SIEM: High observability and analysis for any use cases
- Ingest and detect: With our SIEM you connect all data sources for more precise threat detection and meaningful investigations with contextual data.
- Store and report: Easily meet regulatory compliance criteria. Our SIEM comes with out-of-the-box reports and audit records of all changes in your system.

Over 1,000 Organizations Across 70 Countries Use Logpoint SIEM.

Centralize Data Monitoring for Heightened Visibility
Logpoint SIEM collects log and event data produced by any device, application or endpoint within your infrastructure.
By centralizing the data monitoring you improve your visibility into your network and IT infrastructure.
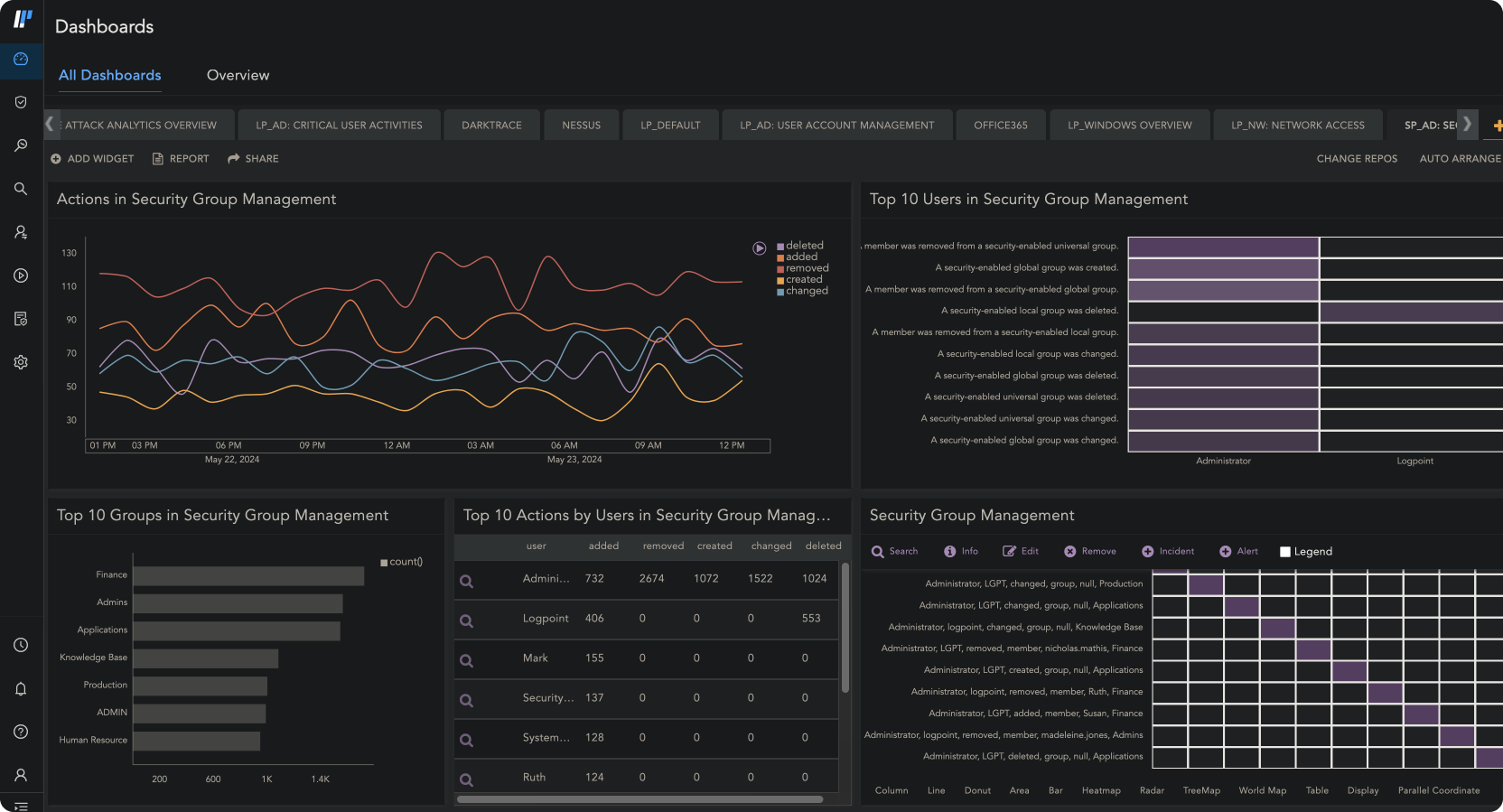
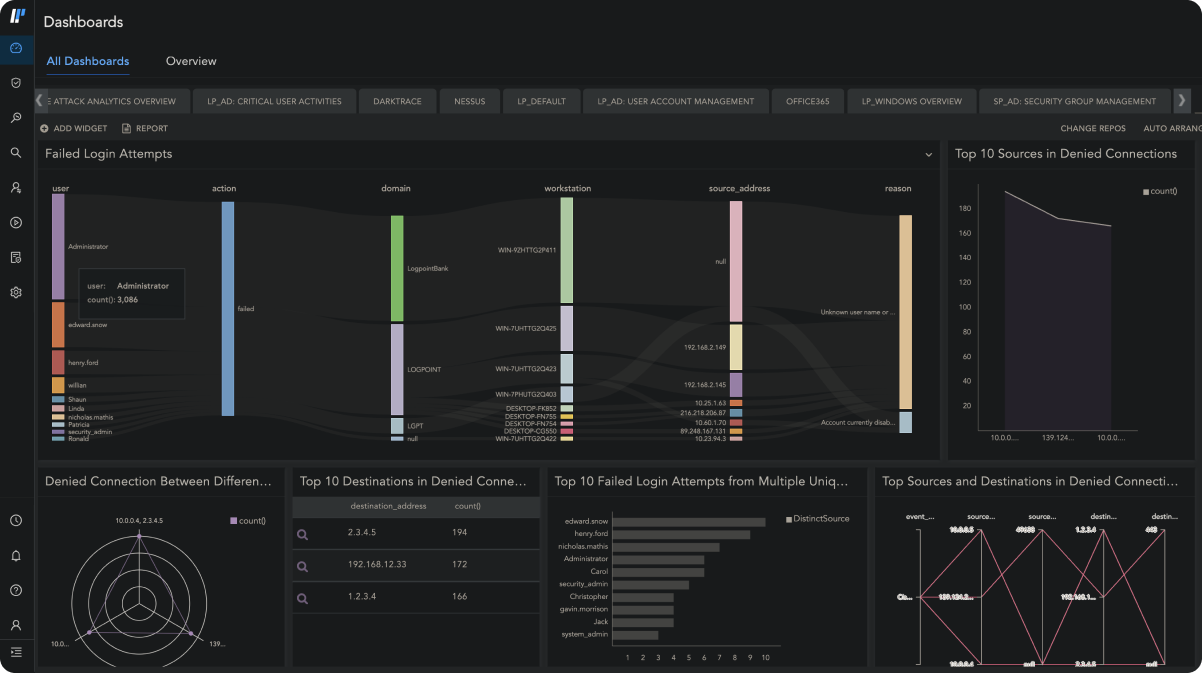
POWERFUL DATA ANALYSIS:
Improve Threat Detection and Investigation
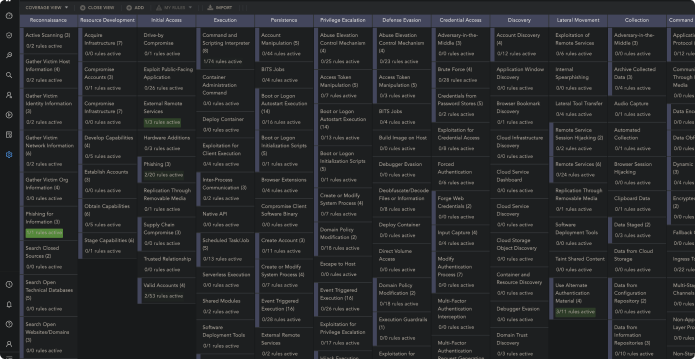
Logpoint SIEM tool translates complex log and event data into a single language and maps all alerts to MITRE ATT&CK for easier analysis of incidents and user activity.
