Akira in the Network: From SonicWall Access to Ransomware Deployment
SonicWall confirms active exploitation of an as-yet-unnamed 0-day on their Gen 7 firewalls’ SSL VPN, enabling attackers to bypass MFA, steal credentials, and deploy Akira ransomware within hours. Telemetry from Huntress shows dozens of intrusions against fully patched TZ and NSa-series appliances running firmware ≤ 7.2.0-7015. Organisations should disable SSL VPN or restrict it to trusted IPs, gather enhanced logs, and apply the detections below until patched firmware is released. Given the speed at which attackers escalate privileges and move laterally after initial access, detecting post-exploitation activity is critical for early containment and response—rather than relying solely on identifying the SonicWall exploitation itself.

Background
Arctic Wolf has observed malicious VPN login attempts since at least October 2024. On July 15, 2025, the company detected a significant spike in suspicious SSL VPN logins targeting Gen 7 SonicWall appliances. Up to July 25, Huntress confirmed approximately twenty incidents where attackers leveraged that access to reach domain controllers within hours. By August 1, Arctic Wolf published an advisory highlighting successful MFA bypasses. On August 4, SonicWall issued an emergency notice urging customers to disable SSL VPN, while The Register reported the same day that a likely zero-day vulnerability was driving the intrusions.
| Date | Key development |
|---|---|
| Early Jul 2025 | Surge of anomalous SSL VPN log-ins and repeated failures observed directly in SonicWall security logs across multiple organisations. |
| 15 Jul 2025 | Arctic Wolf reports the first confirmed spike in successful malicious VPN sessions against Gen 7 appliances. |
| 25 Jul 2025 | Huntress validates ~20 intrusions and notes rapid pivot from the firewall to domain controllers. |
| 01 Aug 2025 | Arctic Wolf issues a public advisory confirming MFA bypass in the attacks. |
| 04 Aug 2025 | SonicWall publishes an emergency notice urging customers to disable SSL VPN until patched. |
Suspected vulnerability – No CVE assigned (as of 6 Aug 2025). Behaviour indicates an authentication-bypass or session-fixation flaw that affects Gen 7 firmware ≤ 7.2.0-7015. Exploits succeed despite TOTP MFA and recent credential rotation.
Affected products
| Product family | Firmware builds confirmed vulnerable |
|---|---|
| TZ-series Gen 7 | up to 7.2.0-7015 |
| NSa-series Gen 7 | up to 7.2.0-7015 |
Detections
At Logpoint, we have closely tracked Akira ransomware since its initial emergence, publishing detailed analyses outlining its common tactics, techniques, and procedures (TTPs). While the initial access vector frequently changes—as demonstrated by the current SonicWall zero-day exploitation—subsequent attack phases, including persistence, defense impairment, lateral movement, and impact, often remain consistent. Customers already using Logpoint SIEM have detection coverage and detailed insights into Akira’s typical behaviours, enabling faster identification and response to ongoing threats.
Log Sources Needed
-
Windows
-
Process creation with command-line auditing should be enabled.
-
Registry Auditing
-
-
Windows Sysmon
-
To get started, you can use our sysmon baseline configuration.
-
In this section, we focus primarily on detecting the post-exploitation tactics, techniques, and procedures (TTPs) associated with Akira ransomware as documented by Huntress. We've also highlighted existing Logpoint alerts capable of identifying these behaviours, along with additional hunting queries designed to proactively detect related malicious activity.
