Guide to the MITRE ATT&CK Framework: What is it and how can it benefit you?
What is the MITRE ATT&CK Framework?
Cybersecurity criminals around the world are constantly trying out new strategies to target and attack organizations. Fortunately, there is a way to observe these strategies and use this knowledge against them. Developed by MITRE, a non-profit funded by the U.S. government, the ATT&CK Framework is a cybersecurity knowledge base of adversary tactics and techniques based on real-world observations. The Framework is useful in many different aspects of cybersecurity, helping organizations increase threat intelligence and strengthen network defenses against attacks.
The ATT&CK Framework is a universal way to classify adversarial tactics. It has the advantage of being backed up by a community-driven knowledge base of adversarial techniques. The unified Framework enables security professionals to communicate more clearly and share information more efficiently, which ultimately contributes to a higher level of security globally.
What are the tactics of the ATT&Ck Framework?
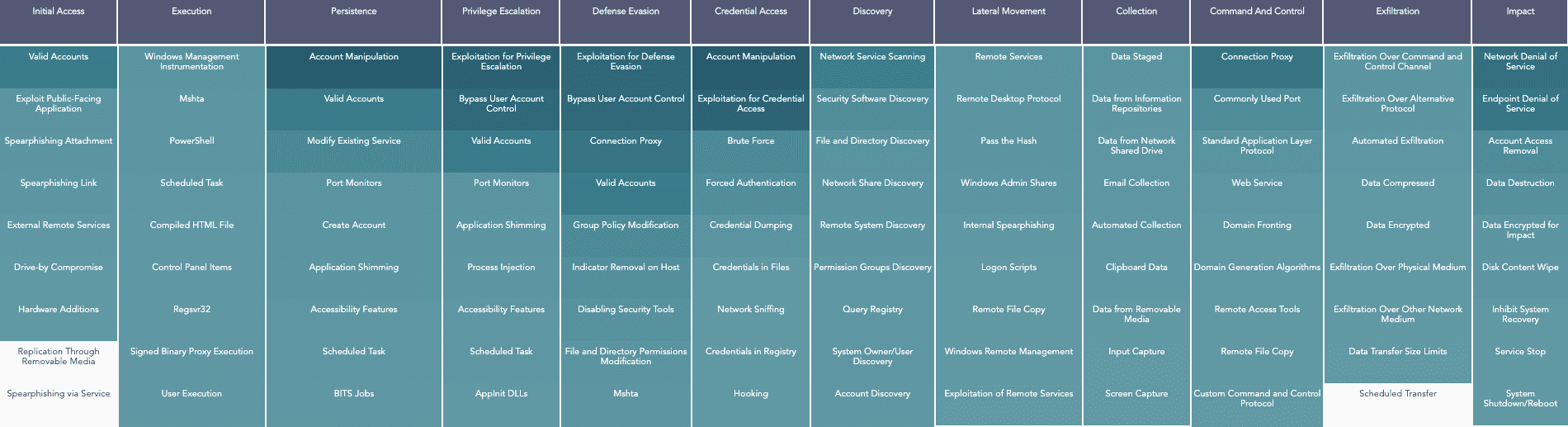
Tactics are the core of the ATT&CK Framework and represent the “why” of an ATT&CK technique. It is the adversary’s tactical objective: the reason for performing an action. Tactics group together the different methods attackers use, such as persist, discover information, move laterally, execute files, and exfiltrate data. MITREretired PRE-ATT&CK and instead introduced two new tactics relating to adversary behavior prior to attack to the ATT&CK Framework. Currently, the MITRE ATT&CK Framework consists of 14 easy-to-understand tactics.
| Tactics name | The adversary is trying to… |
|---|---|
| Reconnaissance | Gather information to plan future operations. |
| Resource Development | Establish resources to support operations. |
| Initial Access | Get into your network. |
| Execution | Run malicious code. |
| Persistence | Maintain their foothold. |
| Privilege Escalation | Gain higher-level permissions. |
| Defense Evasion | Avoid being detected. |
| Credential Access | Steal account names and passwords. |
| Discovery | Figure out your environment. |
| Lateral Movement | Move through your environment. |
| Collection | Gather data of interest to their goal. |
| Command and Control | Communicate with compromised systems to control them. |
| Exfiltration | Steal data. |
| Impact | Manipulate, interrupt, or destroy your systems and data. |
What are the MITRE ATT&CK techniques?
The MITRE ATT&CK techniques are grouped by tactics and are based on a set of actions that adversaries perform to accomplish their nefarious objectives.
Each ATT&CK technique has been observed being used by malware or threat actor groups in attempts to compromise enterprise networks. Techniques are essentially a playbook or a “how to” allowing defenders to prepare for the attack: How are attackers getting into your network? How do they avoid being detected? How are they moving through your network environment?
Going one step further, the sub-techniques are more specific techniques. While techniques indicate the general action an adversary takes to achieve a goal, the sub-techniques are more detailed adversary actions. For example, a technique such as Phishing has three sub-techniques that provide more details about how adversaries send phishing messages to gain access to systems.
The techniques library in the ATT&CK Framework is constantly evolving and consists of more than 150 techniques and 270 sub-techniques divided into the above-mentioned 14 tactics.
What are the benefits of using the MITRE ATT&CK Framework with your SIEM?
SIEM vendors are always on the lookout for ways to improve their solution to gain more insights and information that can help detect and respond to an attack. The ATT&CK Framework allows analysts to better understand the specifics of an attack, which they can then communicate to team members. This makes the threat detection and response time even faster.
The ATT&CK Framework is beneficial throughout an organization. It’s a great tool for communicating with senior leadership and security managers. Using ATT&CK, it’s much easier to produce a more accurate overview of incidents. Auditors and CISOs often require information such as dashboards and reports. The Framework can help with automating the creation of the required information.
MITRE ATT&CK in LogPoint
LogPoint has mapped all analytics to the ATT&CK Framework, which bridges the gap between why an alert is firing and what it means. When alerts correspond to an ATT&CK technique, security analysts can more quickly understand how an alert relates to a larger attack so they can take the necessary steps to protect their business. Analysts can also use the ATT&CK visualizations in LogPoint to track the stages of an attack and assess security coverage.
When it’s time to communicate with other employees to document the value of the SIEM and how many alerts are coming in, analysts can easily pull a report from LogPoint that includes the ATT&CK IDs. The Framework is steadily becoming an industry standard, which makes it easier to map security coverage and risks because alerts and defenses are based on the same ATT&CK taxonomy.
Who is MITRE?
After reading all the benefits about the ATT&CK Framework, you might be interested to know more about the people behind it. Formed in 1958, the MITRE Corporation is a U.S. non-profit corporation based in Bedford, Mass., and McLean, Va., and funded by the U.S. government. The company operates federally funded research and development centers that assist the United States government with scientific research and analysis.
Recently, MITRE released another tool called Shield, which is a framework of defensive actions to help organizations counter current attacks. With the ATT&CK and Shield Frameworks, companies have a comprehensive way to detect adversary behaviors and implement defensive methods to help protect their business.



