Citrix Vulnerabilities Rising – When Gateways Give Way
Citrix has issued an urgent warning about multiple vulnerabilities in NetScaler ADC and NetScaler Gateway appliances. Among them, CVE-2025-7775 (CVSS 9.2) has already been weaponized by attackers and so has made it’s entry to the CISA’s Exploited Vulnerabilities (KEV) catalog. More than 28,000 exposed Citrix instances remain vulnerable, leaving organizations open to remote code execution, denial of service, and unauthorized access. Since exploitation is already confirmed, postponing updates is not an option. Organizations that fail to patch risk a full network compromise, data theft, or becoming an entry point for ransomware operators.

Overview
On August 26, 2025, Citrix published Security Bulletin CTX694938, addressing three newly discovered vulnerabilities in NetScaler ADC and NetScaler Gateway. These flaws carry two high and one critical severity ratings and affect multiple supported versions, including 13.1, 14.1, 13.1-FIPS, and NDcPP:
-
CVE-2025-7775 – Critical memory overflow that can lead to remote code execution or denial of service (CVSS 9.2).
-
CVE-2025-7776 – Memory overflow vulnerability causing system instability and denial of service (CVSS 8.8).
-
CVE-2025-8424 – Improper access control on the management interface that could allow unauthorized access (CVSS 8.7).
With CVE-2025-7775 already under active attack and all three vulnerabilities now in CISA’s KEV catalog, organizations should assume exploitation is underway across exposed systems.
CVE Details
| CVE ID | Description | Pre-conditions / Affected Configurations | CWE | CVSS v4.0 |
|---|---|---|---|---|
| CVE-2025-7775 | Memory overflow leading to Remote Code Execution (RCE) or Denial of Service | NetScaler configured as Gateway (VPN, ICA Proxy, CVPN, RDP Proxy) or AAA vserver; LB vservers (HTTP/SSL/QUIC) bound to IPv6 or DBS IPv6 services; CR vserver type HDX | CWE-119 – Improper Restriction of Operations within Memory Buffer | 9.2 (Critical) |
| CVE-2025-7776 | Memory overflow vulnerability causing erroneous behavior / DoS | NetScaler Gateway configured with PCoIP profile | CWE-119 – Memory Buffer Restriction Failure | 8.8 (High) |
| CVE-2025-8424 | Improper Access Control allowing access via NSIP, Cluster IP, GSLB Site IP, or SNIP with management access | Management interfaces exposed | CWE-284 – Improper Access Control | 8.7 (High) |
Who’s at Risk?
Organizations operating Citrix NetScaler ADC/Gateway appliances are at high risk if:
-
Devices are exposed to the internet and configured as Gateways (VPN, ICA Proxy, RDP Proxy).
-
Load Balancer vservers use IPv6 configurations.
-
Management interfaces (NSIP, SNIP, Cluster IP, GSLB Site IP) are directly accessible.
| Product Name | Affected Version |
|---|---|
| NetScaler ADC and NetScaler Gateway |
|
| NetScaler ADC 13.1-FIPS and NDcPP |
|
On August 28, using data from The Shadowserver Foundation’s internet scanning platform, we observed more than 28,000 Citrix NetScaler instances exposed online and vulnerable to CVE-2025-7775.
