Threat Detection and Monitoring with Microsoft 365
There’s no doubt that Microsoft 365 is widely used among companies of all sorts of sizes. This powerful suite of productivity tools brings with it an intricate landscape for security teams in those organizations with a large number of endpoints, users, and especially data. Logpoint’s integration with Microsoft Graph API helps SOC teams monitor the Microsoft 365 network, giving them the visibility they need to detect threats and improving the organization’s security posture.
Microsoft365 is a subscription-based service from Microsoft that encompasses a range of tools hosted in Microsoft’s global data centers. It includes core products such as Exchange, SharePoint, and Microsoft Teams, along with Microsoft's public cloud services.Logpoint focuses on identity and access and XDR services to detect and monitor threats and attacks identified by events in the Microsoft 365 platform. Specifically, it utilizes Microsoft Entra ID for identity and access management and Microsoft Defender XDR for comprehensive threat detection and response.Logpoint SIEM leverages data from these services to enhance security, visibility, and response capabilities in Logpoint’s platform. This integration enables organizations to correlate events, detect anomalies, and respond to incidents more swiftly and accurately. It strengthens their overall security posture and protects critical assets within the Microsoft 365 network.
The primary goal of this blog is to showcase cloud security log source integration in Logpoint with Microsoft 365. Using Microsoft Graph API through the Universal REST API Fetcher (URAF), the Microsoft Graph log source template includes REST API endpoints for Microsoft 365 services, namely Entra ID audit logs (audit sign-in and directory audit), Entra ID Identity Protection risk detection and risky users, and Defender XDR alerts and incidents which provides comprehensive alerts and incidents events. Information fetched from these endpoints is used to demonstrate analytics using Logpoint's search query to correlate events, and therefore address security risks and secure critical assets.
What is Microsoft Entra ID?
Microsoft Entra ID, formerly Azure Active Directory, is integral to the entire Microsoft 365 ecosystem. It is a multi-cloud identity and access management platform within Microsoft 365. It enables users inside an organization to access all applications across cloud and on-premise instances. It allows secure access to work applications and protects users' identities, which helps protect the information and services used.
Remembering multiple logins used across various applications and services can be challenging, often leading people to reuse their usernames and passwords across different services. When one of those services gets hacked, and their credentials are leaked, without the user knowing it, adversaries can exploit those credentials to access other services. Entra ID provides a single username and a unified system to log into all of a user’s work services, which are secured with two authentication factors and work with passwordless login, eliminating the need to remember multiple passwords using a single email address. All assigned applications can be accessed from one central location instead of managing independently.
What is Microsoft Defender XDR?
Microsoft Defender XDR (formerly Microsoft 365 Defender) is a unified cloud-based XDR solution that provides visibility, investigation, and response on data across Microsoft Defender for Endpoint, Microsoft Defender for Office365, Microsoft Defender for Identity, and Microsoft Defender for Cloud apps. It collects, correlates, and analyses data, signals, threats, and alerts across these Microsoft security platforms and can stop attacks and remediate affected assets. Microsoft Defender XDR is licensed separately from Microsoft Entra ID.
Using Microsoft Graph to access Microsoft 365 data
Microsoft Graph is a REST API that can interact with data in Microsoft 365, Windows, and Enterprise Mobility+Security (including Entra. ID). To use the Microsoft Graph API, you must register an application in your Microsoft Entra ID. This is because the Microsoft Identity platform performs identity and access management (IAM) only for registered applications. This application will authenticate and authorize your application to call the Microsoft Graph API.
The Microsoft Graph API allows you to manage resources in your Microsoft Entra ID for users directory. It uses OAuth2.0 as the authentication framework and JSON response formats as output.
Logpoint integrates API endpoints for Entra ID Audit, Entra ID Identity Protection, Microsoft Defender XDR Alerts, and Incidents through Microsoft Graph API.
Why Entra ID Audit logs?
Entra ID audit logs offer a comprehensive report detailing user activities and sign-ins within an Entra ID tenant. Using the Microsoft Graph API to fetch these audit logs into Logpoint, organizations can analyze and investigate audit events related to changes in applications, groups, or users within Microsoft Entra ID. For each user account, you can access a complete set of audit logs with different events related to their identity and detailed sign-in logs to see which apps they have recently signed into, along with their locations.
