SOAR & Automation: Workflows at machine speed
- Triage and investigate: With SOAR you can speed up alert triage processes to optimize your security team’s time and ensure that no threat goes unnoticed.
- Orchestrate and respond: Reduce cyber security risk with automated playbooks for rapid investigation, containment, and removal of threats.
- Expand your SOAR: Combine Automation with Case Management for scalable incident investigation and response or integrate with almost any log source.
Over 1,000 Organizations Across 70 Countries Use Logpoint SIEM










Automation Decreases the Time to Detect and Respond
Security teams become more efficient by using automated, structured workflows for day-to-day tasks. They free up time to focus on complex threats and investigations, and time is key to prevent damages.
By implementing automated playbooks, you reduce the incident response time and manual intervention over alerts.
Logpoint Automation aggregates security data from multiple sources, prioritizes and executes the response according to standard workflows, and automates the investigation, containment, and removal of threats.
DETECT, AUTOMATE, ORCHESTRATE
Enhance your security posture
Add orchestration and automation to Logpoint SIEM to improve overall efficiency and response times. With aggregated data from various security tools, the alerts will trigger playbooks.
The playbooks automatically execute the actions required to detect, investigate, and respond to the incidents. If your team needs flexibility, they can also decide to schedule playbooks or run them manually.
Logpoint Automation turns your security event management tool into a full SIEM solution with SOAR capabilities.

EFFORTLESSLY AUTOMATE INCIDENT RESPONSE
Create Custom Playbooks with Easy Drag and Drop
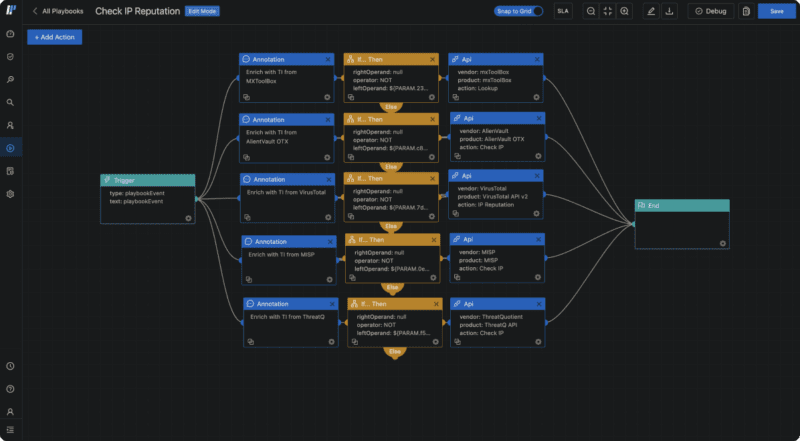
Logpoint Automation offers the capability to create your own custom playbooks with an intuitive drag and drop UI. With prebuilt code blocks organized by action types, you can easily assemble custom workflows.
Whether you want to expand the 80+ out-of-the-box playbooks or you prefer to create them from scratch, you always have documentation at your disposal.

We discovered this program a few years ago and found it to be the greatest alternative. It meets our organization’s cybersecurity requirements. One of the advantages of being a Logpoint member is that the customer receives SOAR, a tool that automates the routine tasks of a SOC analysis. SOC analysts no longer need to verify low-level alarms and cleaning records now that SOAR is available. Instead, the SOC analysis may apply critical thinking to tackle difficult issues while SOAR handles the simple ones.
Gartner Peer Insights Review

Built-in Playbooks
Get access to an extensive collection of out-of-box, playbooks to automate standardized detection, investigation and response processes, or adapt them.
Guided Decisions
Automation investigates alerts and recommends a response. Analysts simply execute the suggestion, making them more productive, even with limited resources.