Reconaissance
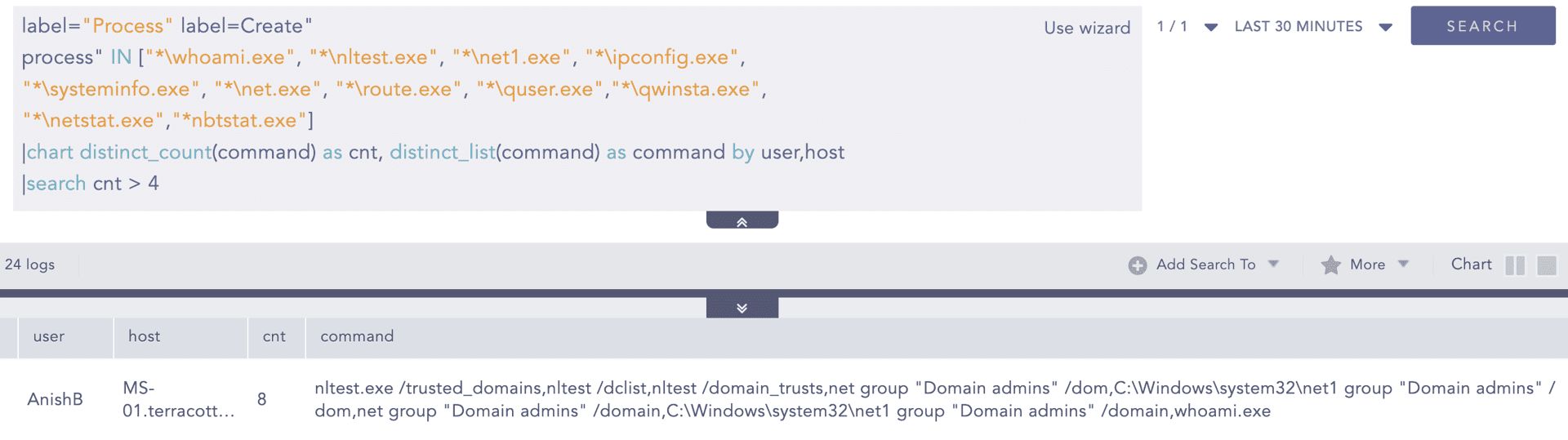
After gaining an initial foothold, adversaries performed user and network reconnaissance through various methods. They leveraged built-in Windows binaries such as nltest.exe, ping.exe,quser.exe and net.exe as well as external scanning tools, including NetScan and Advanced IP Scanner, as demonstrated below.
Reconnaissance using Windows Binaries Detected
Adversaries commonly utilize various built-in Windows binaries in close succession for reconnaissance activities. These behaviors can be effectively identified using the Reconnaissance Using Windows Binaries alert.
Additionally, Logpoint provides a dedicated alert, Suspicious Usage of Advanced IP Scanner, specifically designed to detect usage of Advanced IP Scanner, a frequent tool of choice among adversaries for performing network discovery.
Data Staging and Exfiltration
A commonly observed method for data exfiltration is compressing sensitive files into archives before transferring them out of the environment. According to TTPs documented by Huntress, adversaries in this campaign staged data by executing WinRAR commands on multiple compromised hosts, compressing files using nearly identical command-line syntax. The only variation among these commands was the specific source or target drives involved. This technique enables adversaries to efficiently aggregate and prepare data for subsequent exfiltration.
To detect data staging attempts like these, Logpoint has you covered with Suspicious Compression Tool Parameters alert. The alert identifies suspicious usage of common data archiving tools such as 7z.exe, winrar.exe, and rar.exe, allowing you to quickly spot adversaries prepping data for exfiltration.
Persistence
As one of the most commonly abused LOLBins, msiexec.exe is often used by adversaries for both initial access and persistence, particularly to install tools like RMM software. Huntress observed Akira deploying tools such as AnyDesk, ScreenConnect, and OpenSSH via .msi installers dropped in C:\ProgramData.
To detect such abuse, Logpoint has you covered with the Suspicious Msiexec Usage Detected alert. Whether msiexec is used to install persistence tools or as part of lateral movement, this alert is designed to catch the most common and known misuse cases of this binary.
