Uncover more resources with Logpoint’s latest release
The cybersecurity industry is grappling with a massive shortage of skilled professionals while rising cyber threats and new regulatory frameworks are putting immense pressure on already stretched resources. This takes a toll on many SOC analysts, with 60% considering a career change due to burnout. But it doesn’t have to be this way.
As a result, more and more mid-size organizations resort to MSPs and MSSPs to outsource their security operations. However, these, too, experience similar issues and see themselves involved in a bid to offer a better return on investment for their customers to remain competitive.

Maximizing cybersecurity efforts and investments is crucial for both mid-size organizations that handle everything in-house and for MSSPs. So, what if cybersecurity teams could work smarter, not harder? Logpoint’s latest release empowers them by uncovering resources in critical areas such as compliance, incident investigation, and response. This way, organizations can optimize their existing resources, whether in time, expertise and skills, or hardware requirements.
Faster onboarding for faster time to value
Setting up a SEIM solution requires allocating sufficient time and resources to ensure success. Our latest version of Logpoint SIEM comes with a simplified, shorter, and more intuitive onboarding process. Time to value is key for partners, distributors, and MSSPs, who can quickly lower operational costs with less time and fewer resources required to support their customers’ onboarding.
Customers can choose between Advanced Configuration (Custom Configuration, Collector, and Syslog Forwarder) or Standard Configuration. In the latter, customers get a pre-configured compliance package, and they only need to select from which repositories the dashboards and widgets will get the data: firewall, cloud services, network, application, and servers.
After that, they’ll be redirected to the Log Source page to start creating their log sources. This reduces the time and allows MSSPs to quickly onboard standard customers with a process that works like a golden image for compliance.
More flexibility to comply with regulatory frameworks from the get-go
One of the most resource-consuming jobs for organizations is compliance. Yet, a one-size-fits-all approach to ever-evolving regulations is doomed to fail – especially when most of them are recipes that give instructions but not specific ingredients. SIEM providers must stay flexible to ensure their customers remain compliant and avoid fines and economic penalties.
The latest Logpoint SIEM gives newly onboarded customers in Standard Configuration total flexibility in the form of three easy-to-use dashboards for access management, incident management, and perimeter security monitoring. This allows them to monitor relevant information for several compliance frameworks.
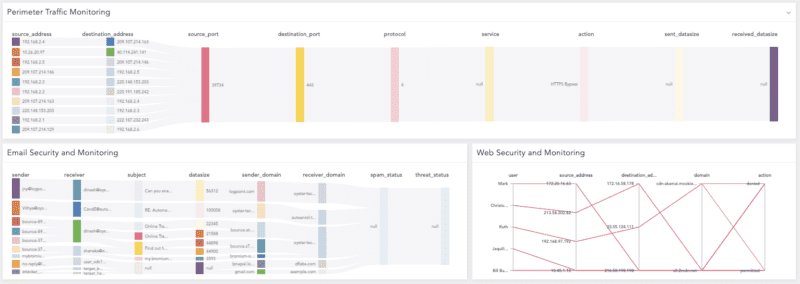
By focusing on critical compliance checks, security professionals reduce the overhead associated with monitoring the same data in multiple dashboards and the burden during compliance audits. It also allows organizations to remain agile and adaptable to new frameworks.
Shorter time to investigate and respond to incidents
The faster and more precise the investigation of a threat is, the less damage it can cause to the organization – ensuring business continuity or meeting compliance regulations that require a timely investigation to prevent fines. To help with that, the new Logpoint Case Management brings a whole usability revamp.
