Originally posted July 2019 – Updated October 2023
Threat hunting is gaining relevance by the day as organizations try to navigate through an ocean full of threats – attempting to identify and address incidents their systems have missed. There are three categories of threat hunting: Known attacks based on Indicators of Comprise (IoC) and Indicators of Attack (IoA), proactive search based on framework such as the MITRE ATT&CK, and the detection of abnormal behavior with machine learning, such as UEBA.
Logpoint’s security operations platform, Converged SIEM, comes with extensive threat-hunting capabilities, including advanced analytics, enrichment, correlations, UEBA, and reporting. They strengthen your agility in triage, investigation, and response from one single platform and your overall security posture.

Go To Section
Converged SIEM also uses threat intelligence feeds to automate some aspects of threat hunting by providing ready-to-use alerts and dashboards. Threat intelligence feeds are used at the time of ingest so that when data enters the platform, it’s evaluated against all known configured threat intelligence feeds.
Threat intelligence is also used at the time of analysis, allowing analysts to submit any amount of historical data to be evaluated against the most recent threat intelligence feeds, to see if they match any new knowledge about attacks. These correlated and evaluated alerts can then be pushed to a third-party incident response tool for orchestration and remediation.
Converged SIEM’s incident response integrations provide automated workflows for business context enrichment, threat intelligence, and correlation of log data with network data. Based on your organization’s workflow, your security team will be empowered to gather evidence, build the case, and remediate efficiently.
To demonstrate how Threat Hunting actually works, we’ve put together this use case.
What features in Converged SIEM help in threat hunting?
The search console can become a powerful ally when looking for threats. Here the threat hunter will start with simple queries to show all matches for a specific data label. For example, the security analyst can start by typing label=malware.
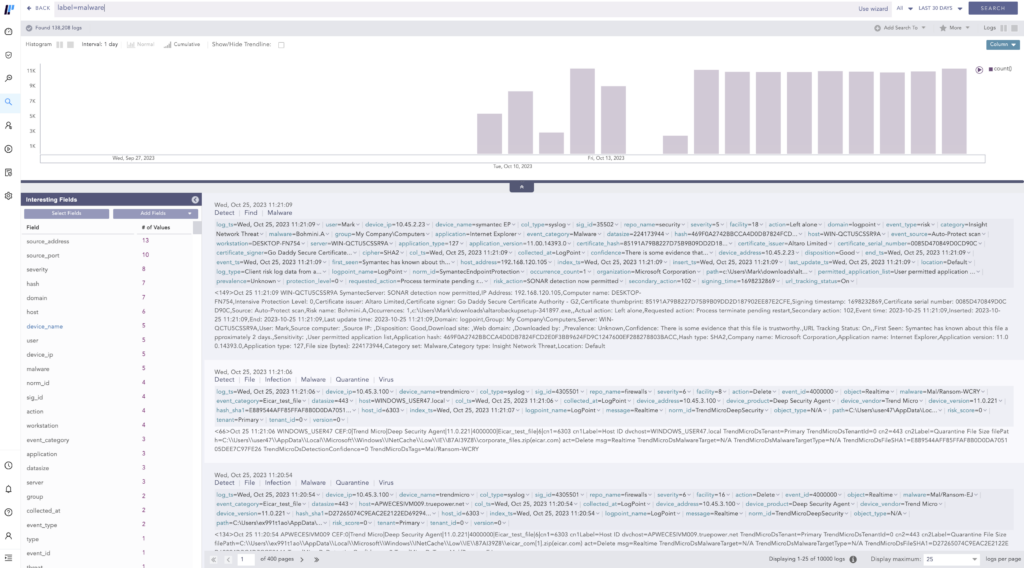
In addition, incident responders can benefit from third-party data on threat intelligence to move forward in the hunt. Converged SIEM gives analysts the ability to import lists of malicious URLs, hashes, IPs, IoCs, etc., to the platform to save time during the threat-hunting process.