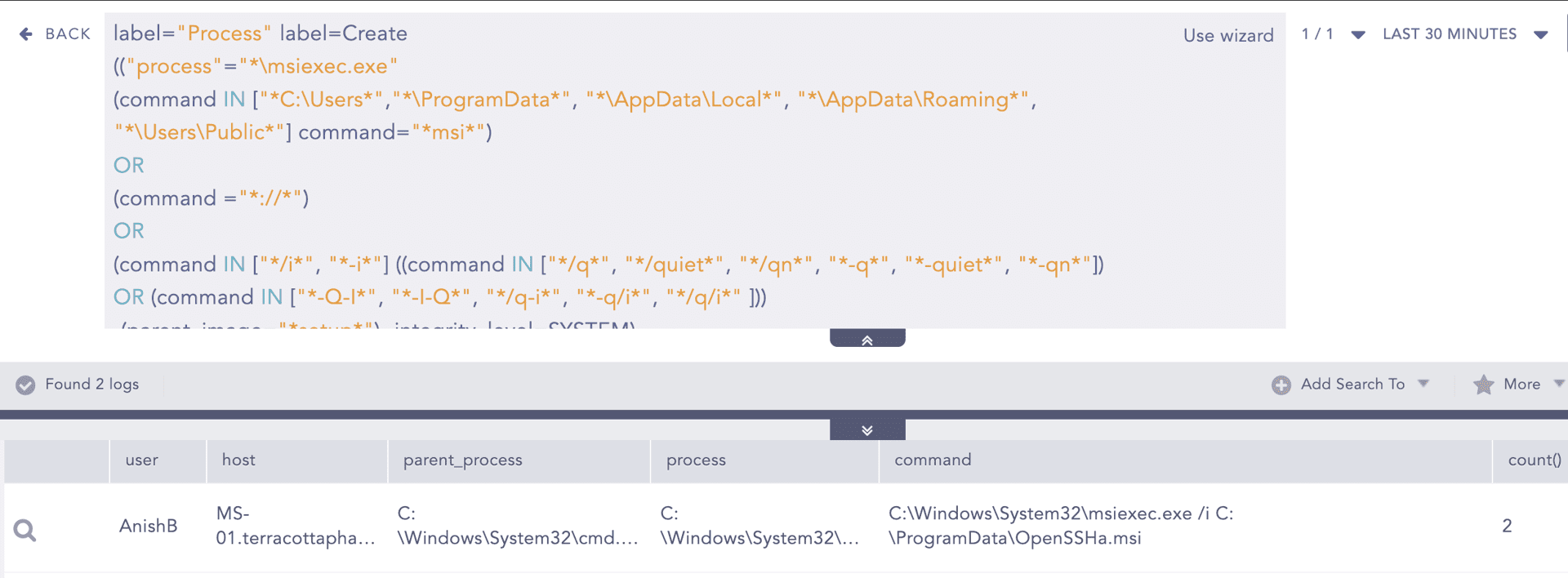
You can also leverage File Dropped in Suspicious Location alert to detect .msi files being dropped into suspicious directories such as C:\ProgramData.
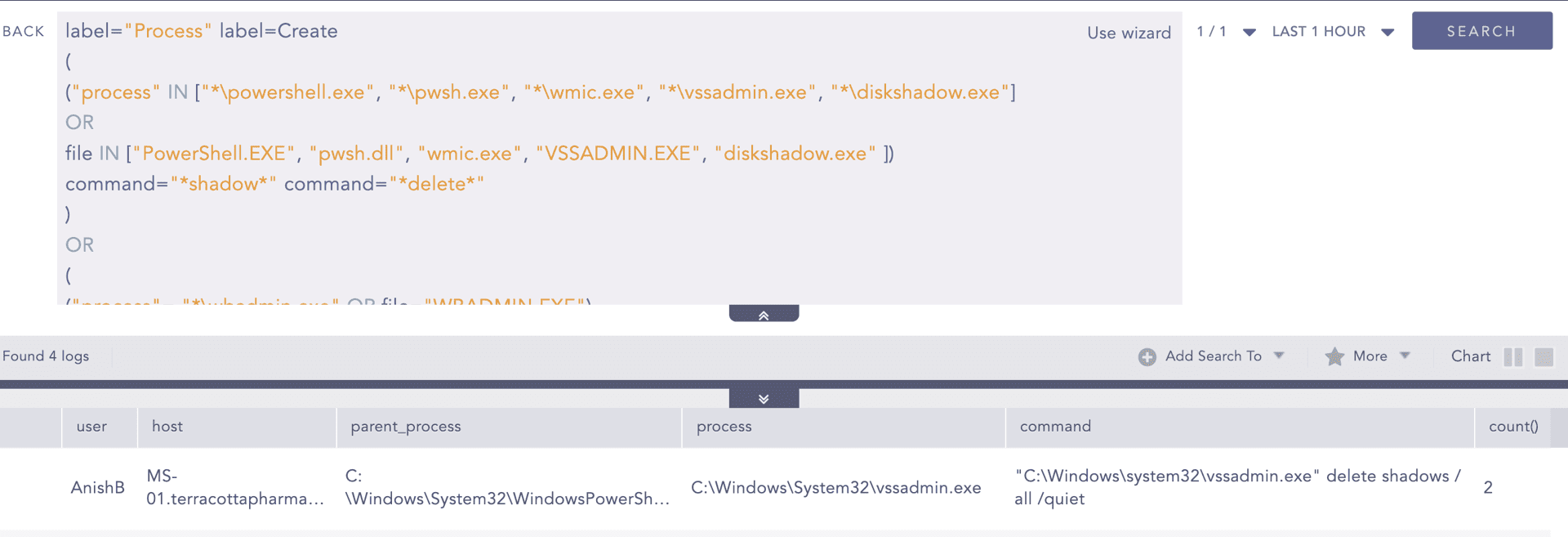
Shadow Copy Deletion Using OS Utilities Detected:
In order to prevent recovery, Akira have used vssadmin.exe to delete the volume backups, so we can use this alert to detect such events,
Alerts for Post-Exploitation Detection
In addition to the adversary behaviors discussed above, the following Logpoint alerts are highly recommended for detecting a wide range of post-exploitation techniques observed during Akira ransomware intrusions. These alerts are not limited to Akira alone—they are designed to identify common behaviors exhibited by multiple ransomware groups. Enabling these alerts will significantly strengthen your visibility and response capability during similar attacks.
Customers are advised to use the latest alert rules application.
-
Firewall Disabled via Netsh Detected
Detects attempts to disable or modify the Windows Firewall using netsh.exe. -
Microsoft Defender Disabling Attempt via PowerShell
Flags suspicious PowerShell script blocks attempting to disable Microsoft Defender. -
Suspicious Windows Defender Registry Keys Modification
Monitors sensitive registry changes that could weaken or disable Defender protections. -
Process Execution from Suspicious Location
Detects when executables are run from commonly abused locations like C:\ProgramData. -
Windows User Account Created or Removed
Detects creation or deletion of local or domain user accounts (Event ID 4720). -
