Inside DarkGate: Exploring the infection chain and capabilities
As the threat landscape continually evolves, some positive developments, such as authorities tracking down Maldevs, threat actors, and forum managers, and seizing control of command-and-control servers while disrupting malware distribution networks, have become more frequent. In this dynamic environment, the emergence of new players and the adaptation of existing ones have become commonplace.
DarkGate overview
The continually evolving environment often leads to the rebranding of threat actors and the modification of malware families, as seen recently with the rise of DarkGate. Its proliferation has surged following the takedown of the Qbot infrastructure, exemplifying the ever-shifting nature of cyber threats. According to Cofense, similarities were identified between DarkGate and PikaBot phishing campaigns, reminiscent of Qakbot techniques. This suggests potential unknown connections or adaptations of existing techniques, underscoring the complexity of modern cyber threats.
DarkGate serves dual purposes as both a loader malware and a RAT, enabling it to execute various malicious actions such as stealing sensitive data from victims and deploying cryptocurrency miners. It is known to be created and maintained by a user who goes by the alias RastaFarEye on multiple forums. Undergoing development since 2017, DarkGate has evolved through various iterations while operating under a Malware-as-a-Service model. DarkGate is primarily distributed through phishing, often using Browser Update Themes. It is also spread via Malvertising and SEO Poisoning, varying according to the threat actor's preferred method of malware delivery.
One of the unique traits of DarkGate is that it uses Autolt, which is a scripting language designed for automating the Windows GUI and general scripting tasks. It allows users to create scripts that automate tasks such as keystrokes, mouse movements, and window commands. It is particularly useful for tasks like software installation, system administration, and automation.
Delivery methods
Let's delve into some of the DarkGate’s most common delivery techniques to shed light on the prevalent methods they use for malware distribution.
Phishing
DarkGate aka MehCrypter is primarily distributed through phishing, employing specific themes tailored for such deceptive practices. Threat actors strategically use phishing URLs, redirecting users to a Traffic Distribution System (TDS) to download the malicious payload. In October 2023, Proofpoint observed a phishing scheme where threat actors directed users to the Ketaro TDS. Victims were then presented with an internet shortcut (.URL) file through this process, and upon clicking, a zipped VBS script was downloaded.
An alternative tactic involves the exploitation of a fake browser update theme. If an end user interacts with the counterfeit browser update button, a similar process ensues, leveraging a TDS for the distribution of the malicious payload.
Again in October 2023, PaloAltoNetworks uncovered the distribution of DarkGate malware through Microsoft Teams. In this scenario, adversaries masqueraded as the CEO of the targeted organization, sending victims a Teams invitation as part of their deceptive tactics. The trend for using Microsoft Teams for phishing lures has still been seen recently in January 2024 by AT&T.
Malvertising
Malvertising, short for malicious advertising, is a technique used by adversaries to distribute malware via online advertisements. These deceptive ads, appearing on legitimate websites, exploit browser vulnerabilities, leading users to malicious sites or initiating malware downloads upon interaction.
Threat actors have employed themes related to remote administration tools, specifically leveraging the guise of Advanced IP Scanner, a widely used tool among IT administrators. When victims interact with the malicious ad, they are directed to a decoy site as part of the deceptive tactics employed by the attackers.
