By Swachchhanda Shrawan Poudel & Anish Bogati; Security Research
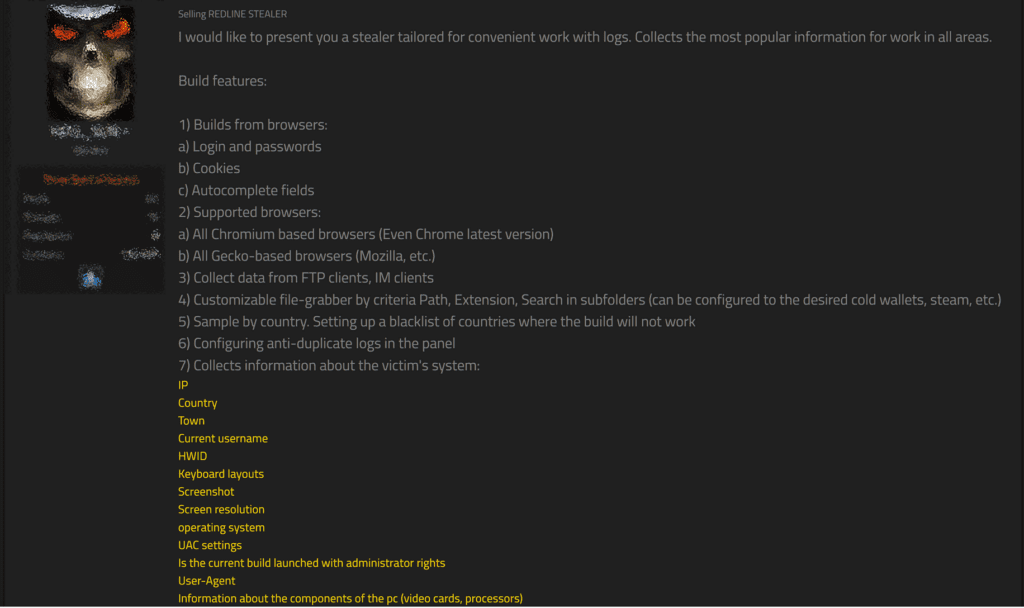
RedLine Stealer, the malicious software that was first seen around March 2020, is a powerful data collection tool, capable of extracting login credentials from a wide range of sources, including web browsers, FTP clients, email apps, Steam, instant messaging clients, and VPNs. But that’s not all – it can also collect authentication cookies and card numbers stored in browsers, chat logs, local files, and even cryptocurrency wallet databases.
In addition, it can gather detailed information regarding the victim’s system, including their IP address, city and country, current username, operating system, UAC settings, administrator privileges, user-agent, and details about infected PC hardware and graphic cards. It can even identify any installed antivirus software on the system. All of this makes RedLine Stealer a formidable tool in the hands of cybercriminals looking to steal sensitive information from their victims. After collection, the malware can exfiltrate those data using various techniques by evading defenses.

Go To Section
How Redline Stealer Works
One of the most common ways this malware is delivered is through phishing emails, where users are tricked into clicking on a link or downloading an attachment that installs the RedLine Stealer. Additionally, cybercriminals have disguised the malware as popular software such as Telegram, and Discord, and cracked software.
Another method of distribution is through redirecting users to compromised websites through malvertising or typo-squatted domains. Once users visit these sites, they inadvertently download the RedLine Stealer instead of the legitimate software they intended to access. Adversaries have continued to utilize various techniques to distribute RedLine Stealer, including masquerading Windows Upgrades, Game Addons, Photo Editing software, etc. This method involves tricking users into downloading and installing what appears to be a legitimate Windows upgrade but is, in fact, the RedLine Stealer.
The low costs and high efficiency of RedLine Stealer have made it a top pick among cybercriminals, including Lapsus$ [G1004], who had used this malware to obtain sensitive data from the victim system after gaining access. Its versatility in extracting login credentials from a range of sources, including web browsers, FTP clients, email apps, Steam, instant messaging clients, and VPNs, coupled with its ability to gather detailed information about the victim's system, has made it a go-to tool for cybercriminals looking to profit from their illicit activities. As a result, the use of RedLine Stealer by threat actors has been on the rise, posing a significant threat to the privacy and security of individuals and organizations alike.
The above section provides only an introduction to the malware and its capabilities. For a comprehensive understanding of the malware, including its distribution methods, execution techniques, ability to achieve persistence, and data exfiltration capabilities, please refer to the attached report. In addition to describing the malware's tactics, techniques, and procedures (TTPs), we have also included detection rules to identify the malware at various stages, as well as a playbook for implementing automated response measures.
The following table presents some of the techniques that we uncovered during our analysis.
**All new detection rules are available as part of Logpoint’s latest release, as well as through the Logpoint Help Center.
Logpoint Emerging Threats Protection Service provides the service subscribers with the customized investigation and response playbooks, tailored to your environment. Contact the Global Services team here.