Business-Critical Security (BCS)
Secure your business-critical systems against irrevocable damage with a powerful and unified threat management solution.
Boost your cyber resilience and secure your important data from attacks with a unified security and observability solution that delivers real-time, holistic monitoring across your entire infrastructure. Effectively monitor, detect, and mitigate threats before they impact your revenue, disrupt your business operations, and damage your brand.

Over 1,000 Organizations Across 70 Countries Use Logpoint SIEM
Detect, Analyze, and Respond to
Threats – All-in-One Solution
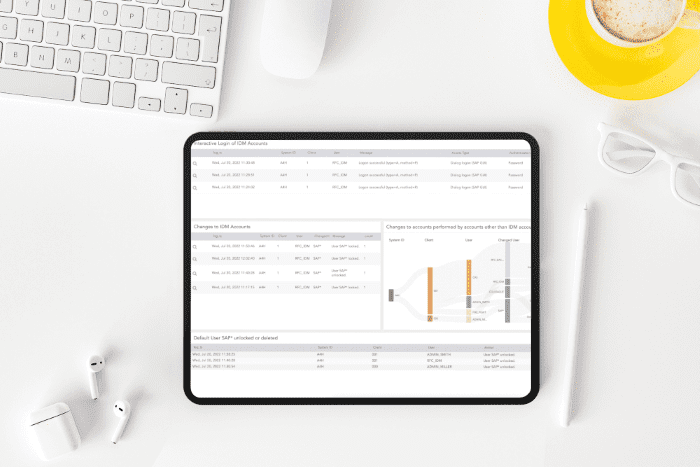
Security: End-to-end monitoring of your entire environment. Get the full context and transparency of events impacting your business-critical systems. Monitor, investigate, and analyze threats in real-time to effectively secure your critical infrastructure against breaches.
Advanced Analytics: Spot early signs of cyber breaches and defend against advanced threats with user and entity behavior analytics. Spot abnormal patterns and divert malicious activity early – before it impacts your business operations and revenue.
Response Orchestration: Automatically correlate business-critical data with security data to get contextual analysis of incidents. Understanding how incidents relate helps you orchestrate an improved response across technological and organizational silos enabling you to combat threats effectively.
Take a look at BCS in more detail below.
BCS – A Unified Solution
Secure your SAP systems and applications against cyber threats with a powerful and dedicated security management solution.
Effectively detect, manage, and respond to unauthorized access, violations, fraud attempts, IP theft, and operational degradations threatening the compliance, stability, and security of your SAP systems.
For more click here.
Embark on a new era of SAP BTP security where uncertainty is a thing of the past. Allow our powerful threat detection and monitoring solution to light the way, providing your teams with comprehensive threat visibility. This ensures they can respond to threats efficiently and take proactive measures to mitigate risks.
- Elevate the security of your SAP BTP – proactively
- Boost your security posture – effectively
For more click here.
Boost your SAP security & effectively respond to threats
Attacks on SAP systems are rising in frequency, sophistication, and severity. A successful breach can easily paralyze an entire organization, leak confidential information, undermine your brand authority, and lead to substantial financial losses.
For more click here.

SAP SuccessFactors is a depository for some of an organization’s most sensitive and regulated data. Safeguarding the confidentiality of employee information by ensuring that only authorized users can access and modify it is essential for avoiding fraud, breaches, costly compliance violations, and brand integrity infringements. Get more information below.
For more click here.

Identify advanced attacks early and efficiently defend against fraud
Reduce fraud-induced losses with improved detection of anomalies in business standards. Uncover potential fraud patterns, so you can take the necessary steps to mitigate the risks of fraud.
For me click here.

The IT-SI solution helps organizations identify an operations problem quickly – before it impacts their revenue, customers, or internal teams. With end-to-end visibility into the operational capabilities, we help you monitor and proactively safeguard the stability of your systems to ensure smooth operations, eliminate downtime, and avoid costly outages.
For more click here.

SAP stores a wealth of sensitive and Personally Identifiable Information (PII), dispersed throughout a multitude of different applications, integrations, and databases. Knowing where your sensitive data resides, who has access to it, and how to monitor it is almost an impossible task. With centralized monitoring, we provide you with holistic insight, so you can manage violations more effectively and you no longer operate in the dark to meet the compliance regulations.
For more click here.
React Faster with Actionable Data
Get the full overview of your security exposure with pre-built dashboards and customizable visualizations. Use multiple filtering options and search templates to navigate and act on your data easily.
Enhance Your Operational Efficiency
Remove data silos and operate from a single point-of-truth to mitigate risks effectively. Improve efficiency and workflows by managing detection, investigation, and response from one central security operations platform.

Get Control of Your Data Privacy
Locating your sensitive data is the first step in securing it against misuse. By monitoring access and subsequent stream of actions taken relating to your sensitive data, we help you secure your sensitive assets and successfully meet the compliance regulations.
Effortless Integration with Your SIEM
No need to waste efforts on additional coding to tailor integrations. BCS for SAP seamlessly integrates with any of the leading SIEM providers.