Losing control over your organization’s data is one of the main concerns for businesses and organizations the world over. The reality is that more often than not the main motivation of attacks is monetary and includes the human element, whether it’s an internal or external actor.
In many cases, data breaches lead to data exfiltration. This is the case when there is an unauthorized transfer of sensitive data outside of the organization’s network with malicious intent.
Go To Section
How does data exfiltration happen?
Situations where employees leak data are unfortunately not rare. However, not all insider threats revolve around an angry employee or someone looking for a new side hustle. The source of data exfiltration can also be external even if it’s an insider threat.
Let’s think about a Pass-the-Hash Attack (PtH), a technique in which the attacker captures a password hash to get authenticated and travel laterally within the network. The worst part is that the attacker doesn’t need to decrypt the hash to get the actual password, but it will exploit the authentication protocol to move around the network checking where it can authenticate.
Here the intensity of the problem grows with the user’s privileges. So, the higher the privilege the more likely the attacker manages to access a server containing critical information. In that case, they will then proceed to exfiltrate the data.
How can organizations prevent data exfiltration?
Because data exfiltration is not an attack per se, but the consequence of a rogue network user or a mistake committed by someone in the organization, fighting against it is not easy. The preventive measures in place should cover the whole sequence; from preventing the attack to monitoring the network activity.
Many organizations require regular password renewals and education around the best security practices for employees to stop malicious actors from getting inside. In addition, they often rely on software for email security to prevent phishing.
With all of this in mind, enterprises should stop thinking about whether an insider threat is possible and instead assume that there will be - attackers who will always look for the path of least resistance. So, learning how to detect them despite their lateral movement techniques is fundamental to preventing data exfiltration.
How to prevent data exfiltration with Logpoint SIEM
When it comes to preventing data exfiltration, Logpoint SIEM is a powerful ally. Its capabilities range from the endpoint interrogation features provided by AgentX and its ability to run playbooks for investigation and response of incidents in endpoints to using Behavior Analytics to get specific alerts on abnormal behavior. Security analysts can detect and respond to attacks before important data gets leaked.
These important tasks can also be accomplished with just SIEM capabilities and a bit of skill.
Here’s a hypothetical scenario of a malicious actor trying to access data by infiltrating the system with a Pass-the-Hash attack.
Detection and preliminary investigation of a Pass-the-Hash attack
In this use case, Logpoint SIEM normalizes the logs and enriches them as the data is received. After analyzing the data, it raises three incidents related to this Pass-the-Hash attack.
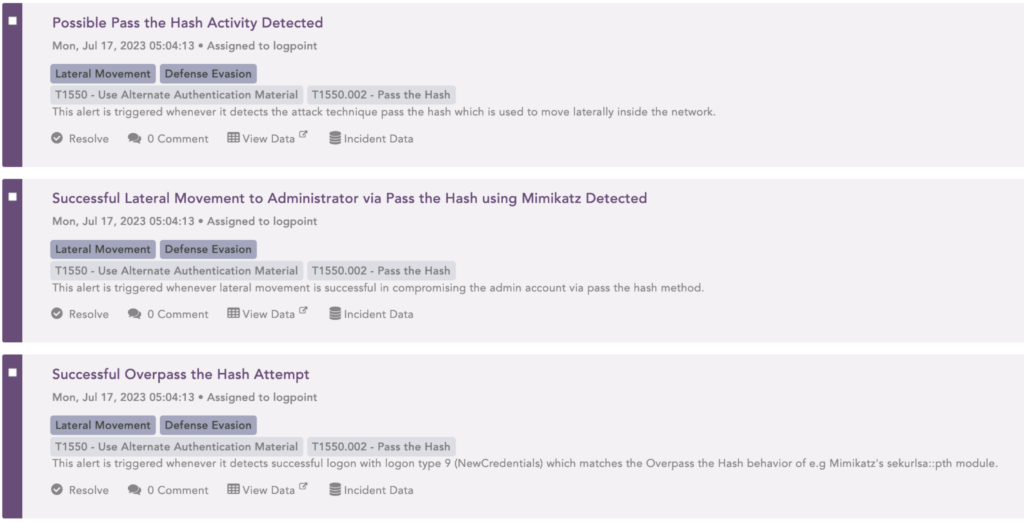
Upon investigation, it’s discovered that the incidents revolve around the user “Kevin Stokes”.
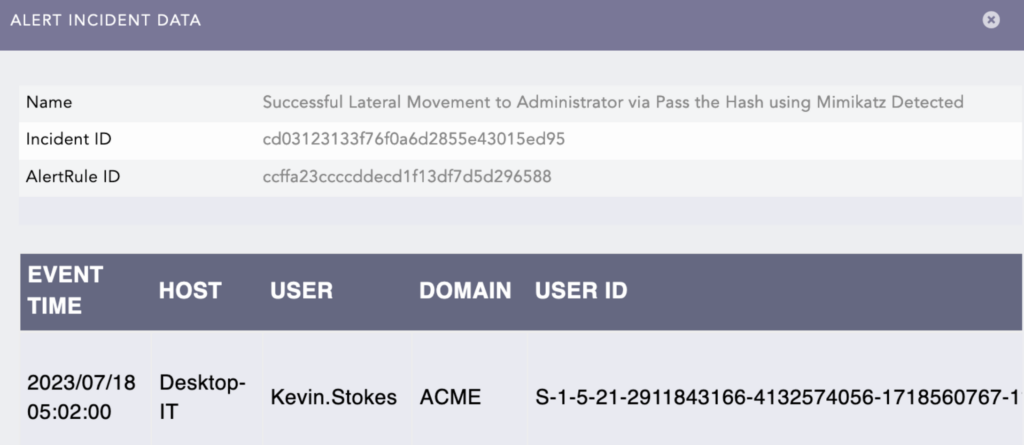
With a search template to monitor suspicious user activity, the analyst moves forward with the investigation. This helps them save time investigating different users by just changing the name in the template fields.