With access to this threat intelligence now saved in the platform, analysts can retrieve a series of known bad hashes. These lists of enriched data from a third-party provider can also be used to find logs that are considered risky by cross-referencing against them URLs, hashes, IPs, amongst others, during the query.
Step 1: Setting the scene
To start looking for file infections, the analyst can run a simple query: label=Detect label=File label=Infection | chart count() by sender,sender_domain,hash, receiver
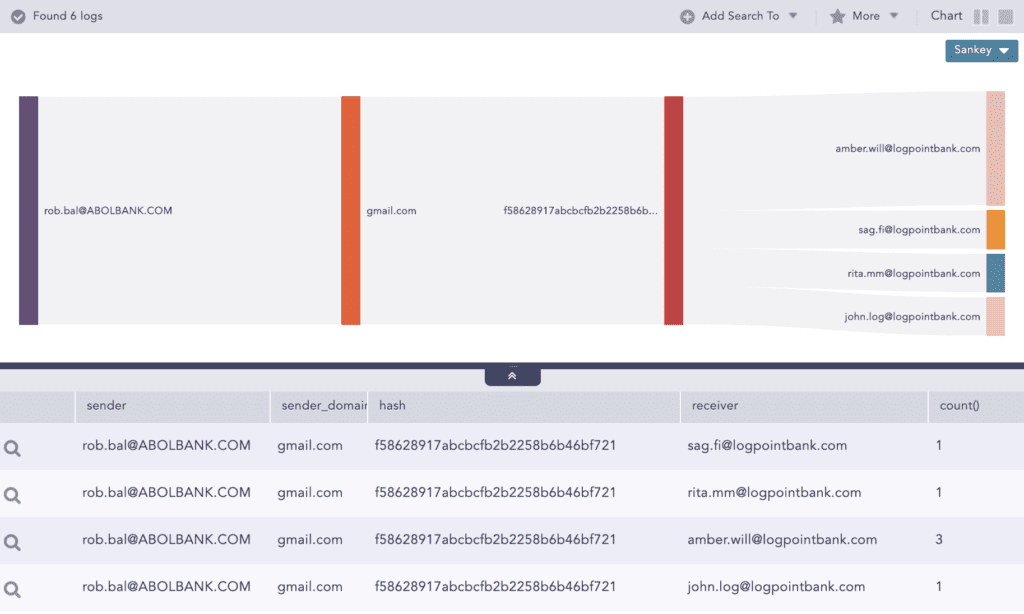
After that, they can drill down on the first row and identify the checksum.
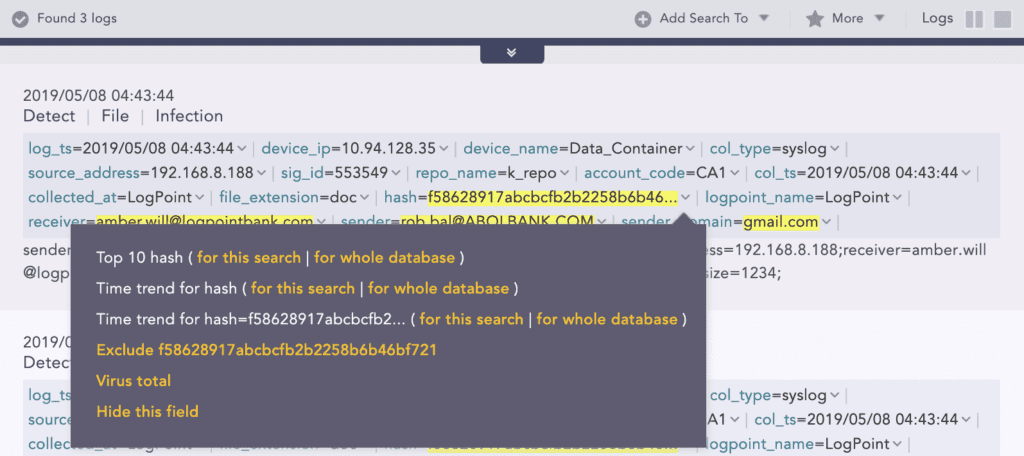
With that in mind, they can use the checksum to drill back to Virus Total.