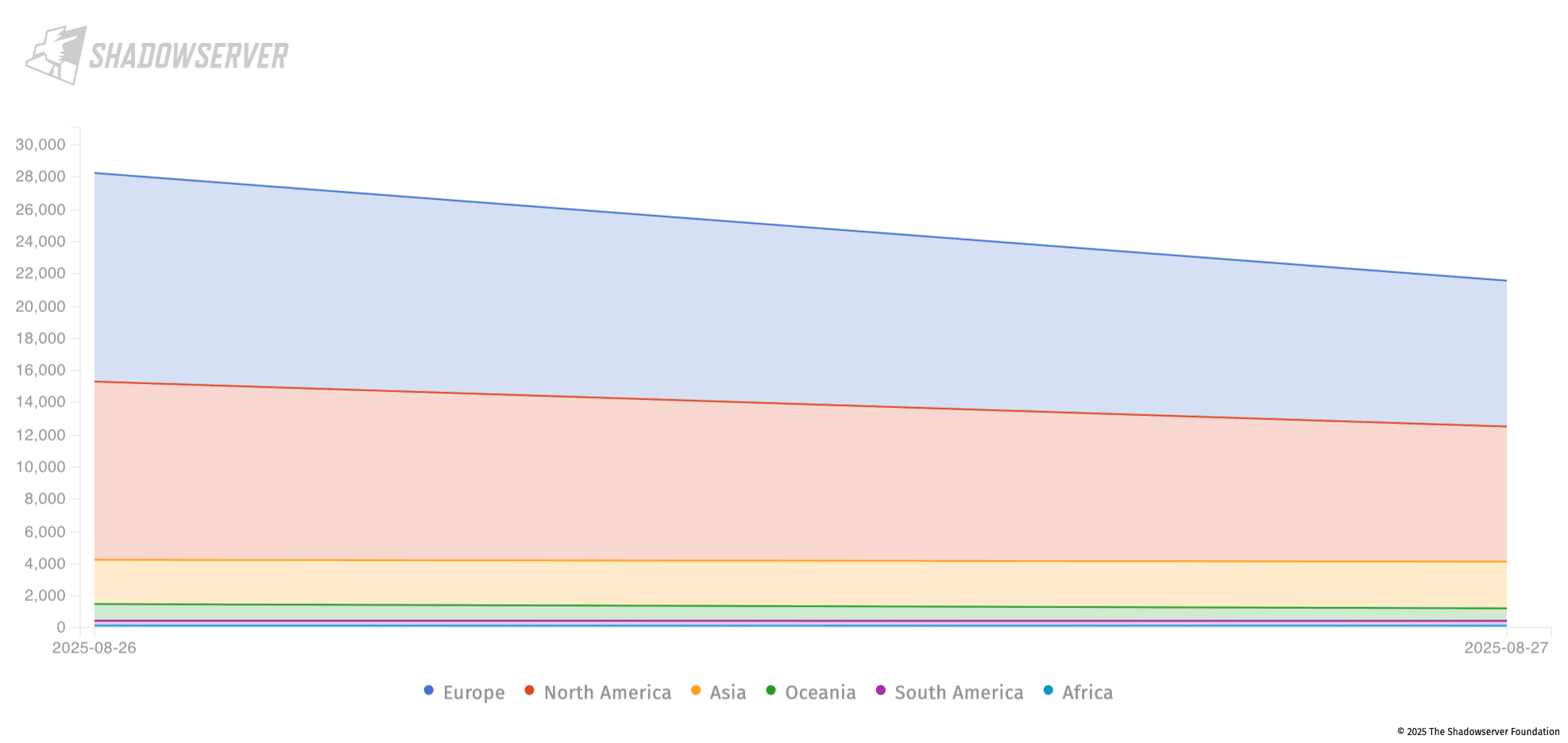
Count of Vulnerable Systems by Regions.
Why This Matters
NetScaler appliances are not ordinary infrastructure devices — they sit at the frontline of enterprise networks and are often the first target for attackers. Their role in secure access makes them especially dangerous if compromised.
They are high-value targets because they:
-
Sit at the network edge – acting as the gateway for VPN and remote access.
-
Handle sensitive authentication traffic – making them prime for credential theft.
-
Provide a direct path inside corporate networks – once breached, attackers can pivot quickly.
-
Enable high-impact attacks – compromise can lead to data theft, lateral movement, or ransomware deployment.
-
Widely exposed to the internet – thousands of organizations rely on them, expanding the global attack surface.
Thousands of Citrix appliances remain exposed to the internet, and exploitation attempts are rapidly increasing. As illustrated in the Censys scan results below, a significant number of vulnerable instances are still publicly accessible.