Using search templates for deeper investigation
With the different widgets in the search template, the incident responder can see who has been flagged for performing actions related to 'Pass the Hash', which servers that user has been logged on, and if some of the websites visited by the user have been flagged by the threat intelligence engine as suspicious.
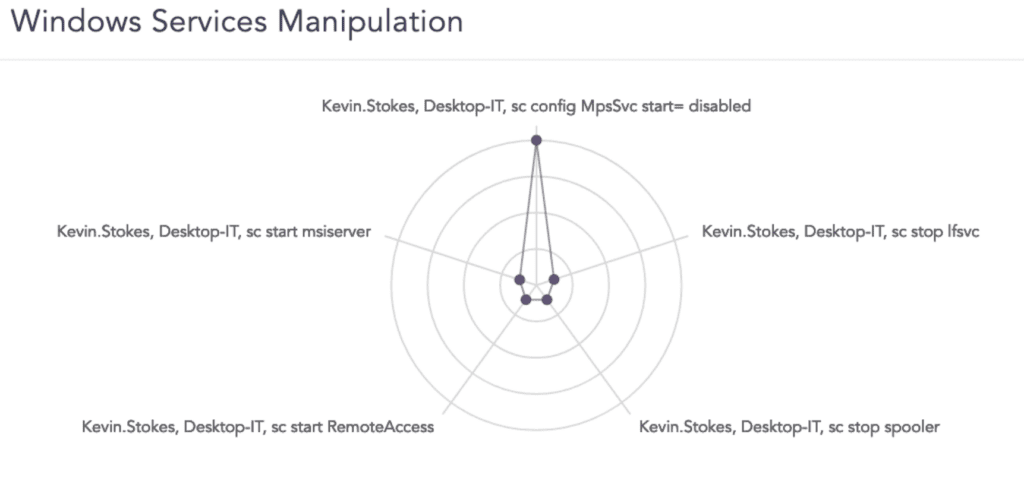
To deep dive into the investigation, the analyst can monitor the service and find out, among other things, that the antivirus protection for the servers the user accessed has been disabled. Other changes are the deactivation of the firewall and location services and the action of remote access.
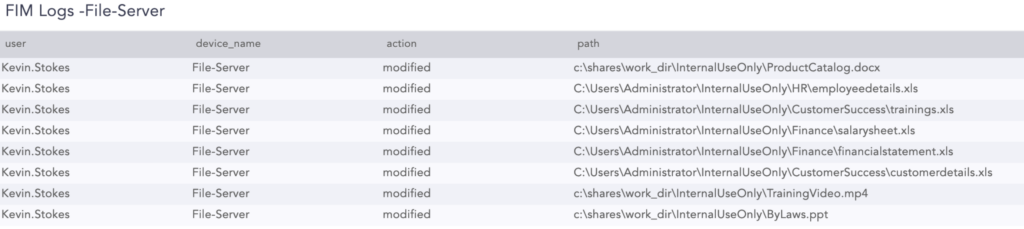
With a few clicks analysts can see which files the user has accessed. In this case, there are signs that the user accessed and modified product, customer details, and payroll information. And with another widget, the template shows scripts to add and delete passwords from the server.
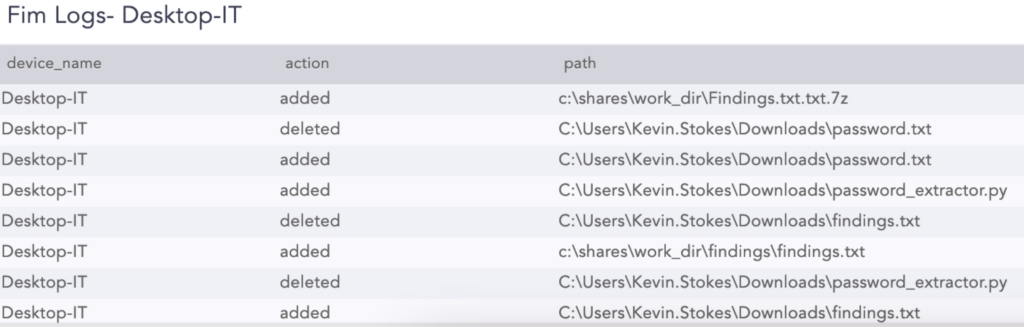
The last stop in this search template is file downloads, showing which files were downloaded from which server and where they were placed. This indicates a clear case of data exfiltration.
Only with standard SIEM logs and using Search Templates to narrow down, can the analyst deconstruct this data exfiltration case step by step, put measures against it, and start the response process.