What sets the Entra ID audit logs accessed via Graph API apart from the Office365 management API logs (available in Logpoint through the Office365 fetcher) is the inclusion of detailed risk information related to user sign-ins. This includes the risk status of a user, the risk level associated with a user during sign-in, and a summary of the risk event type. Additionally, it accurately categorizes changes in any resources- whether users, groups, applications, directories, or roles- across all applications within a tenant and identifies which service initiated the change.
Why Entra ID Identity Protection logs?
Entra ID Identity protection is a tool to identify risk through user sign-ins and unusual behavior. It assesses sign-in risk both in real-time and offline. For example, if someone from another country has stolen your credentials and is trying to use your account, it can block them.
Behind the UI, powerful Microsoft Graph APIs can provide information on risky users, risky sign-ins, or just the underlying detections. Automated remediation policies can be used to deal with risks, or using Graph API, these risk events can be seamlessly integrated with Logpoint for further investigation. This integration facilitates in-depth investigations within Logpoint, leveraging the intelligence derived from Entra ID Identity Protection to perform analysis on events such as the following:
- High-risk user behaviour
- Malicious IP Address Detection
- Anonymous IP Address Usage
- Unusual login activity
- Unusual Admin Activity
- Risky Sign-in Patterns
Why Defender XDR Alerts and Incidents logs?
Microsoft Graph security API provides a unified interface for pulling and investigating alerts and incident information from applications that are either part of or integrated with Microsoft 365 Defender. Alerts represent potential security warnings about suspicious activities identified by multiple security services within a tenant. An incident is a collection of related alerts that explains an entire attack story, thereby providing the broader context of the attack.
What is Universal REST API Fetcher (URAF) in Logpoint?
Universal REST API Fetcher (URAF) is a platform designed to address the need for a fetcher capable of supporting data sources accessible through RESTful interfaces.
By providing a custom log source template in URAF, Logpoint has integrated Microsoft Graph API, eliminating customers needing to go through the integration process. Logpoint’s URAF and Graph API can fetch logs across different Microsoft services. Recognizing the significance of threat monitoring, Logpoint has integrated endpoints related to Entra ID Protection, Entra ID users' audit logs, and Microsoft Defender XDR unified Alerts and Incidents through Microsoft Graph API endpoints for analysis, correlation, investigation, and remediation. To successfully fetch logs from these endpoints, an application must be registered in Entra ID, and necessary permissions must be granted to Microsoft Graph to access the endpoints planned to be used.
Here are the different endpoints used, the permissions needed, their corresponding Microsoft service whose logs the endpoints provide, and the Microsoft Entra ID license required:
| API Endpoints | Minimum Permissions needed | Microsoft Source | License Required |
|---|---|---|---|
| List Alerts_v2 | SecurityAlert.Read.All | Microsoft 365 Defender | None |
| List Incidents | SecurityIncident.Read.All | Microsoft 365 Defender | None |
| List directoryAudits | AuditLog.Read.All | Entra ID | None |
| List audit sign-ins | AuditLog.Read.All | Entra ID | Microsoft Entra ID P1 or P2 license. Note: Only those with a P2 license |
| List riskDetections | IdentityRiskEvent.Read.All | Entra ID Identity Protection | Microsoft Entra ID P2 license. |
| List riskyUsers | IdentityRiskyUser.Read.All | Entra ID Identity Protection | Microsoft Entra ID P2 license. |
How to Configure Microsoft Graph in Logpoint?
If you want to start ingesting data from Microsoft Graph endpoints, you must first register an application in Microsoft Entra ID. You can always read our technical documentation about configuring Microsoft Graph, which also explains how to create a Graph API application and assign permissions in the Azure Portal.
Since the permissions require admin consent, an administrator must approve all permissions before the source can be used.
