this full coverage through the Converged SIEM platform by fusing weaker signals from endpoints, network, Business-Critical Solutions and infrastructure and then using one single taxonomy to enable detection and response across the entire portfolio.
With a focus on customer experience, Logpoint’s Converged SIEM platform supports out-of-the-box integrations of more than 600 vendors, and we continue to add more log integrations at no additional cost to the customer. All our solutions, whether it’s SOAR, UEBA and endpoint security (AgentX) are on the same platform. This brings not only consolidation of your tech stack but also smooth integrations and data cohesiveness in one single environment.
Hopefully, this analysis of Microsoft Sentinel and what costs entails helped both business and security executive to inform their decision during their research process. Remember you can contact us or book a demo if you want to know more about Logpoint Converged SIEM and how it can help you improve your security posture and streamline your TDIR.