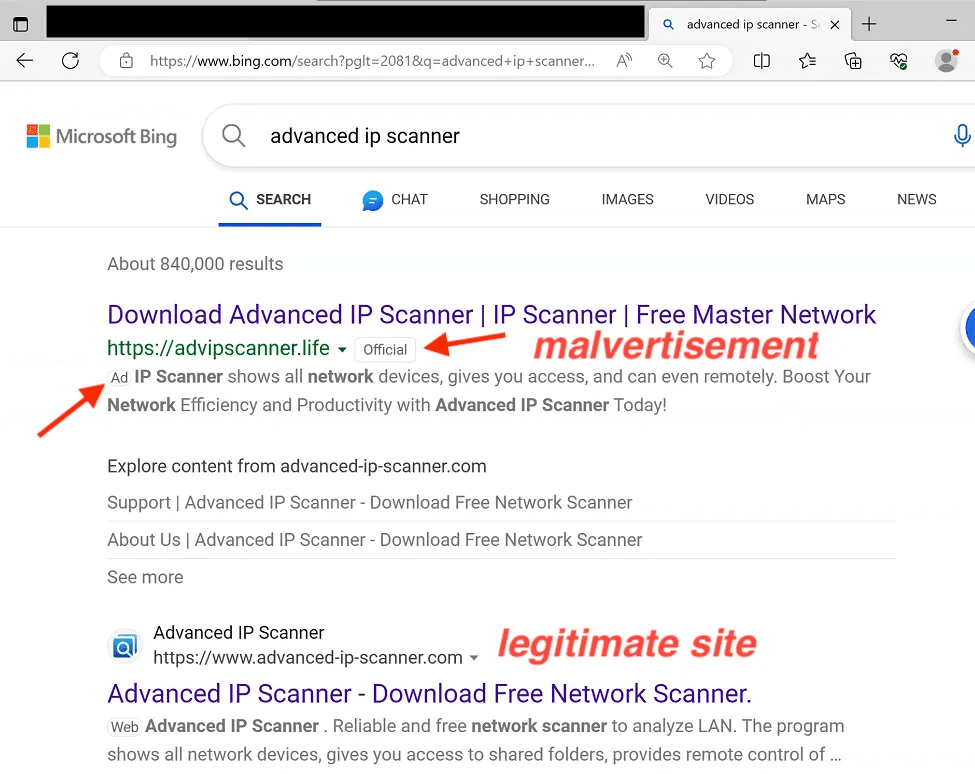
Source - Thrunter.medium.com
SEO poisoning
SEO poisoning, a technique manipulating search results to promote malicious content, aims to boost rankings of websites posing as legitimate ones. In contrast, malvertising spreads malware through infected online ads, tricking users into infecting their devices.
According to Malwarebytes, threat actors used the Advanced IP Scanner theme for SEO poisoning to distribute DarkGate malware. The tactic mirrored the malvertising campaign, focusing on Advanced IP Scanner. Through SEO poisoning, attackers aim to manipulate search results, redirecting users to malicious sites linked to DarkGate malware distribution.
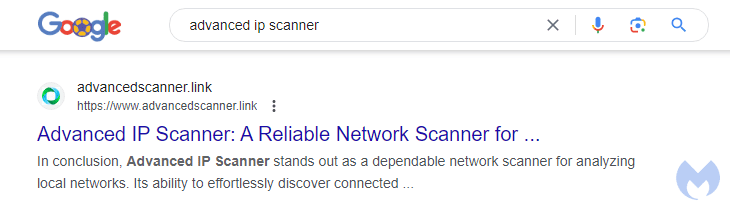
Source - MalwareBytes
To summarize the payload delivery mechanism, any threat actor or hacktivist can acquire DarkGate malware and employ diverse techniques for its distribution. However, based on the aforementioned observations, we can infer that the attackers have specific targets in mind—specifically, administrators. This is evident in their use of scanner themes for phishing attempts, aiming to gain initial access.
DarkGate infection chain:
DarkGate can also be used as a loader malware, allowing its initial payload to manifest in various file formats. Some of the known file formats include .msi, .lnk, and .vbs. Now, we’ll explore the malware's typical infection. Below is the high-level overview of the typical DarkGate infection chain observed from multiple samples during the analysis period before publishing this blog, which is likely to change in the upcoming days.
Chain
-
Initially, DarkGate delivers various forms of payloads for initial access, such as
.msi,.lnk,.vbs,.js, etc., to the victim.
To view some different initial access payloads click, .js, .vbs, .hta, .msi, and .lnk. -
Once received, the victims execute the payloads using the default applications associated with the relevant file types.
-
Following the execution of the initial access payload, DarkGate executes Living Off The Land Binaries (LOLBins) to drop another stage of the payload.
-
The dropped payload may manifest as archive files, such as .cab, from which additional stages of payloads are extracted.
These stages typically comprise external binaries along with their associated malicious Dynamic Link Libraries (DLLs), facilitating DLL side loading. Usually these are dropped under%AppData%\Temp\[random-folder-name]\files\directory.
Alternatively, dropper payloads may be introduced from the third stage, wherein the execution triggers the download of executables. -
Following DLL side loading, DarkGate drops Autoit3 Binary and Autoit scripts.
Alternatively, following the execution of the dropped executables, the executable re-establishes connection with the Command and Control (C2) server to deliver the Autoit3 binary and Autoit3 script. -
Subsequently, DarkGate invokes Autoit3.exe to execute malicious AUscripts, containing instructions for extracting and deploying the loader.
-
Upon the execution of the loader, DarkGate deploys it main module.
Infection chain with MSI
We obtained a sample MSI (Microsoft Installer) file from MalwareBazaar to illustrate the analysis described below:
After the execution of the payload via msiexec, it proceeds to install the payload and displays the installation process of iTunes to the user.