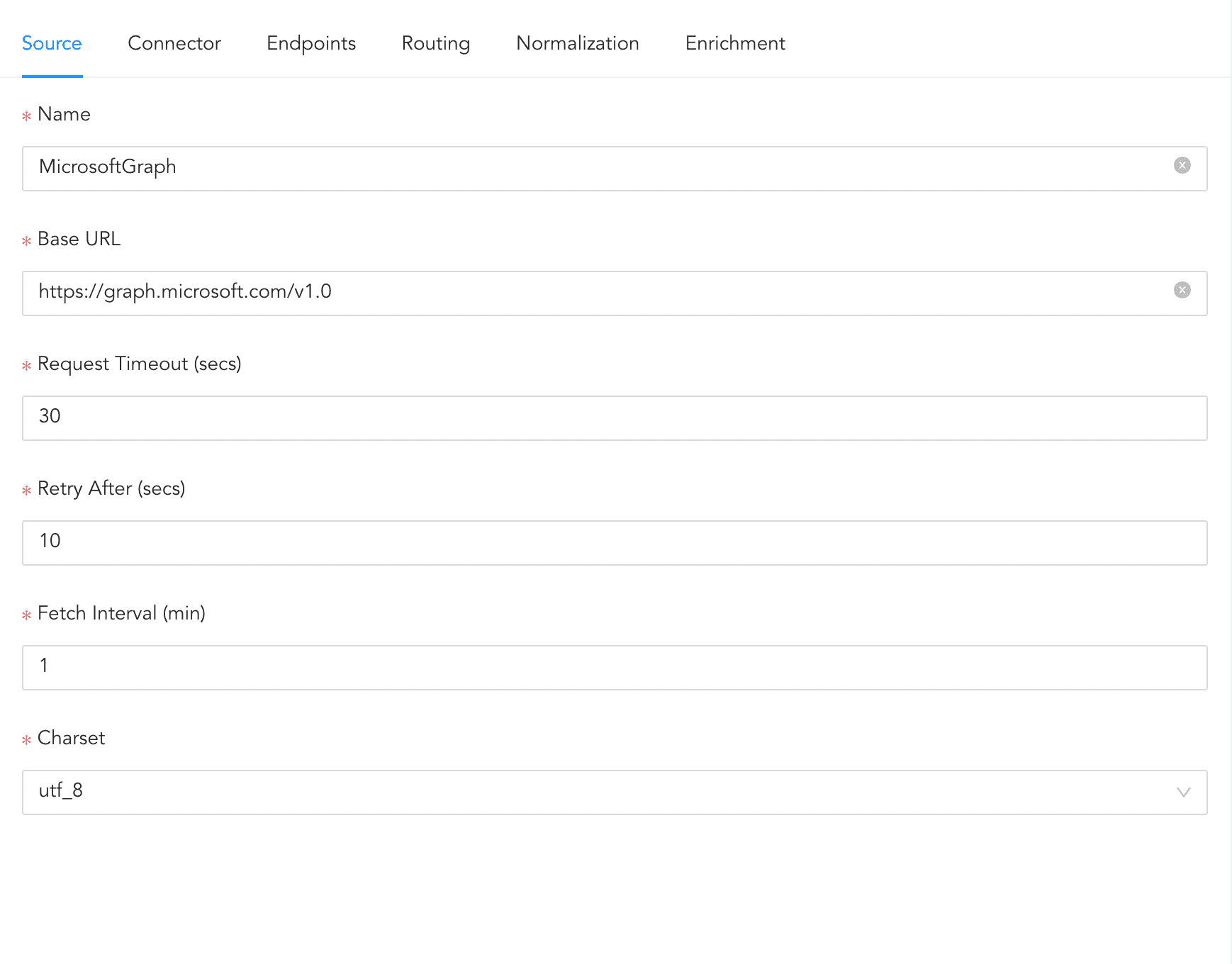
After the Microsoft Graph application registration, you can refer to the following steps to configure the MicrosoftGraph log source template on Logpoint:
-
From the Logpoint Service Desk, download the latest version of the Microsoft Graph API custom application.
-
In Logpoint, go to Settings >> System Settings from the navigation bar and click on Application. Import the .pak file of the downloaded application.
-
Go to Settings >> Log Sources from the navigation bar and click on Browse Log Source Templates. Then, search and click MicrosoftGraph.
-
Provide the tenant ID, client ID, and client secret to authenticate with OAuth 2.0 credentials.