Windows User Added or Removed from Group
Identifies when users are added to or removed from privileged groups (Event ID 4728). -
Browser Credential Files Accessed
Flags access to browser credential stores, such as Chrome or Edge login data files. -
File Dropped in Suspicious Location
Detects when files are created in directories frequently abused by attackers, including C:\ProgramData. -
Suspicious Eventlog Clear or Configuration Using Wevtutil Detected
Detects when event logs are cleared via wevtutil.exe -
Possible Modification of Boot Configuration
Detects when boot configurations are modified to prevent recovery and safe mode boot. -
High Number of Process Terminations
Detects when a high number of processes are terminated—commonly observed as a preparatory step before ransomware deployment to reduce errors and interference. -
Suspicious Scheduled Task Creation
Detects the creation of suspicious scheduled tasks commonly used by adversaries to maintain persistence or trigger payload execution. -
Autorun Keys Modification Detected
Detects modifications to registry keys responsible for launching applications during system startup—often leveraged for persistence.
Hunting post-exploitation
Credential Access
Adversaries targeted Windows Active Directory credentials by attempting to extract the NTDS.dit database. To do this, they used legitimate Windows backup utilities like wbadmin.exe to create volume backups, a known tactic for obtaining copies of sensitive files from shadow copies. While Akira was observed using wbadmin specifically, attackers often leverage similar tools such as vssadmin to achieve the same goal.
