Threat hunting. What do you know about it? You hear it and read about it, but how much do you actually know? Not all threats simply present themselves to you, they don’t wear bells and whistles, or sing and dance, which would negate the whole point of the attackers remaining undetectable. Year on year, actually day by day, the number of threats in circulation is off the chart.
By the third quarter of 2022, there were approximately 15 million data breaches exposed worldwide — a 37% increase from Q2 of 2022.
These types of headlines about cyberattacks and insider threats have become increasingly common. Cybercriminals will stop at nothing to gain critical data from organizations of all sizes, as well as individual consumers using the internet. They’ll grab passwords, personal information, social security numbers, company secrets, and anything else of value.
As long as there is precious data out there, we can expect these sophisticated attacks to increase exponentially. That’s why it’s not enough to simply be reactive — you must be proactive in safeguarding your organization’s data, trade secrets, and other personal information.
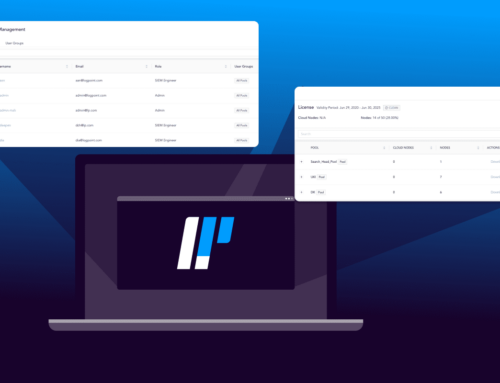
Here’s an example of how to use Converged SIEM to threat hunt.
What exactly is threat hunting in cybersecurity?
Put simply, threat hunting is the practice of proactively searching for undetected cyber threats in a network. Cybersecurity professionals and software will dig deep to find any malicious actors in your organization that was able to slip past your endpoint security defenses.
Once a malicious actor sneaks in, they can hide within a network for months on end. Here is where they become an insider threat, quietly collecting data, scanning for confidential materials, and collecting login credentials that will enable them to move laterally across an entirely digital environment.
Once a cybercriminal is successful in evading an organization’s detection measures and penetrating all defenses, it’s up to the organization to stop the threat from the inside. Unfortunately, many organizations lack the advanced detection capabilities needed to locate and terminate the threat from their network, which is why threat hunting has become an essential component of a comprehensive cybersecurity defense strategy.
How does threat hunting work?
The process of threat hunting begins with the assumption that there are already one or more insider threats in a network. An official investigation is then initiated to detect any unusual behaviors that would indicate the presence of a malicious actor.
This investigation is broken down into three primary categories:
-
A hypothesis-driven investigation — Typically triggered by a new threat that’s been identified through a pool of crowdsourced attack data. This data provides insight into cybercriminals’ latest TTPs (tactics, techniques, and procedures). From there, the threat hunters will scan the network for specific TTP behaviors to detect any threats.
-
An investigation based on Indicators of Compromise (IoCs) — IoCs or Indicators of Attack (IoAs) are cataloged as part of tactical threat intelligence. Threat hunters can refer to and use IoCs or IoAs to uncover potential insider threats and ongoing malicious activity.
- An advanced analytics and machine learning investigation — This part of the process involves combining powerful data analysis and machine learning software to comb through a large amount of information and detect any irregularities that may suggest malicious activity. These are the anomalies that turn into hunting leads and are investigated by experienced and skilled analysts to identify sophisticated threats.
All three components of the threat-hunting process require both human effort and threat intelligence resources, such as advanced security technology, you can really take the human effort out of the equation with automation. Throughout the entire process, threat hunters gather all the information they can about malicious activities, TTPs, and goals. Once the threat is identified and analyzed, the intelligence gathered is brought to the security team so they can terminate the threat.
The intelligence is also used to determine new trends, eliminate the current vulnerabilities within a network, and make the appropriate predictions to enhance the network’s overall security and protect against future attacks.
Examples of threat hunting
To give you examples of threat hunting in session you can go no further than our Emerging Threats and Security Analysis examples. There is a ton of ransomware attacks out there. Every month we release blogs and full reports which include mitigation strategies and also, playbooks for you to use to automate your processes. Check out these:
Security Analysis:
Emerging Threats blog, reports, including playbooks:
What tools should you use for threat hunting?
As mentioned above, threat hunting requires advanced security technologies to identify and assess malicious activity appropriately. When it comes to the best tools for the job, a consolidation including SIEM, SOAR, UEBA, Endpoint security such as AgentX, plus SAP system and application security such as BCS for SAP will stand the test.
For example, Logpoint uses a proprietary Converged SIEM tool to collect, analyze, and prioritize security threats to assist with the analysis and identification of malicious behavior. This also helps to terminate and resolve insider threats much quicker to keep businesses up and running safely.
The Converged SIEM platform is arguably the best tool to use for threat hunting. It has everything your threat-hunting team needs in one place.
Contact us today to learn more about our fully integrated Converged SIEM.
Or take a product tour to see how our comprehensive threat detection response technology works for you.