In the background, it is creating a temp folder and dropping an archive file as shown in the below screenshot. After the folder creation, icacls.exe is used to set the integrity level of the directory to high
.cab aka Cabinet is a type of archive-file format for Microsoft Windows. The dropped files.cab is then extracted using the expand.exe binary.C:\Windows\system32\EXPAND.EXE -R files.cab -F:* files
The iTunesHelper binary and its DLL are extracted from the archive. Subsequently, iTunesHelper.exe, extracted from the archive, is executed. This action leads to the loading of the malicious DLL, which in turn drops Autoit and the corresponding .au3 script file.
Following this sequence, the dropped AutoIt script file is executed using AutoIt3.
The script includes instructions to gather system information, such as the Windows product ID and processor details, as part of its discovery process.
Subsequently, the backup of the Autoit3 binary and script files is created under the C:\ProgramData\[Random-name] directory. The backup is intended for establishing persistence at a later stage.
Following that, AutoIt3 executes malicious scripts to perform the discovery of security software instances on the system.
While analyzing the Autoit Script, we were able to extract some instructions, and there the script contains DllCall function of AutoIt3 which is displayed in the comment. The hex-encoded value shown below is the actual instruction, with the comment section for reference. We can see that AutoIt's DllCall function is used to call the VirtualProtect function from the kernel32.dll library to modify the memory protection attributes to facilitate code injection.
When security software isn't detected, modifications are made to the values of the StartMenuExperienceHost registry key, located at:HKLM\System\CurrentControlSet\Services\bam\State\UserSettings\S-1-5-21-1984999317-268798495-3946344884-500\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy.
Following the modification, the StartMenuExperienceHost initiates the MicrosoftEdgeUpdateCore.exe process. Process injection is performed on the MicrosoftEdgeUpdateCore.exe process.
Subsequently, from the injected process, another round of security software discovery is carried out. Then, the previously created backup of AutoIt3 and its script are set up for persistence by placing them under the RUN registry. Additionally, the process establishes connections to the command-and-control (C2) server.
Additionally, it removes traces of the initial files by deleting them using command prompt commands.
Infection chain with LOLBINs
Moving on to examine a slightly different method, we've got another .msi sample to look into.
Same as above, we executed the payload with msiexec. After the execution, we were able to observe the following disk operations, where %APPDATA%\MSI14499 directory was created and multiple files were written: Microsoft.Deployment.WindowsInstaller.dll, WixSharp.dll and WixSharp.UI.dll.
Additionally, during the application installation process via msiexec.exe, DLL files masquerading as .tmp were also dropped in the C:\Windows\Installer folder.
After that rundll32 was invoked to execute the malicious functions of those DLLs dropped under C:\Windows\Installer by calling relevant export functions, so that's why multiple invocations of rundll32.exe are displayed in the below process tree.
One of the DLL files contains instructions to download the payload from the C2, so when the DLL is executed via rundll32.exe it connects to C2, and downloads another executable.
The dropped executable pm320240221_214000.exe seems to be a loader based on the activities it performs, which are mentioned in the following sections.
After the execution of the binary, it modifies the internet settings as displayed below.
Then it attempts to connect to the C2 server to drop autoit3.exe and its malicious script file. However, due to the C2 server being down during the time of our analysis, we couldn't observe the behavior.
But below is the SS of the network connection observed in Virustotal where the binary was connecting to C2 and downloading autoit3.exe binary and payload script file.
DarkGate capabilities
Let’s take a closer look at some of the configurations that we saw while performing analysis on the main DarkGate malware. Features might or might not be executed based on the adversaries' objectives.
Security software discovery
Before executing malicious functions, DarkGate and its loader perform initial security checks where they attempt to discover if certain folders and processes exist or not. The major security software and antivirus programs are mentioned below:
Bitdefender
Avast
AVG
Kaspersky EndPoint Security
Kaspersky
Eset - Nod32
Avira
Norton
Symantec
Trend Micro
McAfee
G DATA
SUPER AntiSpyware
Comodo
Malwarebytes
ByteFence
Spybot - Search & Destroy
360 Total Security
Total AV
IObit Malware Fighter
Panda Security
Malwarebytes
Emsisoft
Quick Heal
F-Secure
Sophos
Lateral movement
Terminal setting modification
The sample we analyzed contains code to modify network configuration, setting the TrustedHosts value for WS-Management to "127.0.0.2". Then it modifies terminal settings to override default RDP settings and security configuration related to RDP.
