Uncoiling the Enigma of Russian Intelligence’s “Snake Malware”
You could be forgiven for thinking it’s the month of snake, as the Russian Intelligence’s “Snake Malware“ is all over the news. When it comes to making headlines, cyber-espionage groups linked to Russia are unparalleled, with ever-evolving tools and techniques, challenging our defenses and pushing the boundaries of digital warfare. This month, “Snake Malware“, which according to CISA, stands out as the most sophisticated cyber-espionage tool crafted by Center 16 of Russia’s Federal Security Service (FSB) for long-term intelligence collection on sensitive targets. With its stealthy nature and sophisticated capabilities, this serpentine menace has slithered through networks, leaving chaos and compromised systems in its wake.

This insidious cyber threat is intercontinental, encompassing the vast territories of North America, South America, Europe, Africa, Asia, and Australasia. Its pervasive presence spans over 50 countries, leveraging infrastructure across all industries, and operating with meticulous precision to infiltrate and extract sensitive information and intelligence from a diverse array of high-priority targets. From penetrating the fortified networks of NATO member states to infiltrating research facilities and monitoring the activities of journalists, Snake relentlessly pursues its mission of clandestine information gathering.
Here, we navigate the treacherous terrain of advanced persistent threats, dissect the intricate strategies employed by Russian intelligence, and examine the devastating consequences of Snake Malware infiltrations. Join us, as we uncoil the enigma and unveil the true menace of Russian Intelligence's "Snake Malware", the dangers, and the urgent need for vigilance in the face of this ever-present threat.
So, What is Snake?
Nope, not the elongated, limbless, largely carnivorous reptile; nor the legendary Nokia game of the 90s.
Snake, previously “Uroburos“, is considered to be the most sophisticated cyber espionage tool developed entirely in C by the Ryazan-based FSB group “Turla”. The Federal Security Service of the Russian Federation (FSB, Federal'naya Sluzhba Bezopasnosti) devised an ingenious strategy utilizing "Snake Malware” and established a global network of infected computers, employing a peer-to-peer (P2P) architecture. Within this extensive web, numerous systems act as relay nodes, discreetly guiding disguised operational traffic to and from the Snake implants deployed on the FSB's primary targets.

Image of Uroburos by Jakob Böhme embedded in Snake components (CISA)
To ensure confidentiality and impede detection or interception, Snake employs custom communications protocols featuring encryption and fragmentation techniques. These measures serve to thwart the efforts of detection and data collection, adding an additional layer of complexity to the malicious activities orchestrated by the FSB. Additionally, Snake boasts an internal technical architecture that enables effortless integration of new or replacement components. This design not only facilitates the development process but also promotes seamless interoperability among Snake instances operating on different host operating systems, including Windows, MacOS, and Linux.
In response to the reporting by cybersecurity and threat intelligence firms regarding the tactics, techniques, and procedures (TTPs) employed by Snake, the FSB swiftly adapted/modified the malware implant eluding detection and therefore intensifying the hurdles faced in identifying and capturing Snake and its associated artifacts. As a result, the cat-and-mouse game between defenders and the elusive Snake malware continues to evolve, with the FSB consistently striving to outmaneuver detection mechanisms.
Infection Chain
The FSB demonstrates a consistent pattern of targeting external-facing infrastructure nodes within a network. From there, they employ a combination of tools and tactics to exploit system vulnerabilities and gain access to the internal network. Once initial access is secured, the FSB initiates an enumeration process using a diverse range of methods, including keyloggers, network sniffers, and even open-source tools to map out the network and acquire crucial administrator credentials, often focusing on gaining access to domain controllers.
Once the FSB operators have successfully mapped the network and obtained administrator credentials for various domains, they proceed with regular data-gathering operations. To ensure minimal presence in the system, no additional heavyweight implants are deployed; rather the acquired credentials and lightweight remote-access tools are leveraged to navigate and operate internally within the network. As an added measure, FSB operators sometimes deploy a compact remote triggerable reverse shell as a backup access vector alongside Snake, for lateral movement.
The Good Guys, Fight Back
CISA states, despite the advanced nature of the Snake malware, mistakes made during its development and operation proved to be valuable entry points into understanding Snake's inner workings and enabled the development of capabilities for tracking and manipulating its data. The FSB's utilization of the OpenSSL library for the Diffie-Hellman key exchange exposed a significant vulnerability. Snake's key set generated during the exchange employed a woefully inadequate prime length of only 128 bits, rendering it insecure for asymmetric key systems. Additionally, in hurried deployments of Snake, operators neglected to remove certain components, inadvertently exposing function names, cleartext strings, and developer comments.
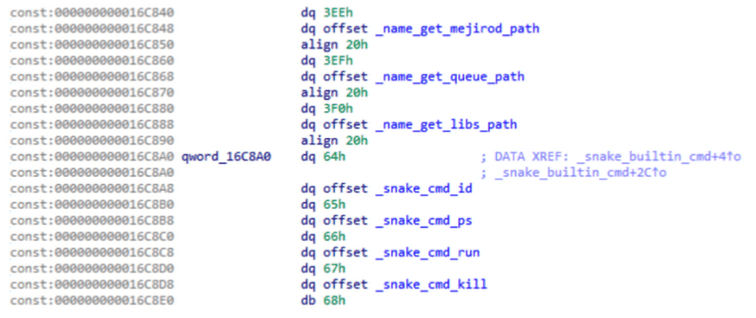
Function names, cleartext strings, and developer comments in Snake’s code (CISA)
The United States Department of Justice made a significant announcement on Tuesday, May 9th, unveiling the successful execution of an authorized operation code-named "MEDUSA" dismantling the sophisticated malware, called “Snake”, that the U.S. Government attributes to a unit within Center 16 of the Federal Security Service of the Russian Federation (FSB). The FBI introduced a specially developed tool called "PERSEUS," which issued strategic commands triggering the Snake malware to overwrite its crucial elements, leading to its self-destruction or permanent disablement. Notably, this operation meticulously safeguarded the integrity of legitimate applications and files on the affected computers, ensuring they remained unaffected throughout the process.
