Uncovering illegitimate Crypto-Mining Activity (Cryptojacking) in the Enterprise: Utilizing Network Logs for Investigation and Remediation
By Swachchhanda Shrawan Poudel, Security Research
Contents
TL;DR
Cryptocurrency mining is a process of using specialized software to solve complex mathematical problems in order to validate transactions on a cryptocurrency network and create new units of the currency. However, it can be resource-intensive, so some malware actors have turned to malware to covertly install cryptocurrency mining software on the computers of victims in a bid to generate profits. This type of malware is often referred to as “cryptojacking” malware. Cryptojacking is growing in popularity and recent reports suggest that there has been a sharp increase in crypto-miner variants in Q3 2022, with a growth of over 230% compared to the same period in 2021. Furthermore, the research claims that the first quarter of 2022 saw the biggest number of users afflicted by fraudulent mining software, with over 500,000 individuals affected.
** Get research and analysis, insight, plus hints and tips, on how to mitigate cryptojacking in the main blog below. Head to the contents and click each section for quick navigation.
Cryptocurrency mining is the process of using specialized software to solve complex mathematical problems to validate transactions on a cryptocurrency network and create new units of the currency. It can be a resource-intensive process that requires significant computing power. As a result, some malware actors have turned to malware to covertly install cryptocurrency mining software on the computers of victims in a bid to generate profits.
This type of malware is often referred to as “cryptojacking” malware. Since it is resource-intensive malware actors have been also targeting organizational cloud resources for coin-mining purposes. A recent incident as reported by Stephan Berger on his official Twitter handle was where a Threat Actor (TA) compromised an Azure Global Admin Account, which they used to spawn up over 200 (Virtual Machines) VMs to mine cryptos with it. Due to a lack of detection capabilities, it was only noticed due to extreme Azure costs.
Crypto mining fast facts
-
Prominently growing over time, with more than 500,000 individuals affected only in 2022 according to Kaspersky reports.
-
Uses the processing power of the victim’s computer illicitly to mine cryptocurrency, allowing cybercriminals to remain hidden for months.
-
Become a profitable criminal activity, with an estimated income that reaches up to $40,500 (2 BTC) per month.
-
In constant evolution, resulting in a higher difficulty to detect and a single/host-based method might not work for each case.
-
Typically discovered by monitoring excessive CPU or memory consumption on endpoint devices, but this becomes more difficult in cloud infrastructures.
The current landscape of crypto mining
Different cybersecurity reports and news suggest that cryptojacking is prominently growing with time. According to Kaspersky’s new research paper ‘The state of cryptojacking in 2022’, there has been a sharp increase in crypto-miner variants in Q3 2022, with a growth of over 230% compared to the same period in 2021. Furthermore, the research claims that the first quarter of 2022 saw the biggest number of users afflicted by fraudulent mining software, with over 500,000 individuals affected. Cybercriminals use these methods to remain hidden for months, using the processing power of the victim’s computer to mine cryptocurrency. Moreover, the Q3 of 2022 saw an increase in the distribution of mining software through the exploitation of well-known vulnerabilities which can be seen in the bar graph below.