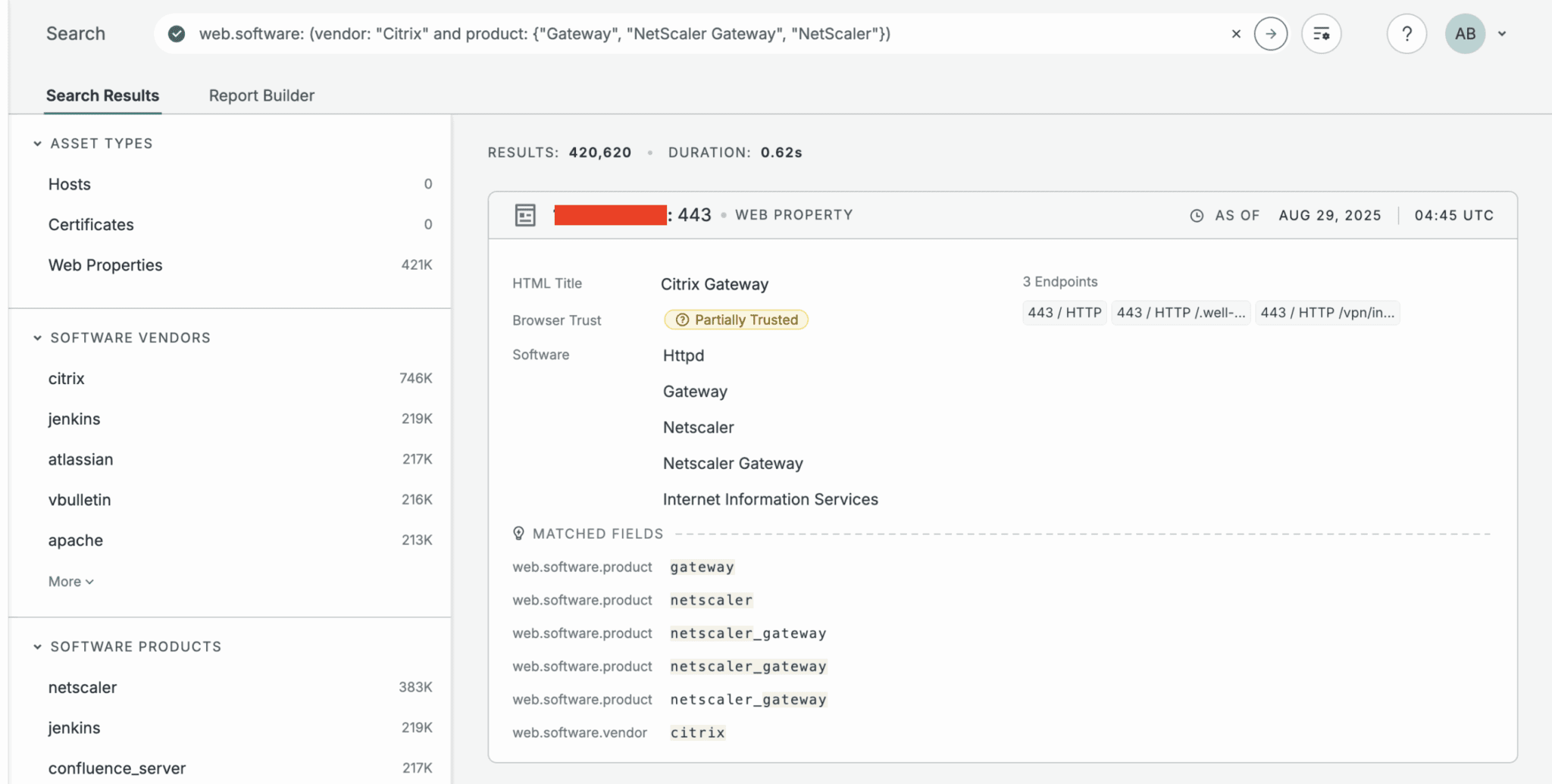
In the past, similar Citrix flaws were exploited by LockBit affiliates to gain access, and deploy ransomware. Even patching after exploitation may not remove an attacker’s foothold, highlighting the importance of thorough post-incident checks.
Recent Citrix Exploitation Trends
Citrix vulnerabilities have repeatedly been high-value targets for attackers. Earlier in 2025, a critical flaw known as CVE-2025-5777 a.k.a CitrixBleed 2 was disclosed, affecting NetScaler ADC and Gateway devices. Much like the original CitrixBleed, this bug allowed attackers to read sensitive memory and hijack sessions, with proof-of-concept code quickly weaponized after disclosure. Exploitation was observed in the wild even before patches were broadly applied, with security vendors and CISA rushing to add it to their KEV catalogs.
In addition, NCSC Nederland has confirmed exploitation of CVE-2025-5349, CVE-2025-5777, and CVE-2025-6543, stressing that adversaries are not only quick to weaponize Citrix flaws but also persistent in targeting them across different versions and deployments. These incidents underline a clear pattern: when Citrix vulnerabilities are published, active attacks follow rapidly.