With intuitive visualization of the data you get more context to quickly detect and investigate incidents.

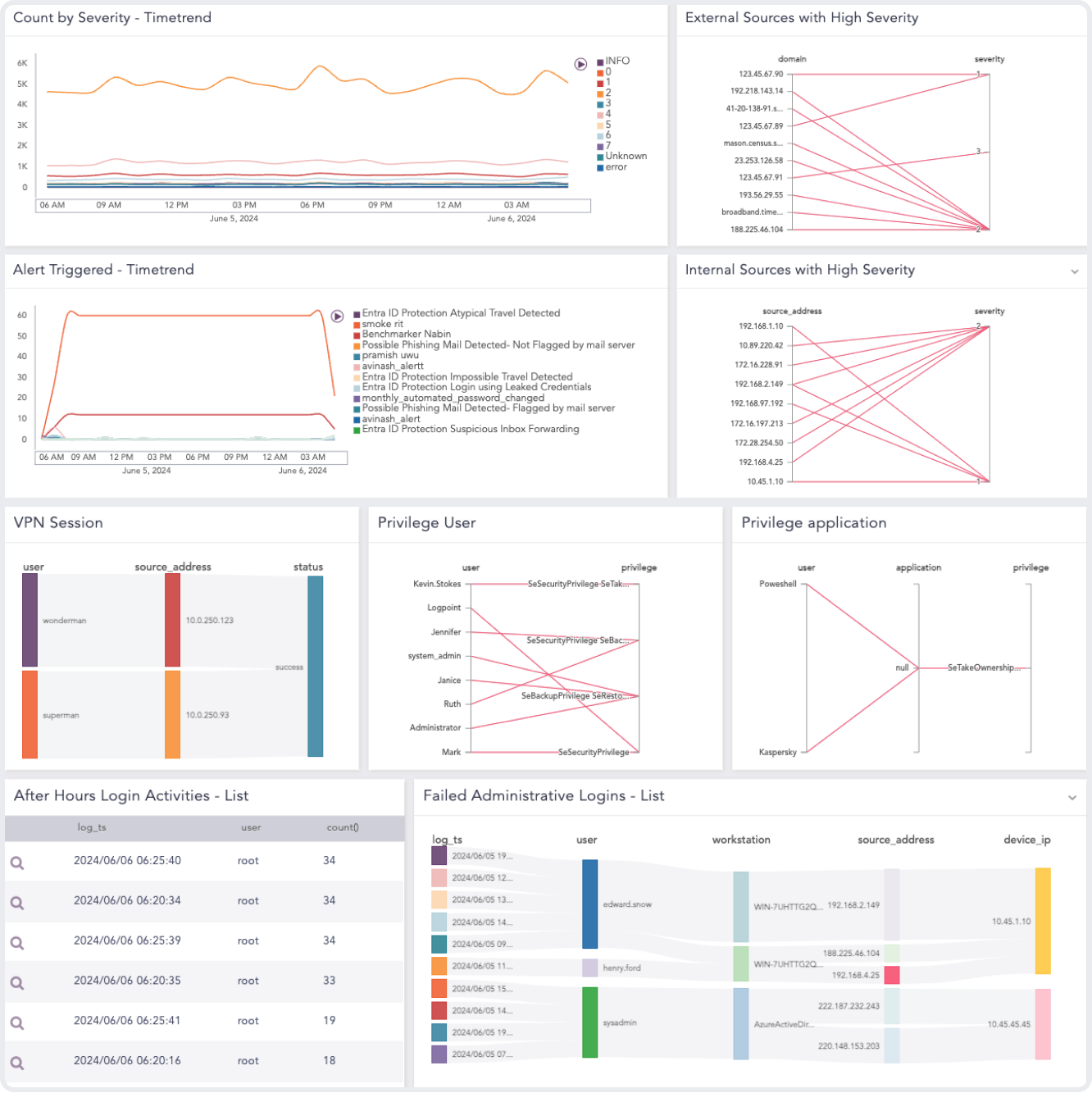

OUT-OF-THE-BOX COMPLIANCE SUPPORT
Meet Compliance Requirements with Ease
Logpoint SIEM ensures you adhere to major regulatory domains, such as GDPR, NIS2, and GPG13, and industry-based ones. It comes with pre-configured dashboards for access management, incident management and perimeter security monitoring.