Creation and storage of remote credential
As settings related to RDP have been modified, credentials for RDP have been created and have been stored using cmdkey binary that could be used, for example, to provide automated authentication when accessing a network resource or service that requires these credentials.
Execution of Psexec
DarkgGate is configured to create a user profile, which it uses for lateral movement within the compromised network. It employs Psexec to remotely execute processes, facilitating its spread across networked systems.
Credential access
DarkGate is equipped with the ability to extract credentials from the victim system. In our analysis of the samples, we noted configurations tailored specifically to extract credentials from popular browsers such as Edge, Firefox, Chrome, Brave, and Opera. Its primary focus lies on files that store browser cookies.
Examples of targeted file paths include:
-
Opera Software\Opera GX Stable\Network\Cookies
-
Opera Software\Opera Stable\Cookies
-
BraveSoftware\Brave-Browser\User Data\Default\Network\Cookies
-
Microsoft\Edge\User Data\Default\Network\Cookies
Additionally, besides its focus on targeting web browsers, we observed DarGgate containing configurations to execute popular password extraction tools from Nirsoft. These tools include MailPassView, capable of extracting credentials from various email clients, and WebPassView, which can extract credentials from browsers such as Chrome, Firefox, Opera, and Internet Explorer.
In addition to the aforementioned techniques, the malware also leverages cmdkey, a built-in Windows binary, to enumerate and extract credentials from the compromised system. By using this utility, the malware can list out and potentially extract various types of credentials stored on the system, including those associated with network resources, remote servers, or user accounts.
The GetKeyboardState API function, intended for legitimate keyboard input handling, can be exploited to create a keylogger. By installing a global keyboard hook, an attacker can monitor keystrokes system-wide. Periodically calling GetKeyboardState allows the detection of key presses, which are then logged along with metadata. To evade detection, the keylogger may employ encryption or other obfuscation techniques. However, it's important to note that developing and deploying keyloggers without authorization is illegal and unethical.
Software for malicious ends
AnyDesk
DarkGate contains a configuration to download and run AnyDesk in the victim system, which grants remote system management for threat actors.
hVNC
In addition to its capability to use AnyDesk for remote desktop access, DarkGate also supports remote desktop access using hidden Virtual Network Computing (hVNC).
Miners
Darkgate can deploy miners into the victim system. It has been configured to stop the miner if task manager and tools such as process explorer and process hacker are detected.
Detection
Required log sources
The following should be enabled:
-
Windows
-
Windows Sysmon
Detecting execution of initial access payload
From the above analysis, it is clear that when DarkGate executes .msi initial access payload, there are set of processes that are spawned afterward. To look for such a process, one can simply search for the child process of msiexec.exe
Using the above generic query to search for a child process created by msiexec.exe, the analyst can use a filter to display the above-observed techniques:
Besides the use of MSI files, other file formats are also used as initial payload, which can be detected using the following alerts:
-
Suspicious Execution of LNK File
Also, the below alerts can be used to detect specific events related to the suspicious use of expand.exe and icacls.exe binary by DarkGate payloads.
-
File or Folder Permissions Modifications
-
Suspicious File Extraction via Expand Detected
Suspicious Rundll32 activity detected
Recent samples have use rundll32 to download the DarkGate loader into the system. Analysts can use this alert to detect the execution of malicious DLLs that result in the download of the loader into the system via rundll32.
Detecting traces and execution of AutoIT3 and script files
Now after detecting artifacts related to the execution of initial access, we can search for one of the unique techniques used to deploy the DarkGate malware, for example the use of Autoit3 and its malicious scripts:
Analysts can use the below query to detect events where Autoit3 and script files are being created
After the binary and script files are downloaded, they are executed to drop other stages of the payload
For persistence, the AutoIt3 binary and the script are written in another folder. Later, they are configured for persistence by placing them in the run registry. Therefore, analysts can use the Autorun Keys Modification Detected alert to detect such events.
Detecting modification of internet settings
Before connecting to the C2, the loader tries to change Internet Settings to prevent any issues during communication with the C2.
Note: The mentioned registry path in the query needs to be added in Sysmon Configuration or SACL needs to be configured to generate relevant logs.
Detecting techniques related to DarkGate
DarkGate uses psexec for remote command execution, which can be detected using the following query.
As DarkGate is known to retrieve credential and cookies data from the web browser below, analysts can use the query to hunt for such events, if appropriate SACL is configured to the relevant folder with Audit File System.
