By Martha Chrisander, Head of Product Marketing
Multiple vulnerabilities published in CVEs and SAP Security Notes regarding web-based attacks against SAP systems are increasing the need for dedicated detection and response capabilities.
According to the SAP Security Response Team, more than 40,000 SAP systems are exposed to the internet enabling remote employees to work more efficiently, supplying a connection to mote offices or providing remote management of SAP systems. Once open to the internet, SAP systems are even more vulnerable to web-based attacks, which can result in a full takeover of the system and loss of business-critical data.
Quickly address web-based threats to SAP systems.
With the latest release for Logpoint’s Security and Audit Compliance Monitoring solution, you can quickly address web-based threats to SAP systems:
- The SAP Internet Connection Manager (ICM) and SAP Web Dispatcher (WD) ensure the communication of SAP systems to the internet.
- ICM processes requests from the internet via HTTP/HTTPS or SMTP and makes sure that the HTTP, HTTPS, and SMTP protocols work properly.
- WD is the entry point for HTTP(S) requests into the system, helping with load balancing and ensuring an even distribution across the servers. It then passes requests to ICM for processing.
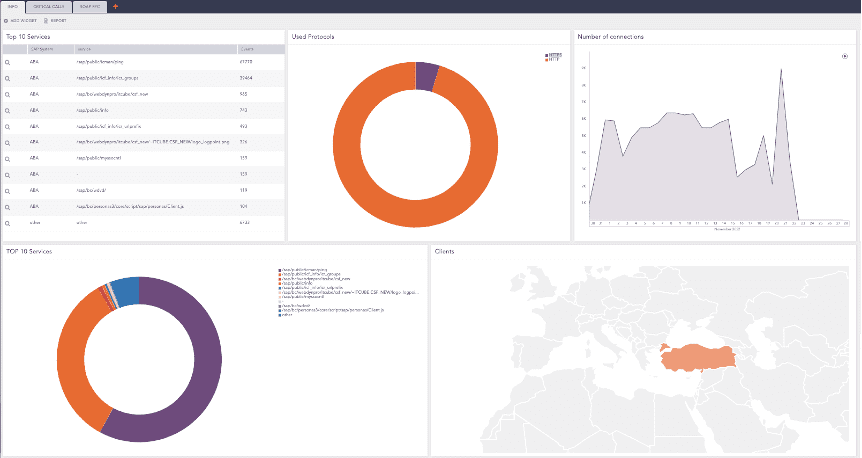
Logpoint provides out-of-the-box visibility into web-based attacks on SAP
While ICM and WD enable the efficient connection between SAP and the outside world, they do not have any threat detection capabilities or the ability to detect malicious requests.
Logpoint’s update to Security and Audit Compliance Monitoring ensures it’s possible to extract ICM and WD data sources easily detecting and responding to web-based attacks. With this update, users can easily integrate client and server HTTP logs, trace logs, security logs, and ICF logs.
As part of the Logpoint Converged SIEM platform, users can leverage ready-to-use dashboards, alert rules, search templates, and response playbooks enabling efficient detection, investigation, and response to web-based attacks associated with business-critical SAP systems. With the latest release, organizations can detect attacks against ICM and WD, such as unauthorized execution of critical function modules and attacks against URLs.
Get started with Logpoint BCS for SAP!
Visit the Logpoint Help Center to read the release notes and download the latest version of Security and Audit Compliance Monitoring.