With forensic analysis and investigation capabilities, you can effortlessly present evidence of compliance and determine the root cause of the breaches in the least amount of time.
INGEST, PARSE, STORE, AND SEARCH
Proper taxonomy to achieve any use cases
Logpoint SIEM collects all the relevant events and metrics from log sources, data sources, and endpoints through a wide range of built-in collectors and fetchers and a native endpoint agent.
It then normalizes them into Logpoint’s common taxonomy, so the analyst doesn’t have to know the exact format of logs for each device. After that, Logpoint enriches logs with contextual data, such as threat intelligence, geographical information, LDAP, and more.
With such level of granularity in its normalization and extensive enrichment, you can cover any use case you need. Whether you need to run in-depth investigations or get alerted for certain events related to compliance.
Using Logpoint fundamentally changes the way you work with log data in your infrastructure. With Logpoint log data becomes a useful tool. It allows us to take control and get a meaningful, constant output that enables us to spot potential problems and react promptly. Before things turn into a real threat
From SIEM to Cyber Defense
Looking to consolidate your tech stack? Witness how SIEM fits with Automation, Case management, and Behavior Analytics in one platform that combines data sets from multiple sources. Instead of using multiple standalone products, you can unify your security needs under one single source of truth.
- Full data integration for automated TDIR
- No integration or maintenance required
- Out-of-the-box compliance support
- Flexible deployment based on your needs
Precise detection of malware and incidents in endpoints with AgentX
Precise detection of malware and incidents in endpoints with AgentX
![]()
![]()
![]()
![]()
![]()
![]()
An increasing number of attacks are designed specifically to target endpoints and gain unauthorized network access. Against them, you have AgentX.
Logpoint’s native endpoint sensor is present in Logpoint SIEM to increase threat detection by providing additional insight to user actions and processes running on your endpoints.
Making sense of endpoint data is critical to maintain the business’ security. With built-in MITRE TTP enrichment, you can identify the tactic, technique, and procedure for the relevant signal, and put context into it.
Connect the dots between various signals to efficiently perform forensic investigations and threat hunting on endpoints.
AgentX built-in enrichment goes beyond security and also assists in identifying which events are key for compliance and corresponds to the control defined in compliance standards.
This enrichment of logs and telemetry supports GDPR, NIST 800-53, PCI-DSS, and many others, but you can define compliance rules to easily address what you want to focus on.
Get notified if there is any violation on the integrity of infrastructure and data. AgentX runs security configuration assessment, constantly scanning endpoints for policy and configuration violations based on CIS CSC v8. It also monitors changes in Windows Registry content, permissions, ownership, and attributes of files by any unknown events
Never miss when devices enter a non-compliant state and stay on top of your security.
High mean time to investigate and respond to threats causes ineffective security operations and leaves organizations vulnerable to threats. Add Automation to Logpoint SIEM to get out-of-the-box security content and investigation and response playbooks.
Combine SIEM with Automation to merge the precise and fast detection of AgentX with automated investigation and response capabilities.