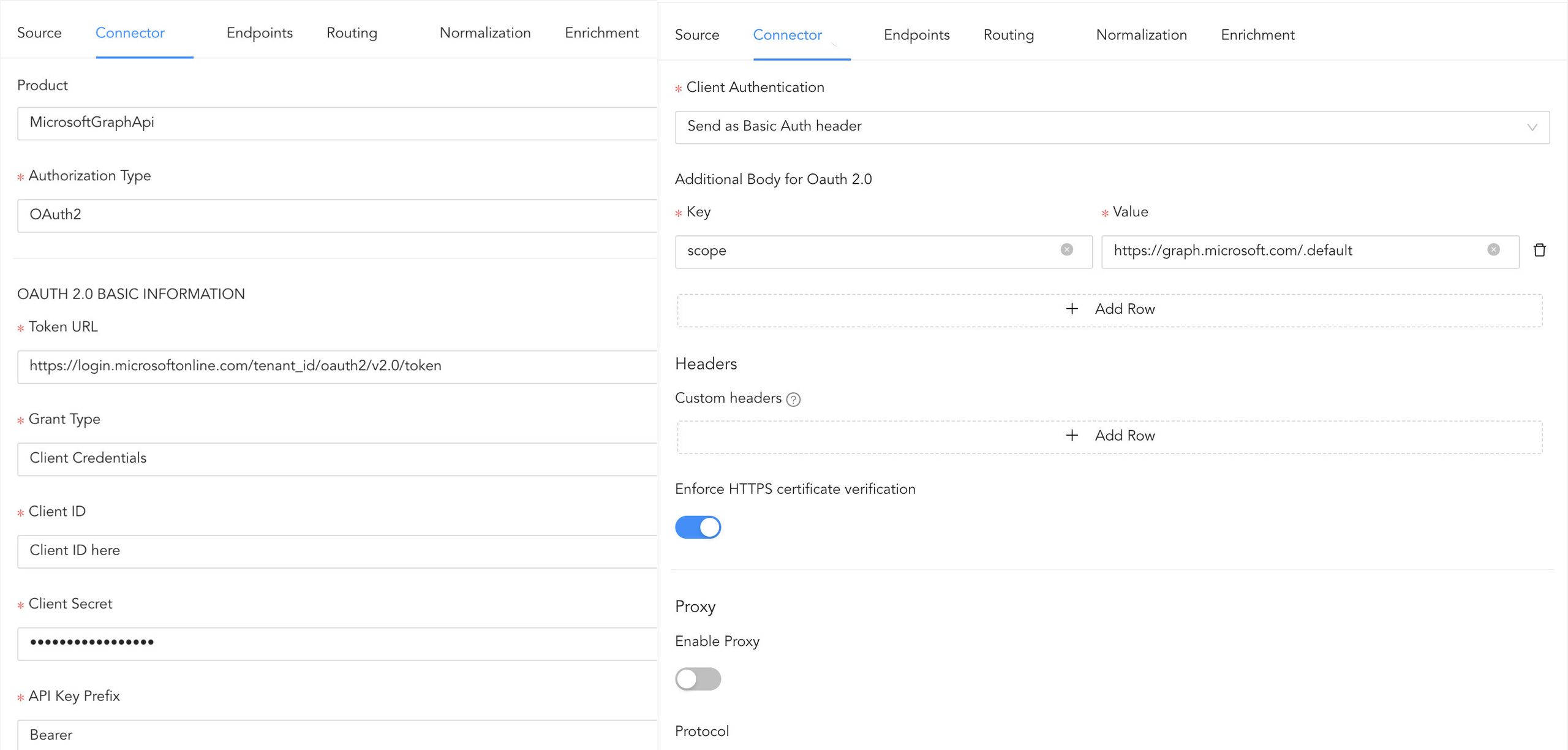
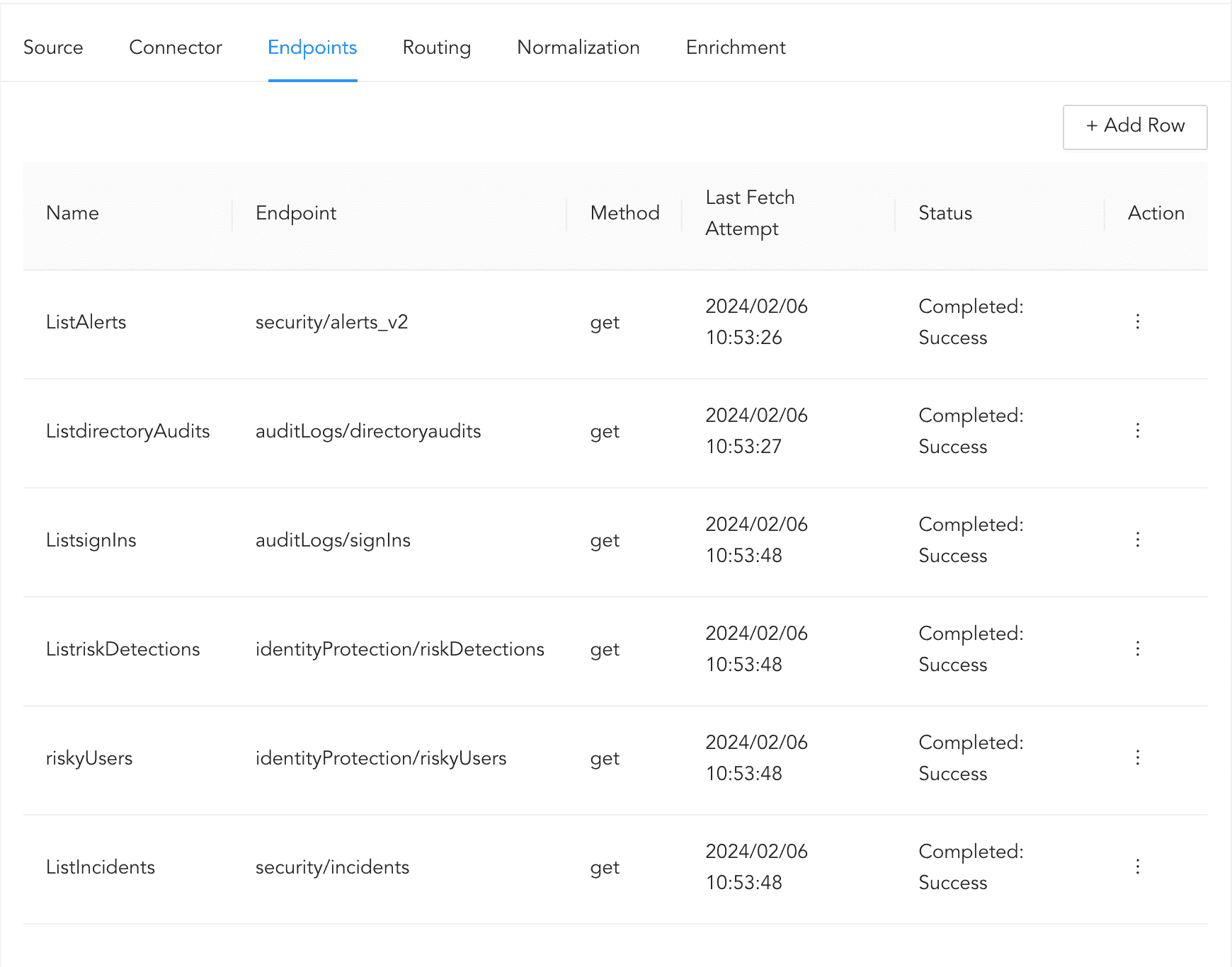
In addition to the endpoints that are available out of the box, the riskyUsers endpoint has been added to the MicrosoftGraph log source template.
-
Add a new Repo or choose an existing Repo to store the Microsoft Graph API logs.
-
The Normalization and Enrichment are preconfigured in the log source template.
-
Click on Create Log Source.
Threat Rules using Microsoft Graph API
Logs fetched by URAF from the Microsoft Graph API endpoints can be utilized to create security use cases using Logpoint’s own search query language. Search query enables the implementation of dashboards, search templates, alert rules and reports as analytics component for Microsoft Graph, allowing for real-time interpretation and analysis of security information to identify potential threats. These analytics provide timely warning, helping analysts to investigate further and take appropriate actions against compromised users or devices.
In addition to out-of-the-box analytics provided by Logpoint, information fetched from the API endpoints can create more analytics to detect and monitor potential threats. Here are some search queries that leverage information from the Graph API endpoints:
365 Defender Suspicious Event Detection
This query lists any new alerts with high severity triggered on the 365 Defender platform.
