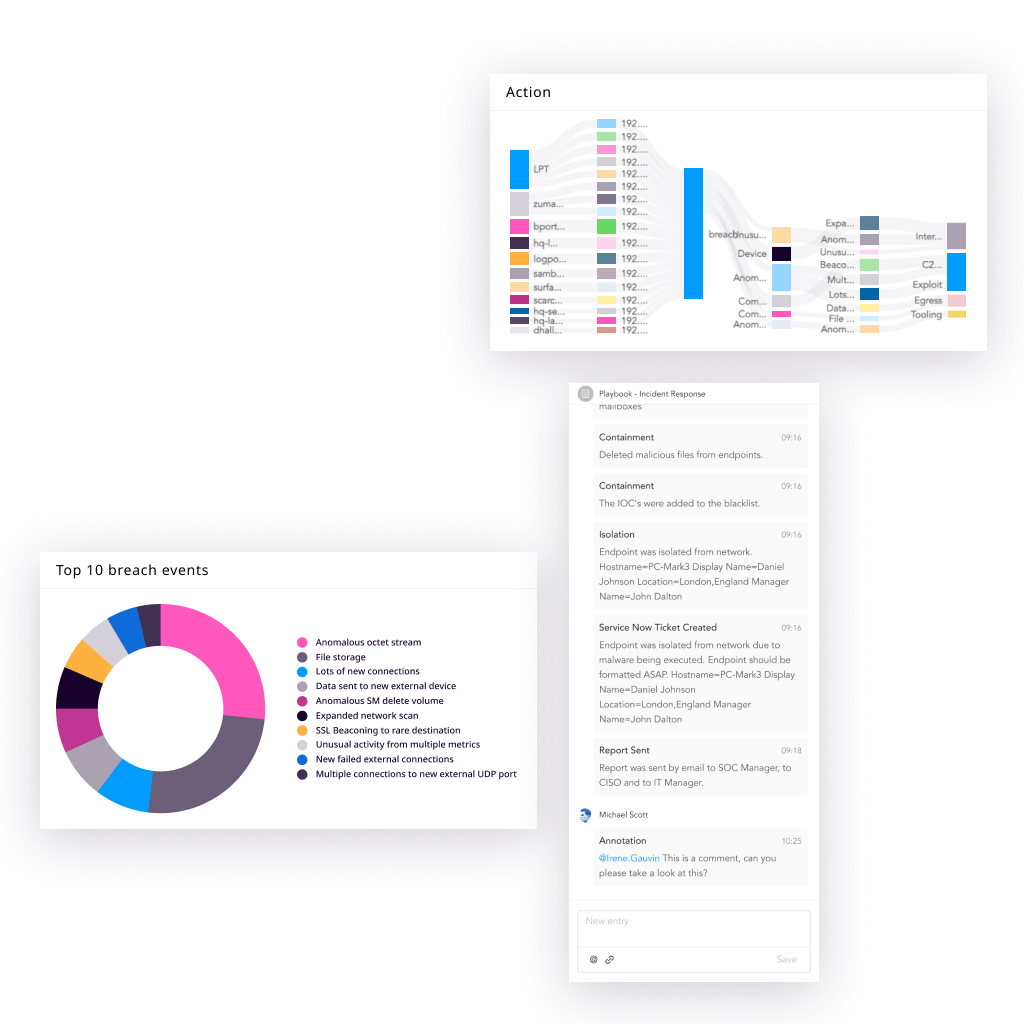
Logpoint SecOps Platform
Expand SOC capacity with zero overhead
Give your analysts the speed, coverage, and automation to punch above their weight and focus on what matters most, without adding complexity or cost.

Manage fleets without friction
Reduce complexity instead of just shifting it with flexible fleet control across every deployment.
Get sovereign-ready security
Cloud. Hybrid. On-prem. Meet data residency requirements without compromising control or capability.
Connect the full SecOps stack
With 100+ integrations and zero heavy lifting, your team can focus on outcomes, not plumbing.
Get instant visibility across environments
Reduce analyst workload with 1,000+ built-in, high-fidelity detections. No manual rule-writing needed.
Act with confidence, not assumptions
With network and log data, together at last, your team can see what’s happening, where it’s happening, and why.
Predict your costs instantly
Say goodbye to cost spikes with flat, predictable pricing. Ingest and operate with full confidence in your budget.

“The efficient management of customers’ SIEMs, the continuous development in close coordination with us as MSSPs, and the flexibility in architecture and data handling make the collaboration with Logpoint especially attractive for us.”
Tobias Rühle
Head of Security
A partnership beyond technology

Logpoint Collaborate for MSSPs
Deliver better services across customers
Accelerate growth with a partner who helps you win and retain customers. Logpoint Collaborate helps MSSPs go to market faster, deliver measurable value, and build long-term customer relationships.