Note: Appropriate SACL needs to be configured beside File System Auditing
DarkGate can change the configuration related to Terminal Service, which can be detected using the following query:
Typically, miners are executed with the --cpu-priority command-line argument. As DarkGate can deploy miners into the system and during the analysis of a sample, we observed hardcoded command-line configurations. Analysts can use the following query to detect process creation events of miners.
DarkGate also deploys AnyDesk for remote access, so analysts can use the below query to detect traces of AnyDesk installation and execution.
Responding to DarkGate
Upon detecting traces of the DarkGate malware, analysts can use the provided hunting queries to establish them as triggers for subsequent playbooks. These playbooks automate the response process against DarkGate infections.
Logpoint AgentX Remove Item
DarkGate tends to create backup files and drop multiple payload files. By detecting relevant files related to DarkGate, analysts can use Remove Item playbook to delete those files, or an analyst can set relevant triggers to automate the process of running the playbook.
Logpoint AgentX Terminate Process
Based on the queries and alerts mentioned earlier, if the malware process remains active, analysts can use the Terminate Process playbook to terminate it promptly.
Logpoint AgentX Delete Registry Value
Analysts can use the Delete Registry Value playbook to delete the suspicious registry value added in the Run registry key for persistence by the DarkGate loader.
Logpoint AgentX Isolate-Unisolate Host
After verifying the host is infected, analysts can use the Isolate-Unisolate Host playbook to isolate the host to prevent further lateral movement and pivoting.
Recommendations
-
Malware like DarkGate and other malware families are distributed via social engineering tactics. To combat these threats, organizations should provide regular training to employees on recognizing and responding to social engineering attacks, including simulated exercises that replicate real-world scenarios.
-
In addition to enforcing a robust password policy, where password resets occur once a year, raising awareness about password hygiene is crucial. Users should avoid reusing passwords across multiple accounts to prevent adversaries from accessing other services if one password is compromised. Additionally, implementing Multi-Factor Authentication (MFA) on all users, if feasible, otherwise MFA for privileged users or cloud accounts adds an extra layer of security by requiring multiple forms of verification, making it harder for adversaries to gain access.
-
Implement least privilege to restrict user access and permissions, giving employees only what is necessary for them to perform their job functions. By doing so, organizations can significantly reduce the risk of unauthorized access or malicious activity if the user account is compromised.
-
The use of endpoint protection systems is pivotal in detecting and blocking malware, as demonstrated by DarkGate terminating its actions upon detecting specific antivirus products.
-
Implementing proper network segmentation is vital for safeguarding essential systems and sensitive data from malware and adversaries. By keeping these critical assets isolated from the rest of the network, organizations can reduce the risk of lateral movement or pivoting.
-
Regularly auditing privileged accounts and their activities helps detect misuse or anomalies that could lead to data breaches, system failures, and other security incidents. By closely monitoring privileged access, organizations can identify suspicious behavior and take prompt action to mitigate risks, enhancing overall security.
-
Regularly updating devices, browsers, and other software applications is a critical security practice that can help protect systems from known vulnerabilities and cyber threats.
-
Proper logging, asset visibility, and system monitoring are crucial for cybersecurity. They offer network oversight and anomaly detection. Regular monitoring and auditing track user activity and identify unusual behavior. Comprehensive log collection from all systems is essential.
-
Threat actors leverage Remote Monitoring and Management (RMM) tools such as AnyDesk, Atera, etc., for remote desktop access. Organizations should monitor the use of such tools. Additionally, it is crucial to monitor the installation of applications because, as observed with DarkGate, it installs applications at multiple stages of the attack cycle.
-
If feasible, configure an appropriate host-based firewall policy to limit the outbound communication from certain applications such as Wscript, Rundll32, and Mshta, which are extensively abused by threat actors to drop other stages of payloads.
-
Additionally, it is recommended to have an adequate log retention policy in place to ensure that log data is available for analysis in the event of an incident. For better visibility, it is recommended to have a log retention time of at least six months.
-
Finally, ensure that an incident response plan is in place for prompt action upon incident detection, aimed at minimizing damage.
For centralized logging and visibility, Logpoint can help with an end-to-end security operations platform, Converged SIEM. Logpoint covers the entire threat detection, investigation, and response process with SIEM, SOAR, and UEBA, including a native endpoint agent. For more information on getting started with Logpoint, book a demo to see Converged SIEM in action.









