Entra ID Protection Risk Detection
This query lists any identity protection risk detection event generated at a high-risk level. It requires either a Premium P1 or a P2 license, with a P1 license having access to a limited number of risk information.
In Entra ID Identity Protection, risk detection refers to identifying suspicious actions related to user accounts in the Azure directory. Two types of detections - real-time and offline- can be detected at the user or sign-in level.
Entra ID Protection Suspicious Inbox Forwarding
This query lists suspicious email forwarding rules detected using information provided by Microsoft Defender for Cloud Apps.
Entra ID Protection Atypical Travel Detected
The result of this query indicates that two sign-ins of the same user originating from geographically distant locations were identified. Tracking past behavior, Microsoft might consider at least one of these locations as atypical.
Entra ID Protection Login using Leaked Credentials
This query lists events where the user's valid credentials have been leaked. The Microsoft leaked credentials service compares user credentials obtained from various sources with the current valid credentials of Microsoft Entra users to identify any valid matches.
Entra ID Protection Impossible Travel Detected
This query includes events where Identity Protection has identified two user activities originating from geographically distant locations within an interval shorter than the time it takes for that user to travel from one location to another, indicating that the credentials are compromised. Microsoft Defender discovered this risk for Cloud Apps.
Entra ID Protection Login from Malicious IP Address
This query lists events where ID Protection has identified logins from IP addresses flagged as malicious at the sign-in time.
Entra ID Protection Anonymous IP Address Usage
This query lists details of users whose accounts were active from an IP address identified as an anonymous proxy IP address.
Microsoft Graph Audit Activity Monitoring
The search queries below employ audit logs of Entra ID users that sign in to or attempt to sign in to Microsoft applications.
Entra ID Unusual Login Activity
The output of this query indicates that a user account made multiple failed attempts with an incorrect username or password before successfully signing in, indicating a potential brute-force attack.
Entra ID Failed User Authentication
This query lists the reasons for users' failed authentication.
Entra ID Protection Suspicious Resource Usage
This query correlates events from directory audits and sign-ins to track instances where a user with high risk at the time of sign-in has exploited any application.
The details for the field risk_level_during_sign_in are only available for those with a Microsoft Entra ID P2 license. All others are returned "hidden".
Analytics in the form of Report