Furthermore, the FBI has released a plugin for the Volatility memory analysis framework, designed to comprehensively examine system processes to identify the presence of the Snake user mode component injected into any process. Once detected, the plugin provides a detailed listing of the injected process and the specific virtual memory address where the Snake user mode component is loaded. This plugin serves as a valuable tool for analysts conducting thorough memory analysis to uncover and analyze instances of Snake malware within compromised systems.
Detection of Snake Malware Artifacts with Logpoint Converged SIEM
Knowing you've been breached is a highly distressing scenario, coupled with the theft of sensitive data only compounds the severity. Therefore, organizations must be prepared to respond swiftly if a threat, Snake as such, manages to breach your defenses. Logpoint Converged SIEM empowers you to expedite the threat detection process, equipping you with the tools to take proactive action.
Required Log Sources
-
Windows
-
Windows Sysmon
-
Firewall
-
IDS/IPS
Detection with Logpoint Queries
The malware is deployed with the primary intent to discreetly infiltrate the target system without being detected. The following queries allow us to detect Snake artifacts i.e. driver files and other executable files, deployed in the target systems:
1. Detect Potential Snake Malware Kernel Driver File
2. Detect Files Possibly Associated with Snake Malware
3. Detect Potential Snake Malware Installation Binary
Detection with Logpoint Alerts
Following deployment, the malware maintains a long-term persistence in the system to exfiltrate as much data and information as feasible. Throughout this operation, it heavily relies on system binaries like "rundll32.exe" and "Werfault.exe". It then begins to execute its final goals i.e. data exfiltration, and connecting to suspicious servers.
The subsequent section outlines detection for the methods employed in this process.
1. Suspicious Rundll32 Activity Detected
2. Snake Malware Covert Store Registry Key Detected
*Note: Registry Auditing should be explicitly enabled for this alert to trigger.
3. Suspicious WerFault File Creation
4. Suspicious WerFault Service Creation
Incident Response with Logpoint SOAR and AgentX
Within Logpoint Converged SIEM, two powerful tools are at your disposal to combat the Snake malware infection: SOAR, and AgentX, our native endpoint agent. AgentX in combination with SIEM and SOAR gives EDR capabilities to our Converged SIEM solution and comes with built-in telemetry that enriches SOAR events, allowing for automated and timely responses to security incidents and therefore reducing the scope of impact.
Logpoint AgentX is available now: Contact your representative
To counter detected persistence attempts triggered through the alerts mentioned in the previous detection section, the following Logpoint SOAR playbooks can be leveraged to take appropriate actions against registry values, processes, scheduled tasks, and start-up services and eliminate them.
1. AgentX Delete Registry Value
2. Logpoint AgentX Terminate Process
3. Logpoint AgentX Delete Scheduled Task
4. Logpoint AgentX Disable Startup Service
Remediation and Mitigation
-
Regularly scan and assess organizational assets for vulnerabilities and misconfigurations, to patch them, and maintain updated Operating Systems, firmware, and applications.
-
Secure and limit connections to external-facing servers
-
Ensure all the traffic passes through a properly configured firewall.
-
Follow a "deny all connections by default" approach, allowing only explicitly required connections for specific system functionality.
-
Limit the number of open ports and services running on the server to minimize the attack surface.
-
Implement VPN access for remote administration and ensure it is properly configured with strong encryption and authentication methods.
-
-
Educate users about the risks of downloading and executing unknown files or visiting suspicious websites, as these can be potential sources of keyloggers and network sniffers.
-
Password Policy & Hygiene
-
Develop and extensively implement an organization-wide password policy that defines
-
immediate requirements to change the default password,
-
a globally accepted minimum password length and password expiry period,
-
the complexity involved, and more.
-
-
Strongly enforce MFA and phishing protection for both user and administrative accounts. Adopt the practice of least privilege and time-based access, where possible.
-
Immediately change credentials from a non-compromised system, avoiding any similarities to previous passwords to ward off brute-force attacks facilitated by Snake's keylogger functionality.
-
-
Extensively implement network segmentation to prevent the spread, especially to domain controllers, and limit the impact.
-
Deploy AgentX, to secure endpoint devices and ensure they are up-to-date, properly configured, and trigger alerts when disabled.
-
Continuously monitor critical organizational assets with a combination of tools such as Sysmon and the Logpoint Converged SIEM platform.
Final thoughts
In conclusion, despite the Snake malware's advanced sophistication and ability to operate covertly, it was ultimately susceptible to human errors and operational hazards, enabling its successful detection and eradication. The valuable insights shared in this blog can empower users to achieve similar outcomes by leveraging the provided detection.
By utilizing the comprehensive capabilities of the Logpoint Converged SIEM platform, which integrates SIEM, SOAR, and endpoint response functionalities, analysts can effectively investigate the Snake malware and implement appropriate countermeasures.
With the right tools and knowledge at hand, organizations can fortify their defenses against emerging threats like Snake, ensuring a secure and resilient digital environment.
** We can help you! For help with the suggested playbooks – design, development, and implementation – contact Global Services here.