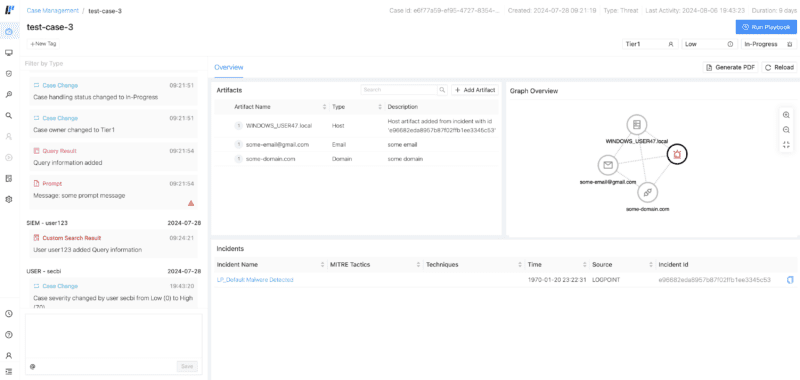
Analysts can now access the timeline, artifacts, incidents, and graph overview from one screen and easily add artifacts or work with labels. They can also perform prompt actions directly from the case without opening a playbook in runtime mode, cutting down the time spent on the investigation and response.
Increased incident responder’s productivity
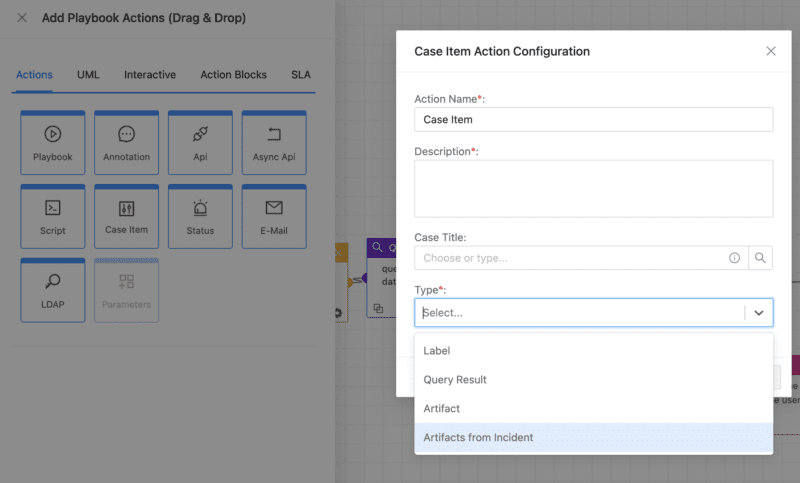
Playbooks serve as the blueprints for automated triage and incident response. Therefore, analysts must understand their dependencies and input and output parameters for more efficient and faster responses. Our latest release solves this.
By including playbook descriptions, we help analysts have clarity over the expected data and the results to be produced by the playbook. It’s not only about efficiency; knowing precisely what a playbook does allows for reusability. Users can clone and quickly adapt playbooks to match their use case. It also facilitates traceability in the case of an audit of incident response activities for reasons like compliance.
This release also includes more playbook actions to foster efficiency and time savings. Now, users can encode and decode HTML without developing a script. Another action allows them to update the case type from threat to risk and vice versa. Finally, analysts gain time and clarity by automatically adding incidents as artifacts to cases to see which incident triggered a playbook.
Save on hardware costs and get the most out of the existing ones
Hardware requirements represent a large portion of the costs that organizations must assume when using cybersecurity solutions. The ideal scenario combines better security, more stability, and fewer hardware costs –this is exactly what Lopgoint’s latest release brings to the table.
Performance improvements mean increased stability, and a reduced cost of operations will always offset other costs in your organization. That’s why, in this version of Logpoint SIEM, we managed to reduce the CPU load and CPU usage and, by doing so, reduce hardware requirements too, such as server and storage.
Logpoint customers can now get more for the same, allowing them to handle larger data sets, increase the number of log sources, and scale up their security when the organization grows.
Final thoughts on Logpoint’s latest release
Streamlining compliance efforts and reducing complexity allows for more focused threat investigation and response. This saves valuable time and reduces the risk of costly data breaches or financial penalties for compliance failure.
Moreover, optimizing resource utilization can lead to significant cost savings in hardware requirements, freeing up funds for other critical business investments.
Ultimately, maximizing resources in cybersecurity protects sensitive data and enhances overall operational efficiency and resilience.
Do you want to know more about Logpoint’s latest release? Reach out to your Logpoint representative.