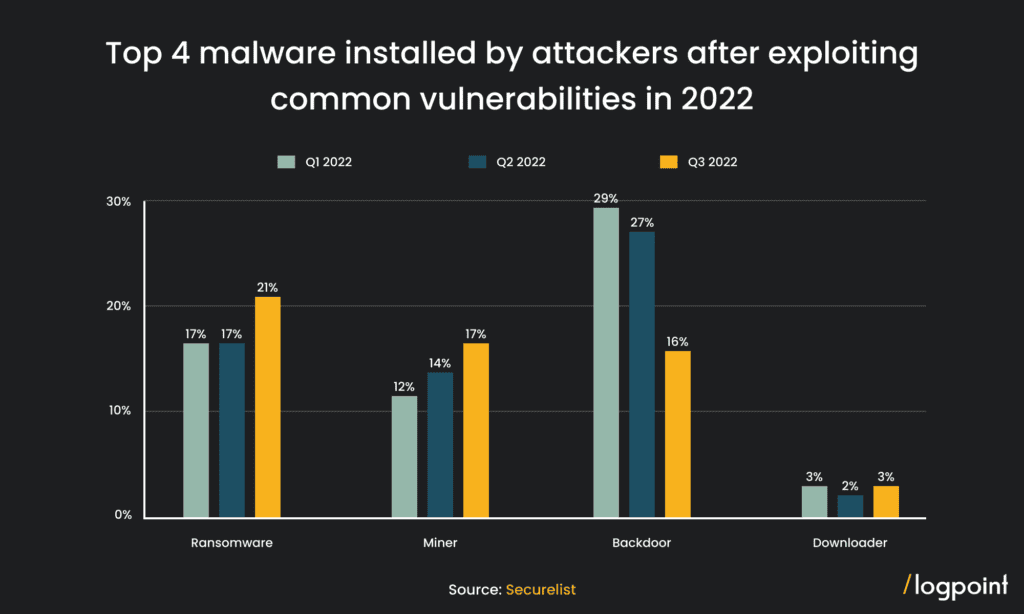
Fig 01. Top 4 malware installed by attackers after exploiting common vulnerabilities in 2022 (Source: Securelist)
Adversaries are also getting attracted to crypto mining which was shown by the Astralocker ransomware, which reportedly shut down its ransomware operation to pursue crypto-mining. TA could be attracted to mining for easy passive income with low risk as compared with ransomware campaigns as not all campaigns bring ransom to them.
How cyber-miners gain access to your system
The initial access techniques of Cyber adversaries for distributing crypto mining malware are consistent with those seen in other types of cyber-attacks, such as ransomware. Phishing emails, exploiting software and system vulnerabilities, and using compromised credentials are some methods used to gain unauthorized access to targeted networks.
Furthermore, cybercriminals may use malware distribution campaigns or exploit kits to deliver crypto-mining malware to unsuspecting victims. It is worth noting that these initial access methods are not limited to crypto mining attacks but are relatively widely used in various cybercrime operations. Unpatched vulnerabilities in software and systems are particularly dangerous as they provide an easy entry point for cybercriminals to gain access and deploy crypto-mining malware. For example, The “EternalBlue” exploit is one example of an unpatched vulnerability in windows that has been exploited for crypto-mining. Cybercriminals used the exploit to gain unauthorized access to a vulnerable machine before distributing crypto-mining software that mines for bitcoin utilizing the infected system’s computational capabilities.
It is not easy to pinpoint every Tactics, Techniques, and Procedures (TTPs) of a crypto-miner. The adversaries have been constantly evolving their ways of operation and will do so in the future for detection evasion purposes. Cybercriminals use various methods to mine digital currency without consent, one of which is the use of legitimate mining programs with open-source code. These programs do not contain malicious functionality on their own, but they can be used by malware to mine cryptocurrency without the user’s knowledge. This method allows cybercriminals to avoid detection and save resources on malware development.
Current detection of crypto mining
This is Why anti-virus alone can’t stop cryptocurrency mining. It requires more than a host-based detection tool. A defense in depth ideology is the best approach. By using a combination of security measures, including endpoint protection, network monitoring, and incident response capabilities, it is possible to detect a wide range of crypto-mining activity and mitigate the threat.
Despite the techniques employed to install/run, coin-miners are different, the major coin-mining activity is typically discovered by monitoring excessive CPU or memory consumption on endpoint devices. However, in the aforementioned case, detecting crypto-mining activities become far too complex when using Azure cloud infrastructure because it is more difficult to observe changes in system performance or resource utilization at the host level. It may have been spotted by deploying Azure activity logging and monitoring, as well as doing regular Azure account and resource audits and submitting logs to Logpoint SIEM.
However, the easiest and best alternative here for detection is Network traffic analysis which might have aided in the detection of this crypto-mining approach by identifying network traffic patterns connected with the crypto-mining activity. For example, launching a large number of VMs to mine bitcoin will almost certainly generate a big volume of network traffic, such as several outbound connections to certain IP addresses or domains. It would be feasible to detect and prohibit crypto-mining activity by monitoring network traffic for these patterns.
Further along in this article, we focus on the identification and treatment of crypto-mining malware using a mix of security mechanisms such as Logpoint AgentX for endpoint protection and a combination of Logpoint SIEM and SOAR for network monitoring and incident response.