Hunting Query:
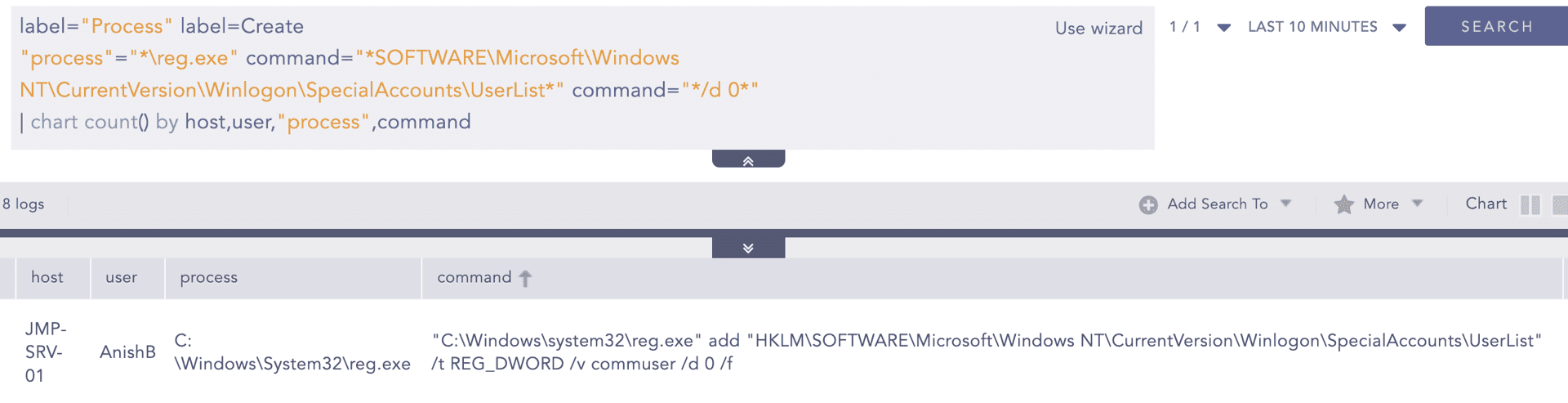
Hidden Users
To remain undetected, the Akira gang modified registry values to hide user accounts from the standard login screen. This is done by adding the account under the SpecialAccounts\UserList registry key and setting its value to 0.
To detect such activity, you can use the following hunting queries:
Process-based Detection:
Registry-based Detection (if Registry Auditing is enabled):
After detecting such behavior, you can visualize the attack chain using Logpoint’s Process Tree feature.
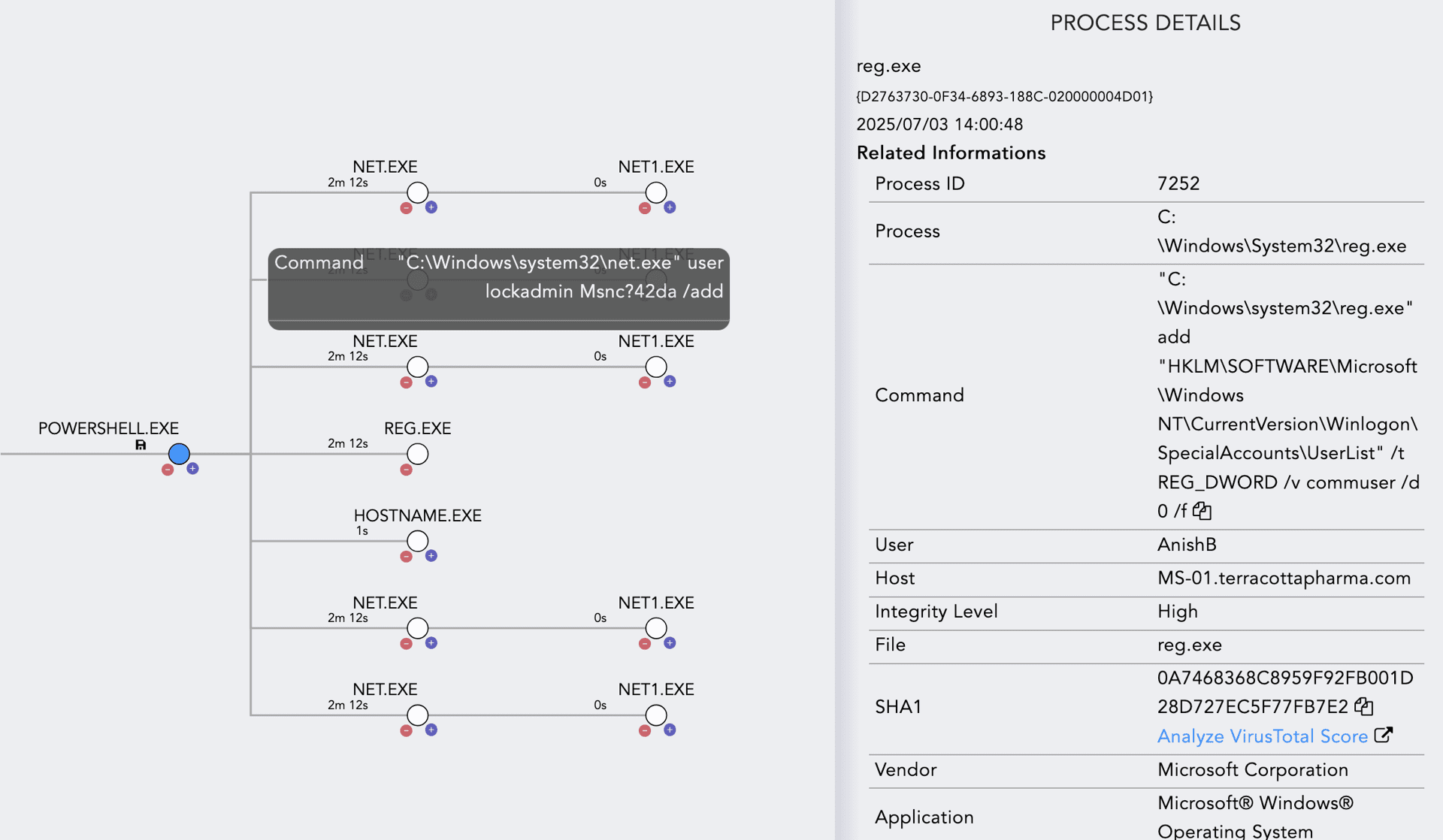
Recommendations and Guidance
To protect your organization from exploitation of the SonicWall SSL VPN vulnerability and Akira ransomware, Logpoint recommends the following tailored security measures:
1. Immediate VPN Risk Mitigation
Organizations should immediately disable SSL VPN services on Gen 7 SonicWall appliances if possible. If VPN access must remain enabled, strictly limit it to essential users and trusted IP addresses only.
2. Credential Management and MFA
Immediately rotate credentials for all accounts used in SSL VPN. Disable or remove any unused local SonicWall user accounts, especially those previously provisioned with VPN access.
Enforce Multi-Factor Authentication (MFA) rigorously on all remote access points, prioritizing phishing-resistant MFA methods such as hardware tokens.
3. Network Blocking of Suspicious VPN Authentication Traffic
Review VPN authentication logs and proactively block authentication attempts originating from known hosting-related Autonomous System Numbers (ASNs) as shared in Arctic Wolf blog, which threat actors have repeatedly utilized in recent attacks. Consider restricting VPN authentication from the following ASNs:
| AS Number | Organization Name |
|---|---|
| AS23470 | ReliableSite.Net LLC |
| AS215540 | Global Connectivity Solutions LLP |
| AS64236 | UnReal Servers, LLC |
| AS14315 | 1GSERVERS, LLC |
| AS62240 | Clouvider Limited |