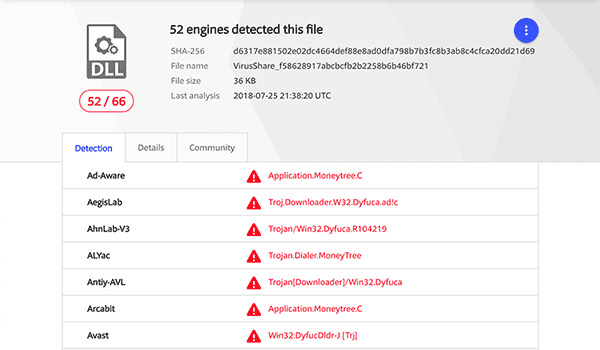
After finding out that several engines detected a malicious file, the incident responder raises the flag and realizes that further investigation is required to look into the impacts of the infection.
Step 2: Raising an incident
The analyst starts by creating an incident for follow-up directly from the search.
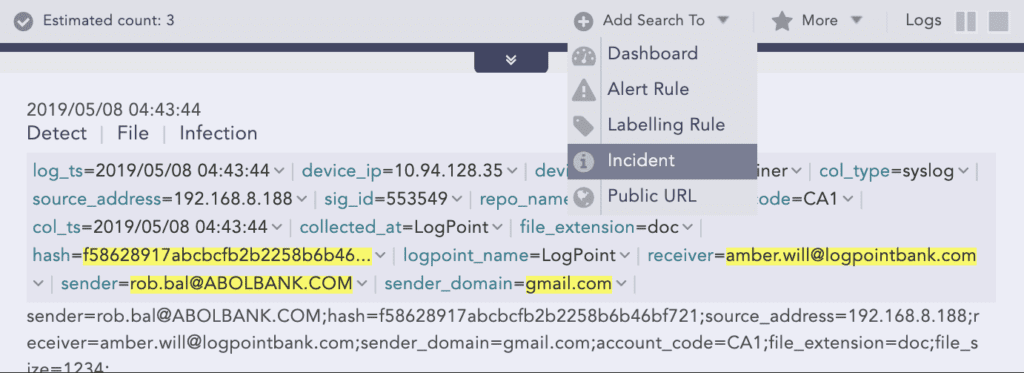
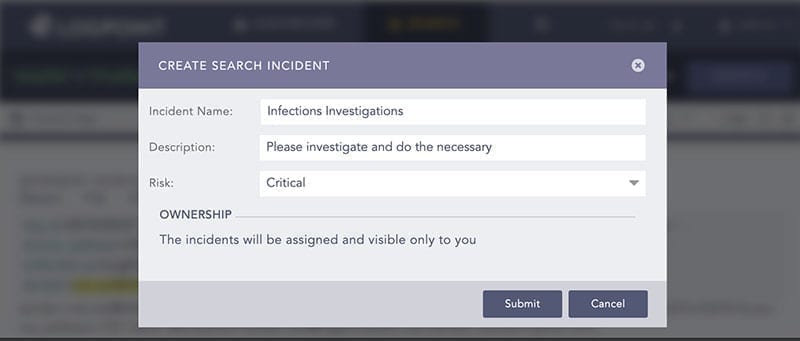
The incident will be listed under Investigation > Incidents together with all the other incidents created.