Together, Logpoint SIEM and SOAR can provide the necessary visibility to detect and mitigate illegitimate coin miners in enterprise environments. Generally, organizations dealing with IT assets have firewalls, IPS/IDS, and DNS in place if not agents installed on every endpoint. We can aggregate all these network logs from these sources to Logpoint where we will then correlate the event to detect, investigate and remediate threats with Logpoint SIEM + SOAR.
Log Source Needed
-
Firewall
-
DNS
-
proxy
-
IPS/IDS
How to detect crypto mining with Logpoint
Irrespective of the infection chain, a crypto miner’s activity always leaves a trail that can be detected using network artifacts. This can usually be detected by investigating internal suspicious/malicious network traffics in relation to crypto-miner pools. We have compiled the list of known coin miners’ IP addresses and domains as follows.
Required IoCs (Updated as of January 2023)
-
COIN_MINER_IPS
-
COIN_MINER_DOMAIN
-
COIN_MINER_DNS
The IoCs can be downloaded from the Logpoint service desk and were released prior to the release of this article. These lists need to be installed in Logpoint to use in this query.
A step-by-step crypto-mining detection in Logpoint
Considering the massive attack of Stephan Berger on Twitter, we simulated a similar attack in our lab to guide a potential step-by-step investigation using Logpoint.
In the given case study, the coin miners had a distinctive user-agent, “miner“ in each of their requests. Using any available firewall or proxy logs, we can check for common user agents that might be used by a tool or a script.
According to this sigma rule, we can detect suspicious user agent strings used by crypto miners in proxy/firewall logs as follow.
An Intrusion Prevention/Detection System (IPS/IDS) like Suricata and Snort can analyze network logs to detect if a system is involved in coin-mining activities. It does this by looking for large amounts of outbound connections from a single system, unusually high levels of network traffic, unusually long connection times, and specific protocols associated with coin mining. Using Logpoint, we can investigate a potential mining activity in the enterprise network through IPS/IDS logs.
It can be seen that the endpoint is communicating with specific addresses in large volumes to specific ports known for its use in mining such as port 3333 i.e. Stratum protocol. We can cross-check the IPs from the results against the provided lists using the following query.
This query can be as used for alerting to detect coin mining activity using all the aggregated logs. It searches for communication with known coin mining IP addresses, and sub-domains by matching them to lists (COIN_MINER_IPS, and COIN_MINER_DOMAIN). This list is prepared to reference from sigma rule and GitHub repos as reported by other security researchers. The query returns any matches found in the network logs, allowing you to detect any coin mining activity on your network.
We can see some hits against the known mining domains. However, IP addresses/sub-domains can be easily changed. Here we can analyze passive DNS data logs on our SIEM to identify new IP addresses associated with the actor. The COIN_MINER_DNS is the static list of top-level domains associated with common currency mining pools, prepared from this awesome sigma rule. We can utilize this rule to identify the client and DNS lookup results. It can give us the new IP addresses of miners.
Investigation of crypto-miner through DNS can be done by looking into DNS queries and responses from endpoints/hosts to our local DNS servers for suspicious activity. For example, if there are large numbers of requests for domains associated with cryptocurrency miners, or if the responses contain unusually long strings of data, this could indicate that coin mining is taking place. Additionally, if there are requests for domains associated with known malicious actors, such as command and control servers, this could indicate that coin mining is taking place as part of a larger malicious campaign.
The source address is the host/endpoint that is querying with the local DNS server, i.e. destination_address, to resolve the domain’s IP addresses, and the results can be seen in the answer. It can be seen that new IP addresses related to coin-miner are getting resolved for the same domain.
With this, there is a confirmation of mining activity in the network. However, due to strict adherence to the list, new IOCs can be observed from the further investigation processes. We must check for other systems that may have connected to this newly found IOC or have similar indicators of compromise at any point in time in the past. In this case, we can use Logpoint to correlate logs from different log sources i.e. from endpoints to the network. It is recommended to search for a time period longer than 30 days.
