- Home
- Solutions & Industries
- Critical infrastructure
Cybersecurity for Critical Infrastructure
Cyberattacks on critical infrastructure can have devasting effects and disrupt main functionalities of a modern society. To secure robustness, SCADA (Supervisory Control and Data Acquisition) – a control system architecture is designed to secure the infrastructure against being compromised. However, these networks are susceptible to disruption of services, redirection and manipulation of operational data.
Ensure NIS2 compliance with Logpoint
NIS2 Directive is stepping into force, striving to enhance protection of critical infrastructure in EU from cyberthreats. It introduces stricter security demands, reporting obligations and enforcement requirements for a broader scope of sectors. Inability to comply can impose fines up to 2%* of the worldwide turnover.
WHY LOGPOINT:
Holistic Security of Your Critical Infrastructure
Highly targeted attacks in complex SCADA networks require advanced event monitoring from both the SCADA system and general IT infrastructure. This includes ERP systems, such as SAP, which are often in place in critical infrastructure environments.
With a unified security and observability solution, Logpoint delivers real-time, holistic monitoring across your entire infrastructure. Get alerted when a suspicious pattern arises and keep track of all incidents in one view with intuitive dashboards. Logpoint is ideal for investigating threats, enabling proactive cybersecurity response, and providing a platform for ensuring compliance with industry standards.
WHY LOGPOINT:
Identify and Respond to Incidents Faster
Dynamic lists collect and store event-specific values and allow for dynamic updates. By enabling analysts to define dynamic lists and tables, organizations can reduce the time to detect and respond to incidents faster. By combining dynamic lists with static enrichment, we empower our customers to build self-configuring analytics to automatically react to new observations accelerating response and MTTR.
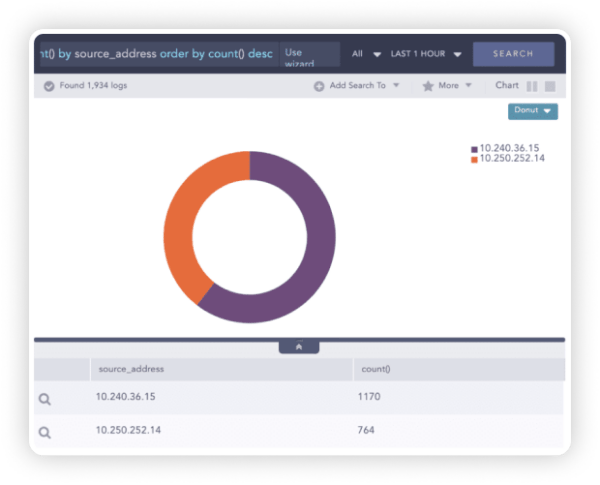
WHY LOGPOINT:
Authentication and Transmission Control
To make audits of transmission controls easier, Logpoint can detect activities such as email, https, and VPN communications. Authentication and transmission control for data security is enforced to ensure a proper authentication mechanism for user identity. Similarly, for transmission controls, Logpoint utilizes secure communication channels for interaction between an external object and a Logpoint instance or between multiple Logpoint instances.
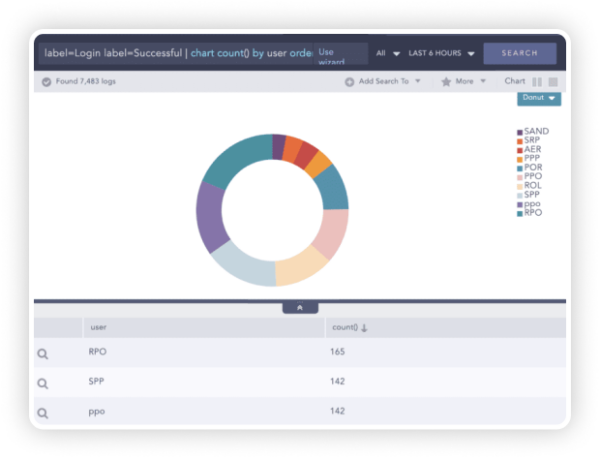
WHY LOGPOINT:
Uncovering IoCs
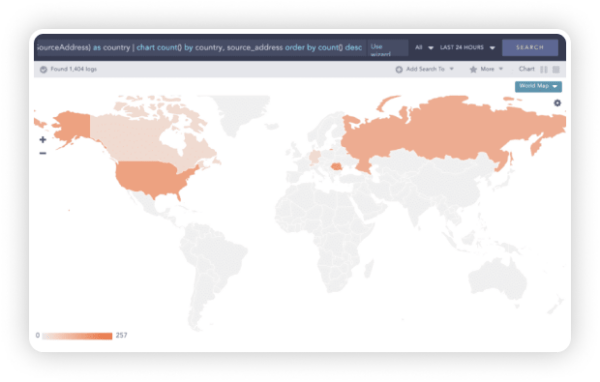
Systems involved in any abnormal behavior can easily be enriched with Threat Intelligence Feeds to check for the associated indicators of a compromise. Furthermore, Logpoint provides you with the exact geographical location of the source of the attack.
Use Case:
Logpoint for Computerome
Computerome is one of Scandinavia’s largest High-Performance Computing (HPC) clusters dedicated to life science research. Keeping a tight check on big data and meticulously documenting how users access information is a regulatory requirement. To ensure the highest security level and compliance, Computernome has chosen Logpoint’s SIEM solution.

Logpoint allows Computerome administrators to quickly detect unusual behavior in the system and to prevent misuse and data breaches. It provides that extra layer of security on top of the established security controls, which is required when handling vast amounts of data. It also allows us to provide our users with full insight and transparency.

Peter Løngreen,
National Life Science Supercomputing CenterGet up to date with the Logpoint blog!
From N-Days to Multiple Arch: Inside RondoDox’s Delivery Pipeline
The RondoDox Shift RondoDox is a Linux botnet family first identified by FortiGuard Labs in…
Breaking the Kill Bit: Active Exploitation of CVE-2026-21509 in Microsoft Office
Overview Microsoft disclosed CVE-2026-21509 in early January 2026 as part of an out-of-band…
An open letter on security, sovereignty, and the right to choose
This is why Logpoint was built differently. We believe security platforms should give customers…