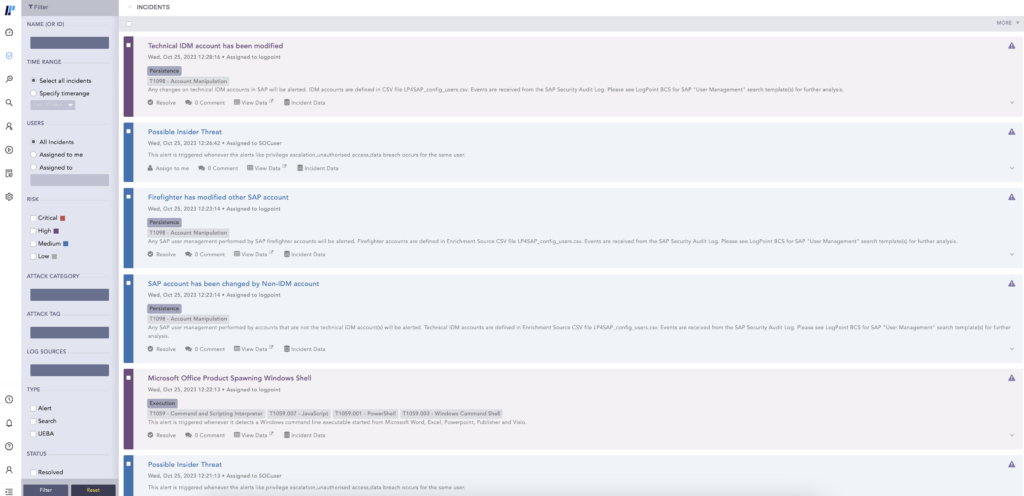
Step 3: Starting the investigation
Now it’s time for a deep dive into the investigation of the incident. The incident responder applies the identified hash as the filter.
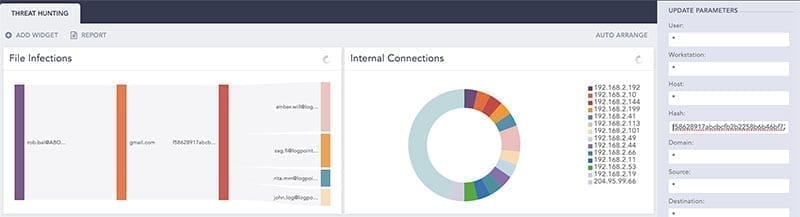
Then they pick each user associated with the recipient emails. It shows that the user Rita performed several failed login attempts to various servers.
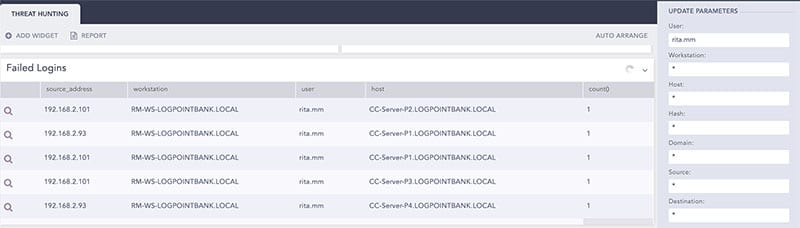
Moving to the search page, the incident responder can see the details and find out more about failed login attempts for specific users by querying: label=Login label=Fail user="rita.mm" | chart count() by source_address,workstation,user,host order by count() desc
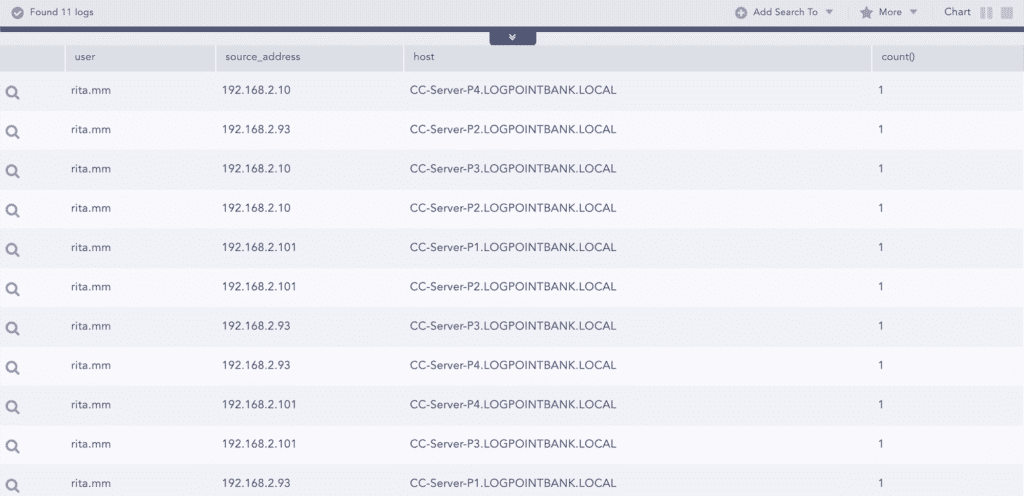
After this, they pick one the source IPs used by user Rita to check if there are other failed attempts or not. With another query, they can get the failed login attempts for specific sources: label=Login label=Fail source_address=192.168.2.101 | chart count() by source_address,workstation,user,host
In this case, the analyst can see that there is one different user with 4 failed attempts coming from the source 192.168.2.101.