An example could be;
A newly found IP address is 197.56.78.87 and the domain ‘newly.founddomain’. To check its communication to other endpoints in the network we would query as follows:
For a more targeted coin miner detection in a host, we have already released a Linux-based detection.Threat hunting with Linux – Detecting a cryptomining attack
Considering the investigation a success, this information now can be used to block the IPs, isolate the hosts, and remove the mining process or files as necessary. The investigation and subsequent remediation can be tedious. However, Logpoint being an integrated SIEM+SOAR solution, streamlines and automates the incident response process triggering incident response on alerts, automating repetitive tasks, improving response speed and consistency, scalability, reducing human error, and providing reporting and auditing capabilities.
Endpoint detection and remediation with Logpoint AgentX
Logpoint agent AgentX works in conjunction with Logpoint SIEM+SOAR as a holistic security solution to detect, investigate and remediate security threats. The AgentX Collector enables you to collect endpoint event logs and flat files. It also provides a file integrity scanner and registry scanner to monitor and report the changes made in files, directories, or registries in endpoints.
Indifferent from the classic Logpoint agent which is more focused on collecting and forwarding log data to a central location, it focuses more on providing host-level security visibility, intrusion detection, and remediation. It has automated remediation capabilities such as blocking IP addresses on agents, isolating the host, terminating the malicious process, removing files, and so on. With AgentX, we can also integrate OSQuery for investigation and carry out a live query on the host enhancing incident response and forensic processes.
Logpoint AgentX is available now: For more information, you can contact your representative.
How AgentX helps to investigate and remediate crypto-miners?
When it comes to crypto-mining attacks, Logpoint has you covered. With AgentX, you can accelerate the TDIR process without adding complexity to the tech stack.
Investigation
With AgentX and OSQuery installed on the agents, we can get the live status of endpoint services and processes to identify malicious/suspicious activity. To ease the analyst burden, we also ship out-of-the-box AgentX OSQuery playbooks such as OSQuery Investigate Host, Investigate Process, Get running processes and applications, etc. which might be helpful in SOC processes such as investigation remediation.
Remediation
Based on the investigation result, the analyst can also use favorable playbooks to mitigate the threat. If the host was found to be in a highly critical state, an analyst can isolate that host by automatically or manually running the ‘AgentX-Isolate-Unisolate-Host’ playbook to further contain the damage and segregate it from Network.
The analyst can always block the malicious addresses (coin miner address) on the host by running the ‘AgentX-Block-IP’ playbook as well.
The IP address that was found to be associated with the crypto-mining pool is blocked in the host Win-Soar using the AgentX playbook.
Remediation and mitigation best practices
-
Identifying and isolating the source of the mining activity, for example, through the use of network monitoring tools.
-
Getting rid of the mining software and any associated malware.
-
Updating and patching any vulnerabilities that were used to install the mining software.
-
Thoroughly reviewing security protocols and making any necessary changes.
-
Using network segmentation to limit malware’s ability to spread.
-
Educating employees on the risks of cryptocurrency mining as well as how to spot and report suspicious activity.
-
Implementing endpoint security solutions such as AgentX to combat malware.
-
Reviewing and monitoring network activity for signs of mining activity regularly.
-
Enforcing strictly enforced access controls and monitoring critical resources.
-
Continuously monitor critical organizational assets with a combination of tools such as Sysmon and the Logpoint Converged SIEM platform.
Final thoughts
Crypto-miners have become a prevalent threat in the cybersecurity industry as they continue to evolve and become more sophisticated. The use of crypto-mining malware is increasing, and it can have a significant impact on an organization’s resources, resulting in financial losses.
For security analysts looking to protect their organization from the harm/loss caused by crypto miners, proactive detection and remediation are critical. Analysts can investigate crypto-mining activity and initiate appropriate responses using the Logpoint Converged SIEM platform, which combines SIEM, SOAR, UEBA, and BCS for SAP. Couple that with AgentX, our built-in endpoint response. With the resources provided in this report, now you can actively hunt crypto-miners and disrupt their chain of attack.
** We can help you! For assistance with the suggested playbooks – design, development, and implementation – contact Global services here.

Contact Logpoint
Contact us and learn why
industry-leading companies
choose Logpoint:












