Decoding the Threat: HTML Smuggling Detection Essentials
Modern web applications perform most of their processing and rendering on the client side, enhancing dynamic and interactive web experiences. However, this architecture introduces a security concern known as HTML smuggling.
Many threat actors such as Nobelium, and Nokoyawa have been using this technique to distribute their malware families as other forms of delivery are well known, and are monitored for as a result have high chances of detection. Besides that, macros from the internet are blocked by default, so adversaries have started using this technique.

What is HTML Smuggling?
HTML Smuggling is a technique that involves embedding malicious Javascript code within a legitimate HTML file. This technique abuses the capabilities of HTML5 and JavaScript, which are supported by every modern web browser. This technique allows adversaries to create their payload in the victim machine.
The technique helps threat actors avoid filters that check for suspicious file types like ZIP, ISO, EXE, etc. It also lets them slip past defenses that focus on network activity, as the HTML file looks normal to those defenses, just like any file used in a web browser. This technique is less likely to get detected compared to other methods because the malicious payloads are created right in the victim's browser using JavaScript code. Also, adversaries can always resort to obfuscation or encoding to hide their payload. Threat actors and malware families such as Qakbot, IceId, and Pikabot have used this technique to deliver their payload.
How HTML Smuggling Works
The first step includes adversaries first creating an HTML file and embedding their payloads into the file. After this, they have various ways of distributing their payload to the victim. They can resort to phishing by sending the HTML file directly to the victim or they can send the URL of the site where their payloads are hosted. They can also use the Drive-by-Compromise technique to make victim load their payload in their browsers.
When the victim opens the HTML file or visits the link sent by adversaries, the HTML smuggling payload is loaded on a web browser, and the malicious JavaScript code inside the HTML file is executed by the browser. As a result, by using JS, a payload is built by the browser and is dropped in the victim system.
The dropped payload can be of any file format, but in most of the cases, we have observed the payload dropping zip files. Adversaries have also dropped the .iso file directly from the HTML payload, to learn more about the iso payload visit this link. Using .iso files they can also bypass the Mark of the Web (MOTW) functionality of Windefender, which gives Microsoft Defender SmartScreen an opportunity to perform an additional inspection of the content.
The HTML file or link sent to the victims, may mimic legitimate sites or simply contain instructions for further execution or passwords to extract the download files.
Detecting HTML Smuggling with Converged SIEM
Required Log Sources
-
Windows
-
Process Creation with command-line auditing should be enabled
-
Audit File System should be enabled
-
-
Windows Sysmon
HTML Files Downloaded
HTML Smuggling first starts with adversaries convincing victims to download the “HTML” payload, so the below query can be utilized to detect such events.
Hunting for HTML Execution by Browsers and Detection of File Download
After the download and execution of the HTML payload by the user, the HTML file will be loaded by the default browsers. The below investigation query can be utilized to search for events where common browsers such as Internet Explorer, Chrome, Edge, Firefox, and Brave are loading an HTML file, which later drops a zip file in the system.
If you don’t have Sysmon enabled but have configured the Audit File System with appropriate SACL configuration, then below can be utilized to detect a load of HTML files by browsers and download a zip file.
If you don’t have Sysmon or File System Audit setup then, there is an alternative to the above hunting query but may yield more false positives than above. Without Sysmon and File System Audit we cannot detect file download events, so here we will be trying to look for events where browsers are trying to load HTML files.
Download of ZIP File
After the execution of the HTML payload, a zip file is dropped into the system.
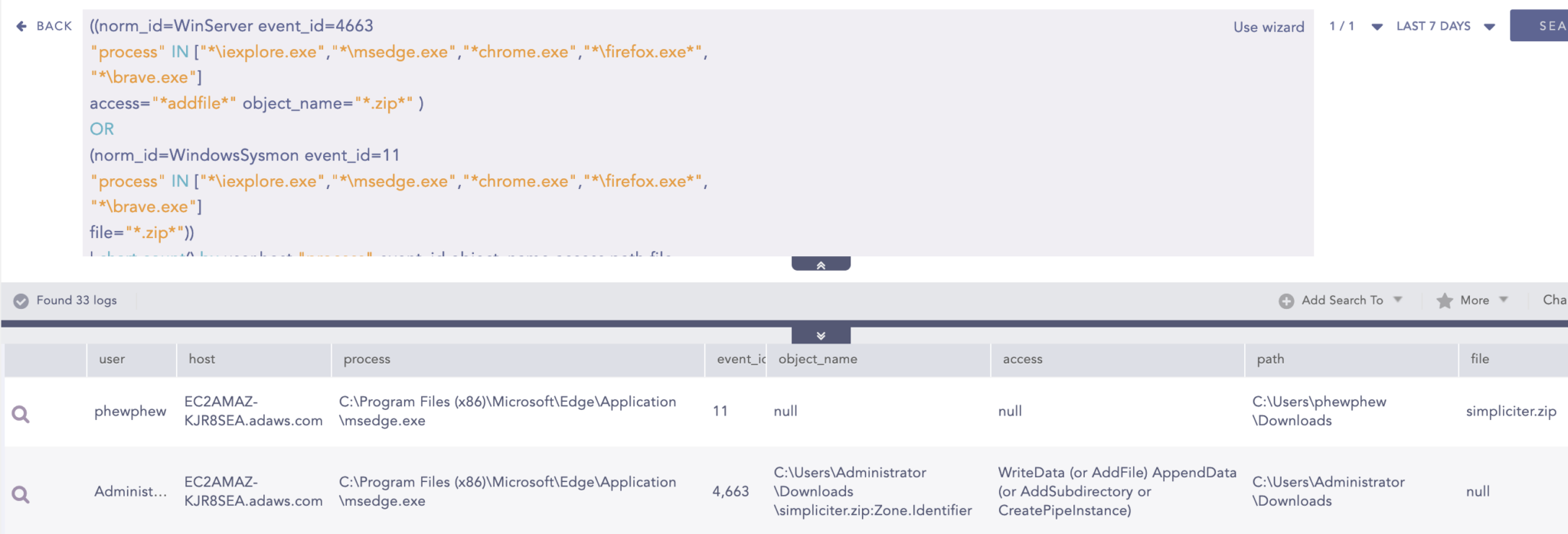
Note: For the Detection Query we have emphasized the download of ZIP files but analysts can search for any other file types by simply removing the zip filter from the query or they can add another file extension such as “.iso”, “.doc” and others.
Response to HTML Smuggling with Converged SIEM
After setting up the above hunting queries on trigger, the analyst can set the following playbooks for automated response against HTML Smuggling:
Once the queries are set as triggers, analysts can use the Logpoint AgentX Remove Item playbook which allows them to automate the process of response by deleting the zip file.
After analysts have verified a host to be infected they can use the Logpoint AgentX Isolate-Unisolate Host playbook as a last resort option to isolate the host to prevent lateral movement and reduce damages.
Recommendations
-
Social engineering tactics are designed to deceive victims into downloading and executing malware. To combat these threats, organizations should provide regular training to employees on recognizing and responding to social engineering attacks like phishing mail, including simulated exercises that replicate real-world scenarios.
-
Utilize web filtering tools to block access to malicious websites and implement robust email security measures, including anti-phishing and anti-malware solutions. Also policy to prevent users from downloading files with suspicious extensions should be implemented where possible.
-
Implementation of least privilege to restrict user access and permissions to only what is necessary for them to perform their job functions. By doing so, organizations can significantly reduce the risk of unauthorized access or malicious activity if the user account is compromised.
-
Regularly auditing privileged accounts and their activities is crucial because these accounts have elevated access and permissions that can potentially give malicious actors unauthorized access to sensitive data or critical systems. Without proper monitoring, privileged accounts may be misused, leading to data breaches, system failures, and other security incidents that can cause significant harm to an organization. Additionally, auditing privilege accounts can provide valuable insights into how these accounts are used, allowing organizations to make informed decisions about access control, resource allocation, and risk management.
-
Regularly updating your devices, browsers, and other software applications is a critical security practice that can help protect your systems from known vulnerabilities and cyber threats. By keeping your software up to date, you can ensure that you have the latest security patches and bug fixes installed, which can help prevent potential malware infections and data breaches.
-
Having proper logging, visibility of assets, and monitoring of systems are essential components of a robust cybersecurity strategy. These measures provide an overview of the network and help to detect anomalies that may indicate a security threat. It is important to monitor and audit the network regularly to keep track of user activity and network traffic and identify any unusual behavior. It is also crucial to ensure that logs are being collected from every system to ensure comprehensive coverage.
-
Additionally, it is recommended to have an adequate log retention policy in place to ensure that log data is available for analysis in the event of an incident. For better visibility, it is recommended to have a log retention time of at least 6 months. Still, it may be necessary to retain logs for longer periods depending on regulatory or compliance requirements.
For centralized logging and visibility, Logpoint offers an end-to-end security operations platform called Converged SIEM. It covers the entire threat detection, investigation, and response process with SIEM, SOAR, and UEBA, including native EDR capabilities thanks to AgentX, a native endpoint agent.












