By Gitte Gade, Product Marketing Manager, LogPoint
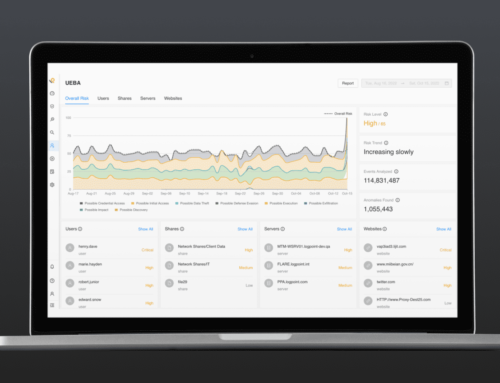
Security analysts are often faced with an overwhelming number of incidents, making it difficult to know what to prioritize for investigation. A common taxonomy allows security analysts to react to and resolve threats quickly by knowing instantly which type of threat it is.
With LogPoint 6.12, it is now possible to categorize alerts and incidents to a single common taxonomy like the MITRE ATT&CK framework.
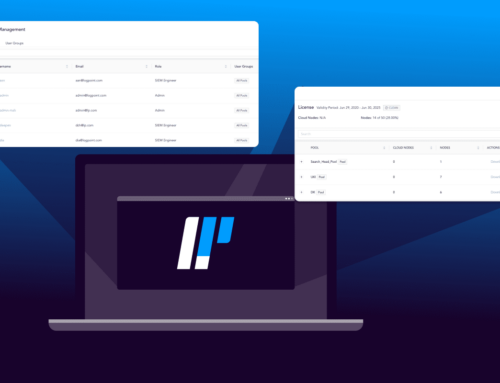
To give the best possible overview for security analysts, classifying alert rules allows filtering all alert rules based on either log sources, attack category, or attack tag.
Watch Nils Krumrey, Sales Engineer with LogPoint, demonstrate how the new feature provides a better overview of different types of incident and alert rules.
Securing the next step
In addition to providing an overview and minimizing the time to identify what type of alert or incident needs to be addressed, categorization helps analysts with response. Incident categorization ensures that third parties or their tools can use this downstream to resolve the incident. The result is that with this update, you are enabling orchestration with automated tools like SOAR.
Share your improvements and updates of search and report templates
As a SOC team, it is crucial to collaborate and share knowledge across functions, and with LogPoint 6.12, it is now possible to configure role-based access to specific search and report templates. The template are shared as references to the same item to ensure that updates are applied to all users using the template. Role-based access to templates increases efficiency because it eliminates the need to create duplicates every time you make changes in your content.
Download LogPoint 6.12 today!
Visit the LogPoint Help Center to download the latest version of LogPoint and read the release notes.