Quicker Triage Process
Enrich alerts with contextual information and threat intelligence to check whether there is known data on visible indicators or tactics and technical procedures.
Reduce Investigation Effort Combining Automation with Case management
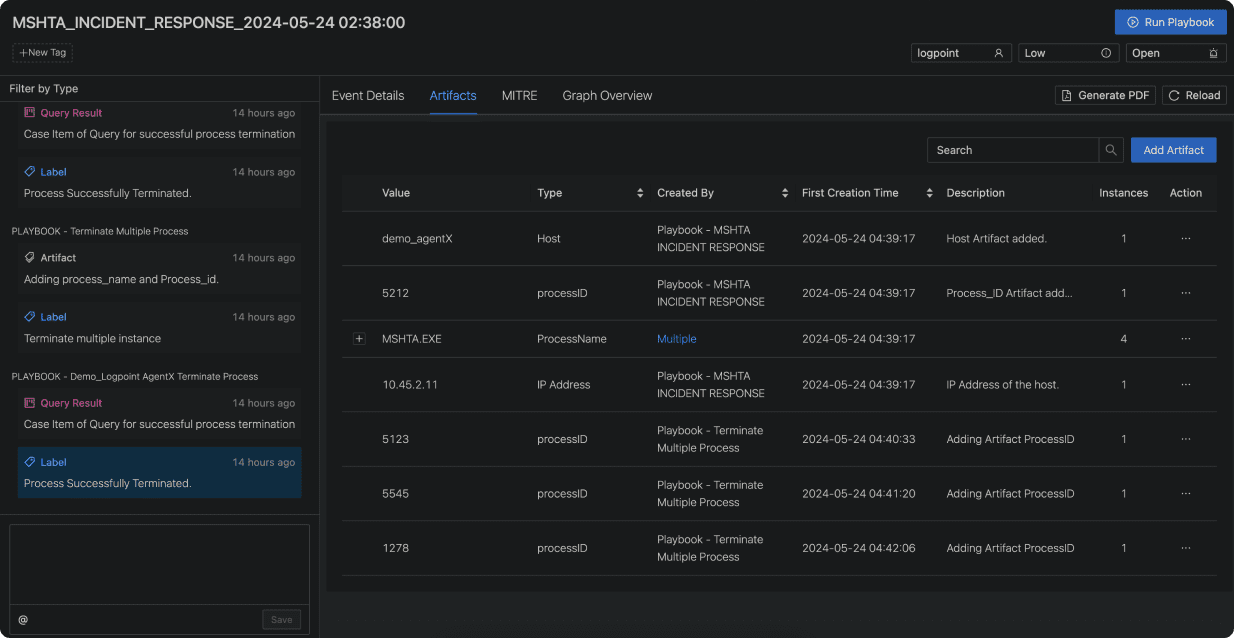
When you add Case Management to Automation, not only do you reduce the time to respond, but also you ensure a cohesive investigation process in collaborative investigations.
If a playbook is triggered, Logpoint will automatically create a case, which represents one or more incidents that make up a potential attack and enlists details about the threats. It also offers a timeline over the chain of events associated with the threat facilitating joint investigations.
Centralize, collect, distribute, and analyze investigation data in a coordinated manner.
Automate your tech stack, whatever it is
Logpoint parses and analyzes logs from over hundreds of integrations so you can automate actions for any tool in your tech stack. We continuously add more log sources based on customer needs — if you miss one, contact Logpoint Customer Support.
More than log sources
Process Commands, Enrichment Sources, UEBA, Authentication, Normalizers, Parsers… With an extensive collection of third-party security and integration packages you’ll boost your threat detection, investigation and response capabilities
Automate endpoint investigation and response
Connect endpoints with automated playbooks to respond with speed
Logpoint SIEM ingests logs and telemetry from endpoints and constantly runs CIS scans. If it detects a problem, it will gather additional insight into what is happening to the client and start the response using 20+ playbooks for endpoints.
Run actions on endpoints
Automatically react to a problem using the right playbook. Logpoint Automation will contact the endpoint agent to run actions on the endpoint, such as killing a process, gathering further intel, or isolating the host pending an investigation.
Watch how you can do it too
From SIEM to Cyber Defense
Looking to consolidate your tech stack? See how Logpoint SIEM fits with Automation, Case Management, and Behavior Analytics in one platform that combines data sets from multiple sources. Instead of using multiple standalone products, you can unify your security needs under one single source of truth.
- Full data integration for automated TDIR
- No integration or maintenance required
- Out-of-the-box compliance support
- Flexible deployment based on your needs
Do you want to get started with Logpoint Automation?
Book a personal demo and discover the benefits of adding Automation to Logpoint SIEM. Our Sales Engineers will work with you to find the best way to cover any specific use case you have.
