Emerging Threat: The PLAY with OWASSRF
Executive Summary:
- First appeared in June 2022, still active and victimizing high-profile targets.
- Second Highest number of victims in the first week of January.
- Bypasses ProxyNotShell mitigations by exploiting OWASSRF vulnerability.
- After encrypting files, It adds “.PLAY” as an extension of the files and hence the name.
- Also known as “PLAYcrypt”, its behavior is similar to Hive and Nokoyawa ransomware.
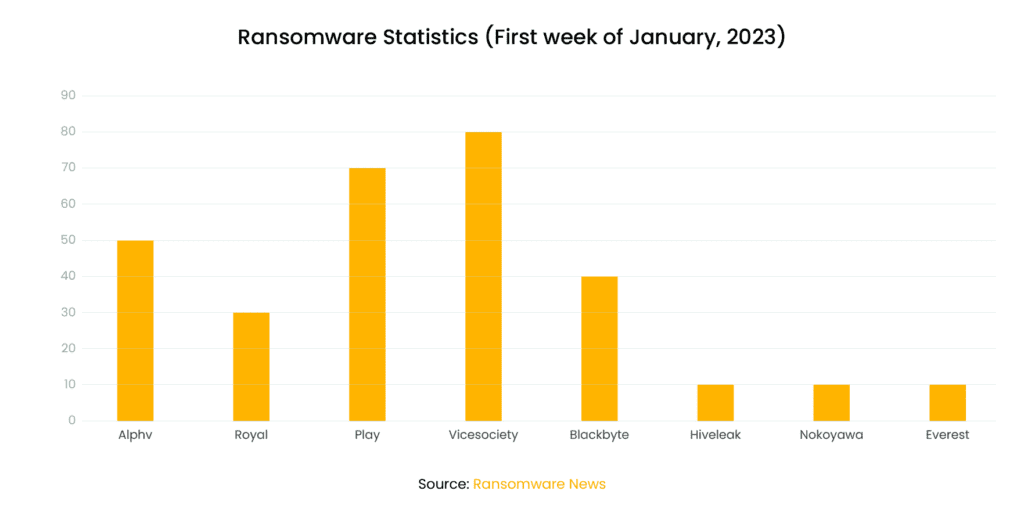
Ransomware statistics for the First week of Jan 2023 from Ransomware News.
Affecting a significant number of victims in the first week of January, “PLAY” ransomware got our, and probably your, attention. Multiple high-profile enterprises have been affected by this ransomware causing disruption in their functionality and also costing them a fortune. Some of the victims are “Argentina’s Judiciary of Córdoba”, German hotel chain “H-Hotels”, the city of “Antwerp”, and “Rackspace”. Detail of which are explained in the report.
PLAY’s Origins
It was named “PLAY” from the fact that It adds “.PLAY” as an extension after the encryption of files. Apart from the familiar ransom notes which contain more threatening and detailed information, its ransom note is unusually simple, containing only the word “PLAY” and an email address. Also, instead of ransom notes being created in every folder, PLAY's ransom note “ReadMe.txt” is only left at the root of a hard drive (C:).
Play’s victims first surfaced in the Bleeping Computer forums in June 2022. Only a few reports have been released on this particular ransomware so far. Its behavior and tactics are similar to HIVE and Nokoyawa ransomware. As of 30th January 2023, the FBI has shut down the Hive network seizing the infrastructures used by the Hive ransomware. However, It hasn’t yet mentioned any information on PLAY. Many speculate that they are somewhat related and use some of the same infrastructures so there is a possibility that this might affect PLAY ransomware, but there is also a good chance that the actors behind Hive might focus solely on PLAY ransomware and increase its activities.
The tactics deployed
A report published by Chuong Dong containing anti-analysis and encryption features mentions that the operators are using common Big Game Hunting (BGH) tactics, such as SystemBC RAT for persistence and Cobalt Strike for post-compromise tactics. They are using custom PowerShell scripts, AdFind, WinPEAS, WinSCP, etc. The ransomware code is highly obfuscated with anti-decompiling features in place bypassing most static analysis via IDA’s disassembly and decompilation. It has also applied intermittent encryption techniques, to evade detection based on conventional encryption methods. CrowdStrike Identified a new exploit method for Exchange servers that could bypass ProxyNotShell mitigations, dubbed OWASSRF. This vulnerability is the combination of CVE-2022-41080 and CVE-2022-41082 which attackers use to achieve remote code execution (RCE) via Outlook Web Access (OWA).
What happens in the process
PLAY ransomware has been seen to exploit this particular vulnerability to gain initial access to the victim's machine. It is also known to exploit domain, local, and virtual private network (VPN) accounts, exposed remote desktop protocol (RDP) servers, and FortiOS vulnerabilities CVE-2018-13379 and CVE-2020-12812 to gain initial access to the system. Like other modern ransomware, It also utilizes the living-off-the-land binaries (LOLBins) for its attacks, and data is exfiltrated prior to the deployment of the ransomware.
This ransomware group has a contact portal where the victims can contact them. This website is accessible only via Tor and is also used for disclosing the victim’s details and leaking stolen data should the victim fail to pay the ransom.
It has an “FAQ” section with brief information on the actions taken by the ransomware group, and steps for them to get hold of their data back. This ransomware group is also following a recent trend among ransomware operators whereby they obfuscate the victim’s name on the leak site to apply additional pressure on victims during negotiations, thus encouraging them to pay them ransom in order to prevent their full name from being disclosed publicly.
For more information on Emerging Threats Protection service, you can contact our Global Service team for help developing and implementing the playbooks seen in the report included in this blog.
Our Security Research team’s report contains the key details on hunting, preventing, and responding to PLAY ransomware using Logpoint SIEM and SOAR.
You can download the report in the link here or click the image in the top right of the blog.