Threat Hunting with Logpoint
Since there are currently limited public PoCs, datasets, or accessible exploited environments, we do not have a vulnerable Citrix setup to test against directly. Instead, this section draws on indicators and observations shared by researchers, vendors, and the wider security community. The goal is to provide guidance on detecting traces of enumeration, exploitation attempts, and post-exploitation activity within your environment.
Required Log Sources:
-
IDS/IPS
-
Firewall
-
Web Access Log
Hunting for CVE-2025-7775 IOCs and IOAs
As highlighted by researcher Simo, adversaries have begun scanning and fingerprinting vulnerable Citrix instances by sending GET requests to the URI /vpn/js/rdx/core/lang/rdx_en.json.gz in order to enumerate the version. Such activity can be detected using the following hunting query:
After the initial version scanning, additional IOCs related to exploitation have been observed. Specifically, attackers attempt to upload payloads via the /api/v1/configuration/ path. The following query can be used to detect such network or web request events:
Following the payload upload stage, adversaries access /var/tmp/poc_test.txt to verify that the file was successfully created and the vulnerability exploited. The query below can help identify such requests in network or web logs:
Hunting Indicator of Attacks (IOA)
Defused observe, 116[.]203[.]235[.]29 performing network scans to exploit older memory corruption vulnerability CVE-2025-5777, a.k.a CitrixBleed 2, so we can look for such attempts using the following query:
As new IOCs or technical details emerge, this blog will be updated with follow-up posts that provide refreshed detection logic and deeper insights.
Mitigation & Recommendations
Patch & Verify
-
Apply updates without delay — Citrix has released fixed builds in CTX69493. No vendor workarounds exist.
-
Identify vulnerable appliances quickly — use the NetScaler console’s Security Advisory → CVE Detection to locate affected instances and trigger upgrade jobs.
-
End all active sessions after patching (VPN, ICA, AAA, PCoIP) to flush hijacked tokens and stale authentication.
-
Prioritize exposed systems — Shadowserver reported 28,000+ NetScaler devices vulnerable to CVE-2025-7775 on the internet. If your device is public-facing, patch immediately.
Reduce Attack Surface
-
Restrict management access: ensure NSIP, SNIP with management enabled, Cluster IP, and GSLB Site IP are never exposed to the internet. Place them behind ACLs or VPN jump hosts.
-
CVE-2025-7775 is exploitable on LB vservers bound to IPv6. Disable IPv6 where unnecessary.
-
CVE-2025-7776 is triggered in Gateways using a PCoIP profile. Remove it if not required.
-
Harden Gateway access: enforce MFA, reduce exposure with IP allowlists or reverse proxies, and keep Gateway/AAA roles off the open internet where possible.
Post-exploitation artifacts
-
Monitor for unauthorized files under /var/netscaler/ and /var/vpn — look for unexpected PHP/XHTML uploads that may function as webshells.
-
Hunt for modified configs such as /flash/nsconfig/rc.netscaler or /etc/httpd.conf.
-
Watch for unusual SUID files (e.g., /var/tmp/sh) that attackers may plant to gain root privileges, and check for NetScaler Packet Processing Engine (NSPPE) core dumps in /var/core/, which can signal exploitation attempts or crashes triggered by attackers.
-
Monitor for malicious crontab entries or other persistence artifacts left behind by attackers.
If any of these indicators are present, treat the device as potentially compromised: isolate, collect forensics, rebuild from a clean image, and rotate credentials.
Incident Response Hardening
-
Rotate credentials and tokens — including LDAP, AAA, local admin, and API secrets.
-
Reissue TLS certificates used on the appliance and revoke any exposed keys.
-
Force reauthentication for all remote users.
-
Check for persistence (webshells, modified configs, cron jobs) before returning the device to production.
Governance & Monitoring
-
Follow NCSC-NL’s GitHub detection scripts to supplement IOC checks and confirm potential compromise for CVE-2025-6543.
-
Subscribe to CISA KEV and vendor advisories. Treat KEV-listed Citrix flaws as the highest priority patch items.
-
Baseline appliance behavior (management logins, session counts, AAA activity) and alert on anomalies.
-
Regularly scan your exposure with tools like Censys/Shodan to ensure no unintended public-facing services exist.