Logpoint Academy
Get more from Logpoint. Fast!
Whether you’re onboarding or levelling up, Logpoint Academy gives your team on-demand and instructor-led training to operate faster, sharpen skills, and make impact from day one.

Support
Get help whenever you need it
You’re never on your own with Logpoint. Our experts are on call 24/7 to get you back on track, fast, calm, and always in your corner.
93% of MSSPs in Europe think it’s important to store a security solution within EU jurisdiction
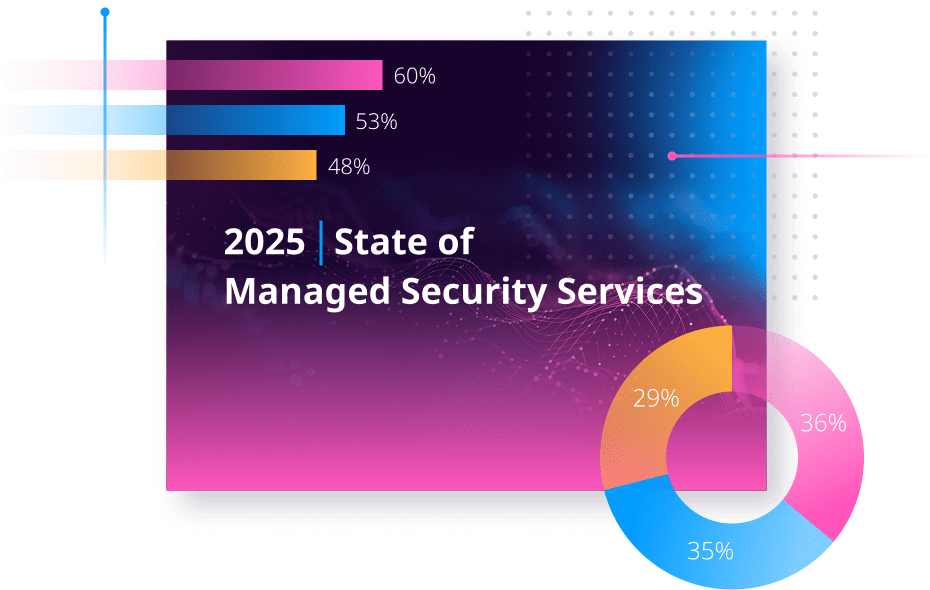
How mature is your cybersecurity posture?
Leader in IDC Marketscape on Worldwide SIEM for SMB 2024
We safeguard society in a digital world
See how our customers drive impact
Security teams trust Logpoint to deliver the clarity they need to detect threats, act fast and meet compliance demands. Read their stories.

CUSTOMER CASE
A node-based model made all the difference
Making the cost of the SIEM solution 100% predictable, eliminating budget concerns and, most importantly, eliminating the need to make decisions about leaving out log sources that may compromise security.

CUSTOMER CASE
One SIEM solution for everything
By integrating SAP with enterprise security tools, Başkentgaz improves threat detection, ensures long-term log retention, and streamlines incident response.

Manage fleets without friction
Reduce complexity instead of just shifting it with flexible fleet control across every deployment.

Get sovereign-ready security
Cloud. Hybrid. On-prem. Meet data residency requirements without compromising control or capability.

Get instant visibility across environments
Reduce analyst workload with 1,000+ built-in, high-fidelity detections. No manual rule-writing needed.

Connect the full SecOps stack
With 100+ integrations and zero heavy lifting, your team can focus on outcomes, not plumbing.
Predict your costs instantly
Say goodbye to cost spikes with flat, predictable pricing. Ingest and operate with full confidence in your budget.
Act with confidence, not assumptions
With network and log data, together at last, your team can see what’s happening, where it’s happening, and why.
BLOG
Stay sharp with the latest
research and insights
Keep up with new threats, trending topics, and expert perspectives from across the cybersecurity world.
From N-Days to Multiple Arch: Inside RondoDox’s Delivery Pipeline
The RondoDox Shift RondoDox is a Linux botnet family first identified by FortiGuard Labs in…
Breaking the Kill Bit: Active Exploitation of CVE-2026-21509 in Microsoft Office
Overview Microsoft disclosed CVE-2026-21509 in early January 2026 as part of an out-of-band…
An open letter on security, sovereignty, and the right to choose
This is why Logpoint was built differently. We believe security platforms should give customers…