Supported log sources
Logpoint comes with hundreds of integrations to make your life easier. Our customers and partners get ready-to-use controls, dashboards, reports, and alerts out of the box. All our applications are designed to suit various infrastructures and are all possible to implement within minutes.
Logpoint integrates with any data source, and we currently connect to more than 400 log sources. You can find the full list of log sources on our doc portal. If you require a custom integration, we’ll create and deliver it to you within days as a part of your Logpoint subscription. Below you can see a few examples of how some of our integrations can benefit your organization.
Find the full list of log sources here:

Database

Endpoints

Applications
Network

SOAR

Cloud

Threat Intelligence

Firewalls
Use cases
The extensive catalog of integrations, both out-of-the-box, and custom, allows you to have a SIEM solution that matches your organization’s needs, reduces the impact of cyberthreats, and makes it easy for security analysts to detect potential issues and quickly put a stop to any cyberattack. Here are three examples of some of our most used integrations:
Accelerate detection and response
The Logpoint integration with Cortex XSOAR combines security monitoring and incident response to help security staff respond to and resolve incidents fast. Our combined solution automates actions and responses, handling incidents that don’t need the security team’s attention. Security teams get complete control over incidents and remediation, and they can further expedite processes with Cortex XSOAR’s customizable playbooks.
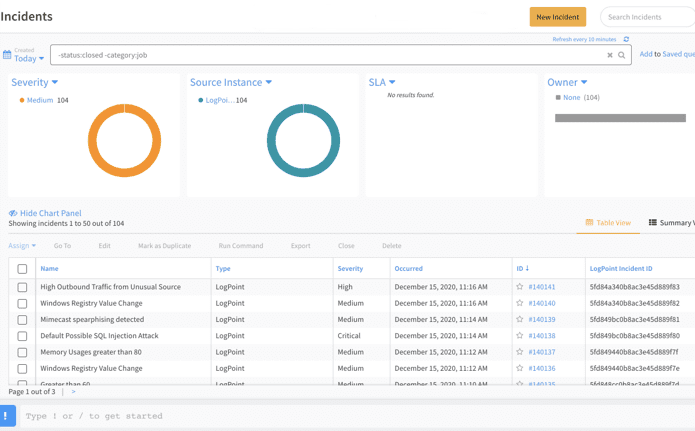
By using an out-of-the-box integration like XSOAR, you:
- Get real-time threat indications, which ensure that your SOC will find breaches before the 280-day average
- Will have a comprehensive understanding of the threat landscape with built-in incident prioritization.
- Reduce mean time to respond with incident mapping.
- Can easily create unique playbooks for specific needs based on a sample playbook.
Integrating with cloud-based platforms
Office 365 is one of the most widely used cloud-based platforms. By integrating Logpoint with Office 365, you get the instant benefit of a centralized log monitoring tool and correlation between other on-premise and cloud-based events for extensive cloud security and threat monitoring. It is possible to use this data for general and business analytics, along with security and compliance controls within your Office 365 environment.
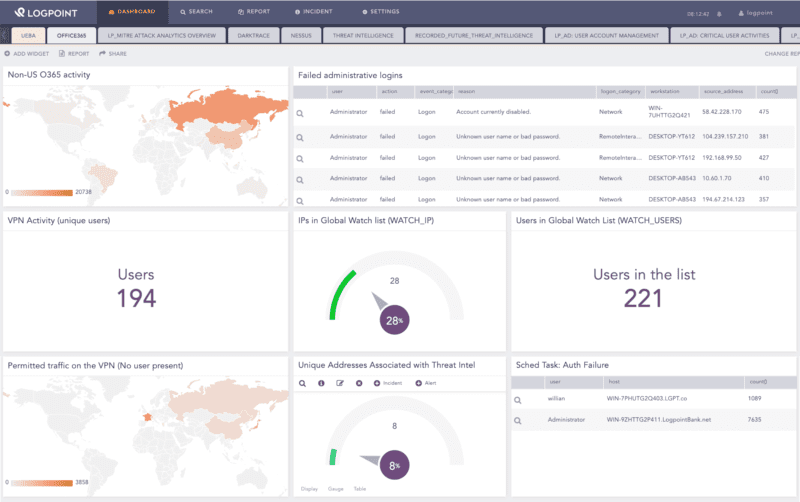
By using Logpoint’s out-of-the-box integration with Office 365, you can:
- Keep track of changes made within active directory, including your Azure/Office 365 environment.
- Control file changes, deletion, and access in SharePoint.
- Monitor OneDrive activities to establish controls within data exfiltration, unauthorized access, and sharing of files.
- Keep your confidential critical information safe by monitoring email activity for Exchange online, including attachments and other media within the emails.
Protect business-critical SAP systems from fraud and cyberattacks
SAP is possibly the most important application in an organization, but it is not usually part of the security monitoring solution. A modern SIEM monitors all IT infrastructure, and with Logpoint for SAP organizations can integrate SAP into SIEM, for full insight into their SAP system. Logpoint for SAP integrates SAP systems with SIEM for compliance and security monitoring of SAP systems.
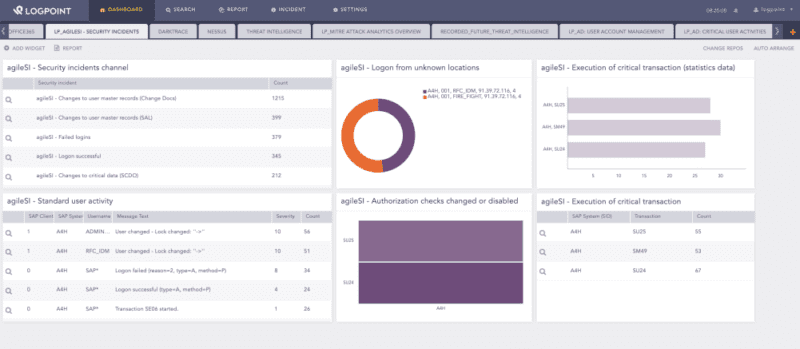
With Logpoint for SAP, you can:
- Get near real-time monitoring of SAP events and information, so you know what is happening with your SAP data at all times.
- Save time with ready-to-use controls, checks, dashboards, and reports to automate the monitoring of SAP system compliance or maintenance.
- Get alerts for any suspicious activity, making it easy for security analysts to detect potential issues and quickly stop any cyberattack.
- Analyze and monitor SAP information and events so you can continuously audit the system and automatically create reports. Automated auditing enables your organization to generate valuable reports on audit-required items.
- Monitor and track SAP events throughout the entire network and get complete control over the whole IT environment.