Logpoint can easily organize and compile analyzed events, information, and findings in the form of reports. To facilitate each use case, analysts can create report templates using search queries which gives a comprehensive overview of what happened in an organization within a specific time range.
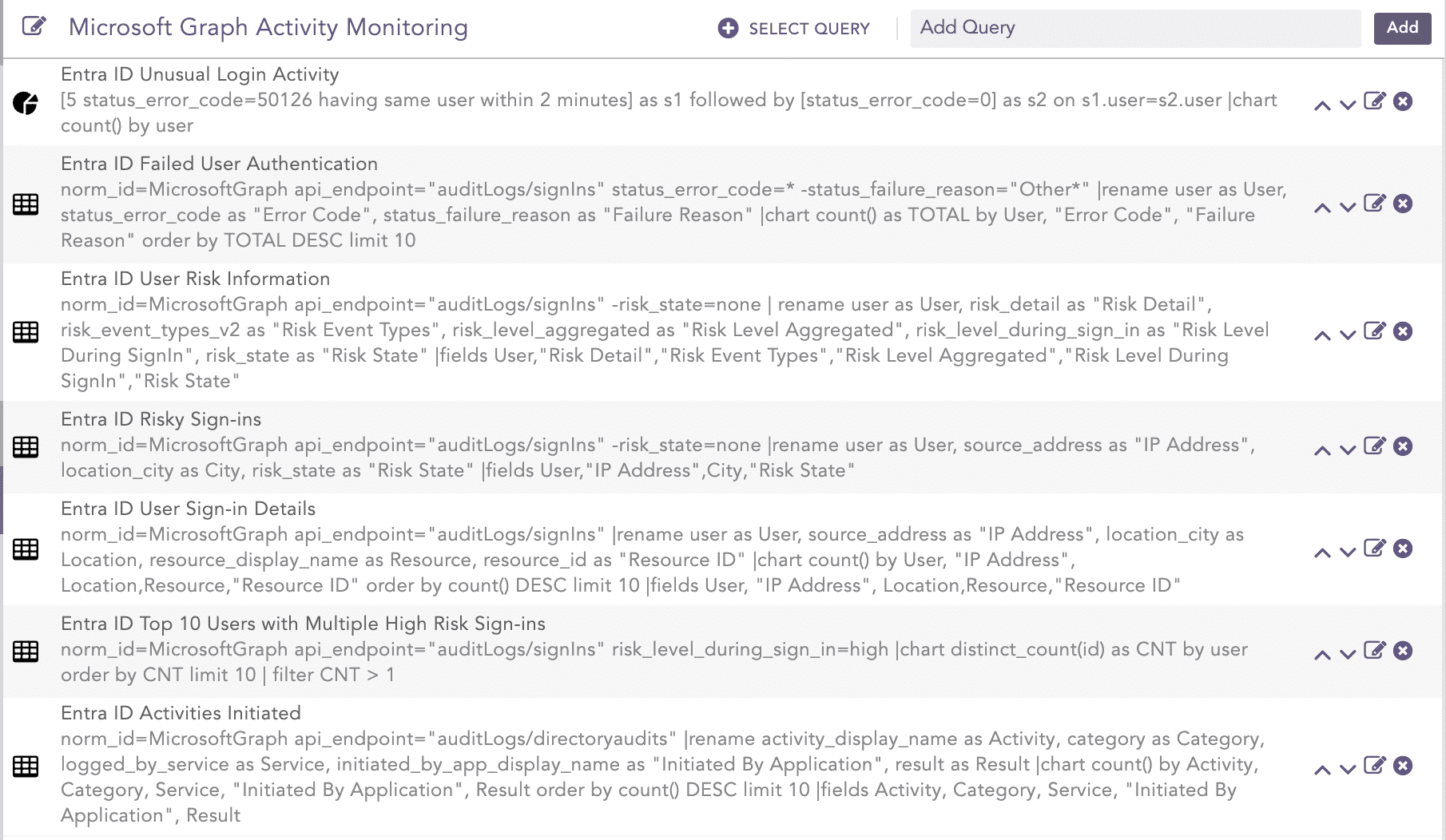
Microsoft Graph Activity Monitoring
Entra ID Protection Risky Users Detail
This query returns details related to a risky user, such as whether the user is deleted, whether the user’s risk state is being processed, the state of a user’s risk, and the level of the detected risky user.
Entra ID User Risk Information
This query reports the reason behind a specific risk state, risk event types associated with a sign-in, aggregated risk level, risk level during sign-in, and the sign-in risk status.
Note: Information on riskDetail, riskLevelAggregated, and riskLevelDuringSignIn is only available for users with a Microsoft Entra ID P2 license.
Entra ID Risky Sign-ins
The output of this query represents the risk associated with each user sign-in and the IP address and location from where sign-in was initiated. This helps identify potential risky sign-in attempts to enforce risk-based policies, ultimately securing organizations from hazardous login attempts.
Entra ID User Sign-in Details
This query keeps track of the most frequent sign-ins performed by any user, including resources each user has signed in to.
Entra ID Top 10 Users with Multiple High-Risk Sign-ins
This query reports the users whose sign-in was categorized as high-risk during multiple sign-in.
Note: Details for this property are only available for Microsoft Entra ID P2 license. All others are returned "hidden".
Entra ID Activities Initiated
This query indicates the activities performed most often, the resource category targeted by the activity, the service initiating the activity, and the application initiating the activity. Services initiating the activity include self-service password management, core directory, and B2C. This table helps monitor system activity records and keep track of any changes in users, groups, or applications.
Integrating Microsoft Entra ID and Microsoft Defender XDR events with Logpoint via the Microsoft Graph API provides comprehensive security monitoring and threat detection. Organizations can enhance their visibility into user activities and potential threats within the Microsoft 365 ecosystem by leveraging detailed audit logs, risk assessments, and incident data.
The capabilities provided by Logpoint's Universal REST API Fetcher (URAF) and custom log source templates streamline the process, ensuring that security teams can focus on analysis and remediation rather than integration complexities. The detailed analytics and reports generated from these integrations offer actionable insights, allowing organizations to address security risks and safeguard their critical assets proactively.




