By Gitte Gade, Product Marketing Manager, LogPoint
We are happy to announce an update, which will be rolled out automatically for all users starting week 40. The update brings three exciting new features; primary and secondary entity support, and anomalies mapped to MITRE ATT&CK
Primary entity support:
Primary entities will, with this update, include servers, shares, and websites, including detectors for those primary entities. This feature will provide are more nuanced understanding of the risks in your network, as we will offer insight into other risk profiles than just users.
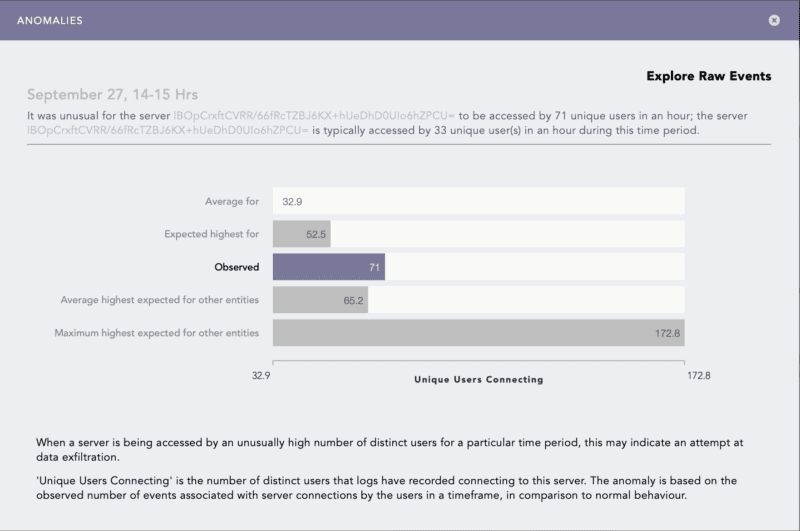
To get full anomaly context for these new primary entities, you’ll need to upgrade to LogPoint SIEM version 6.12 (Please notice that the LogPoint 6.12 will be released at the beginning of October). You can still reap all the benefits of the new primary entities without upgrading to 6.12. However, your anomaly context will have some unpopulated primary entity ids:
Anomaly context description box in UEBA
Secondary entity support:
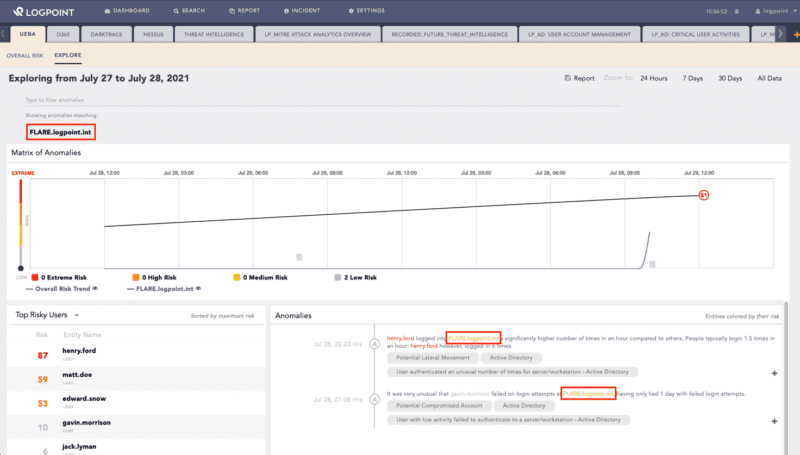
The update provides users with improved filtering options to give more layers and angles to the same data by reintroducing the support of secondary entities. When a secondary entity is detected in an anomaly, it will be exposed in the anomaly context.
The secondary entity will also be filterable, and your anomalies panel can provide you a filtered view of all anomalies where the secondary entity is used abnormally.
Explore page in UEBA
Anomalies mapped to MITRE ATT&CK
With this update, we will map all anomalies to the MITRE ATT&CK tactics. LogPoint SIEM centers around the MITRE ATT&CK framework. Therefore, we are increasing the alignment between LogPoint SIEM and UEBA while also levering a globally accessible knowledge base of adversary tactics from real-world observations.
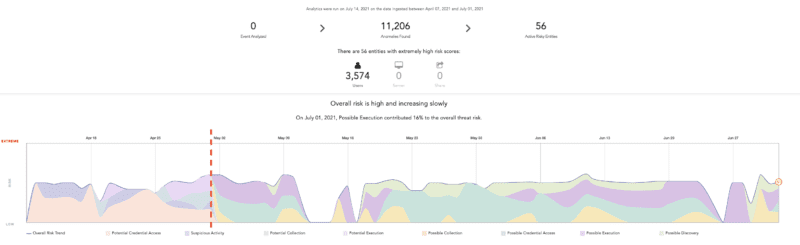
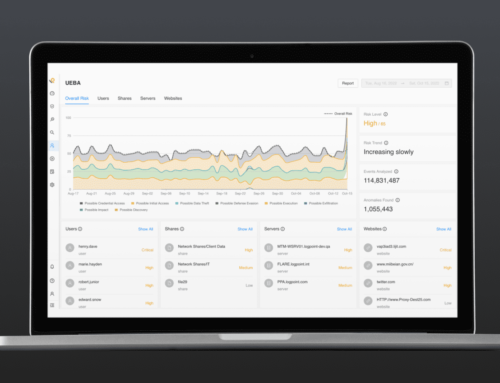
Users will go through a transition period in moving from the prior LogPoint generated use cases to the MITRE ATT&CK categorization. In the picture below, we see the change in the stacked threat landscape happening on May 1:
- Before: The stacked threat landscape is based on LogPoint use cases
- After: MITRE ATT&CK tactics creates the base for the stacked threat landscape. The categories will be named “Possible” and the tactic name (example: Possible Execution).
The graph shows 100 days of data, and the LogPoint use cases will be phased out of the threat landscape as time goes by. In that timeframe, the legend will be updated with results delivery, and the coloring of each threat type may change from one day to the next.
Overall risk page