Note: These ASN networks are not inherently malicious, but authentication attempts from these networks may indicate suspicious or unauthorized activity. Blocking should be restricted strictly to VPN authentication traffic to minimize operational disruption.
4. Enhanced Logging and Monitoring
Ensure detailed logging is enabled specifically for SonicWall SSL VPN authentication attempts, admin activities, and connections. Continuously monitor these logs through SIEM (such as Logpoint) to detect anomalies or indicators of compromise promptly.
5. Implement and Enforce Security Best Practices
In line with SonicWall’s published guidance, enhance your firewall security posture by:
-
Activating Essential Security Services: Ensure features such as Botnet Protection are enabled to detect known malicious hosts targeting SSL VPN endpoints.
-
Practicing Robust Password Hygiene: Enforce strong, complex passwords and encourage periodic updates across all firewall and user accounts.
Note: These measures are best practices recommended broadly and do not guarantee complete mitigation of the zero-day risk described in this alert.
6. Proactive Threat Hunting for Akira TTPs
Regularly hunt for documented Akira ransomware behaviors (credential dumping, deployment of tunneling tools such as cloudflared, disabling of security services, and clearing of logs) using available Logpoint queries. Prioritize response to any detections that align with known Akira indicators or behaviors.
7. Strengthen Incident Response Capabilities
Regularly update and rehearse your Incident Response Plan through practical exercises, focusing explicitly on ransomware scenarios involving compromised VPN access. Clear escalation paths and documented response protocols help ensure rapid containment.
Final Words
Apply firmware patches promptly once available. Swift patching significantly reduces the attack surface and is a critical component of your overall defensive strategy.