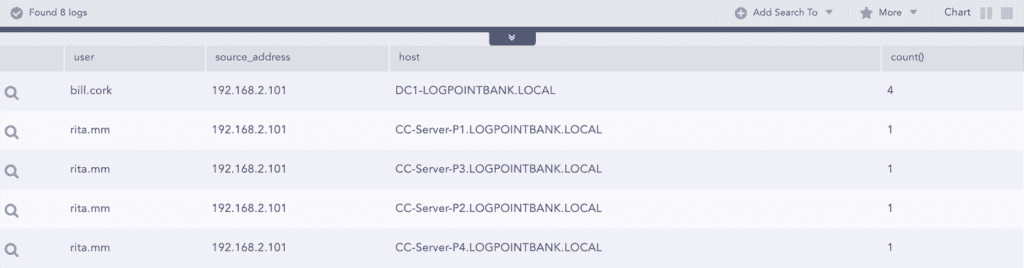
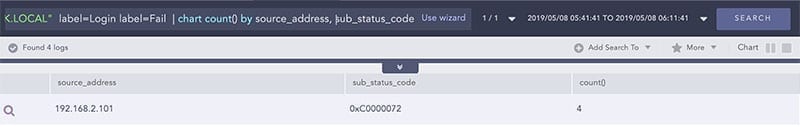
To get more information, the analyst drills down on this event and now queries for that user with failed login attempts on multiple filters by failure sub status: user="bill.cork" source_address=192.168.2.101 host="DC1-LOGPOINTBANK.LOCAL" label=Login label=Fail | chart count() by source_address, sub_status_code
By doing that, they observe that a disabled account is trying to log in to the Domain Controller and that the sub status code 0xC0000072 actually relates to login failure on a disabled account.
Now, the next step is to go back to the search template and check for Indicators of Compromise (IoCs) associated with source 192.168.2.101.
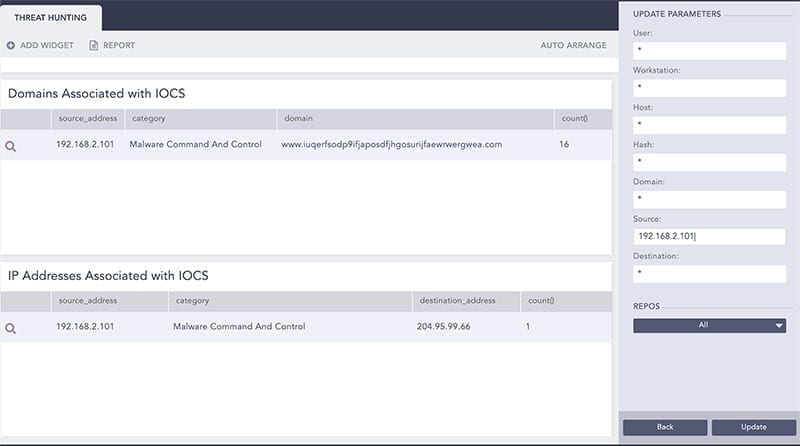
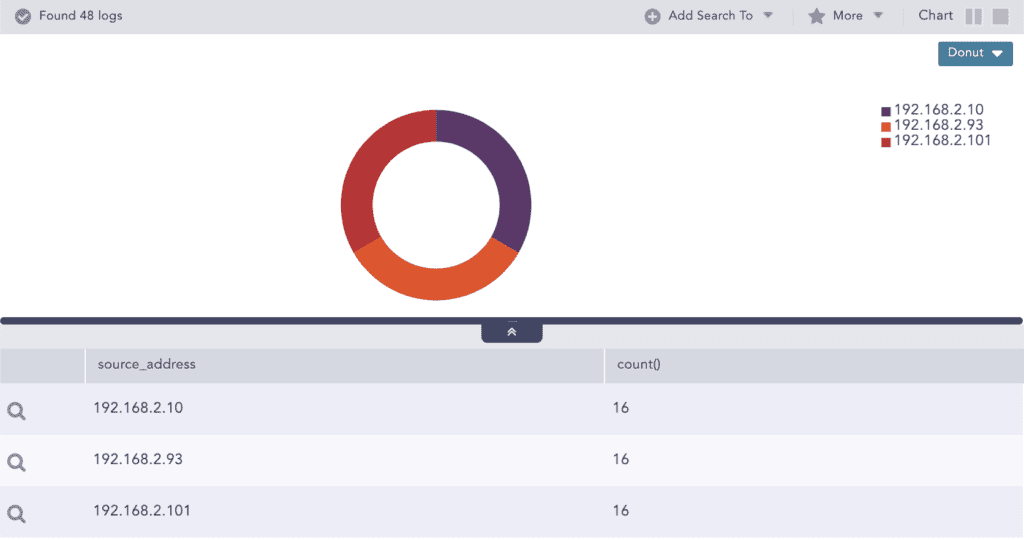
Here, the analyst drills down on the category for malware command and control to check other source addresses associated with it and runs the following query: category="Malware Command And Control" | chart count() by source_address
Step 4: Remediation/Reporting
During the process of threat investigation, the analyst identifies that the user Rita is compromised and should be disabled while the user Rob should be deleted if not to be enabled in the future.
The analyst continues further investigations on the incident to validate if there were any activities of the identified threat indicators in the past. The query used is to find threat indicators for malware command and control appended to the list: category="Malware Command And Control" | chart count() by destination_address | process toList(ACTIVE_IOCS,destination_address)

Finally, the incident responder searches historical events for any activities associated with the IPs in the ACTIVE_IOCS list by querying the following: source_address IN ACTIVE_IOCS OR destination_address IN ACTIVE_IOCS
It turns out that the infected systems should be cleaned and the firewall rule should be updated to block the connections to the “Command And Control Servers”.
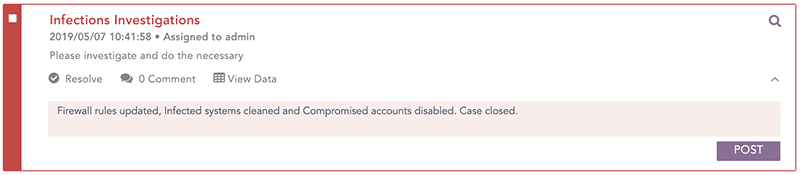
This is a great example of how threat hunting is carried out with Converged SIEM. Thanks to features, such as lists of threat intelligence, alert rules, and search templates, analysts can detect and hunt these threats.
Whether you proactively search for threats, address known indicators of compromise, or react to alerts from abnormal behavior in your network, Converged SIEM gives you the flexibility you need to perform threat hunting in whatever way it comes.
It’s impossible to have a system that detects every single threat, hence the importance of a good threat-hunting process and a platform that allows you to do it. Disregarding threat hunting is almost like disregarding your organization’s security.